The operators of the Ducktail information and facts stealer have demonstrated a “relentless willingness to persist” and ongoing to update their malware as section of an ongoing monetarily driven marketing campaign.
“The malware is created to steal browser cookies and consider benefit of authenticated Facebook sessions to steal info from the victim’s Fb account,” WithSecure researcher Mohammad Kazem Hassan Nejad reported in a new analysis.
“The procedure in the end hijacks Facebook Enterprise accounts to which the sufferer has adequate access. The menace actor employs their acquired accessibility to run ads for monetary achieve.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Attributed to a Vietnamese threat actor, the Ducktail marketing campaign is intended to goal corporations in the digital promoting and advertising sectors which are active on the Facebook Advertisements and Small business platform.
Also qualified are men and women within just potential firms that are most likely to have substantial-amount accessibility to Fb Small business accounts. This incorporates advertising and marketing, media, and human means personnel.
The malicious exercise was very first documented by the Finnish cybersecurity firm in July 2022. The operation is believed to be underway considering that the 2nd 50 percent of 2021, whilst proof points to the threat actor staying lively as much back again as late 2018.
A subsequent investigation by Zscaler ThreatLabz final thirty day period uncovered a PHP edition of the malware distributed as installers for cracked software program. WithSecure, even so, stated the action has no connection by any means to the marketing campaign it tracks below the Ducktail moniker.
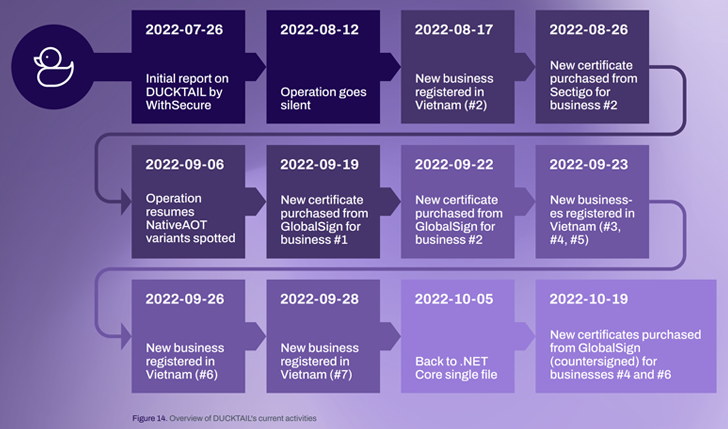
The hottest iteration of the malware, which resurfaced on September 6, 2022, immediately after the menace actor was compelled to halt its functions on August 12 in reaction to public disclosure, comes with a host of improvements included to circumvent detection.
An infection chains now commence with the shipping and delivery of archive information that contains spreadsheet files hosted on Apple iCloud and Discord through platforms like LinkedIn and WhatsApp, indicating diversification of the menace actor’s spear-phishing ways.
The Facebook Company account information gathered by the malware, which is signed working with electronic certificates acquired below the guise of seven diverse non-existent corporations, is exfiltrated utilizing Telegram.
“An intriguing shift that was observed with the latest campaign is that [the Telegram command-and-control] channels now include various administrator accounts, indicating that the adversary may possibly be working an affiliate program,” Nejad explained.
Uncovered this posting interesting? Follow THN on Fb, Twitter and LinkedIn to go through much more special content material we write-up.
Some components of this report are sourced from:
thehackernews.com


 Top Cyber Threats Facing E-Commerce Sites This Holiday Season
Top Cyber Threats Facing E-Commerce Sites This Holiday Season