Google has introduced plans to include support for quantum-resistant encryption algorithms in its Chrome browser, starting up with edition 116.
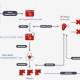
“Chrome will start off supporting X25519Kyber768 for establishing symmetric techniques in TLS, commencing in Chrome 116, and available at the rear of a flag in Chrome 115,” Devon O’Brien said in a publish posted Thursday.
Kyber was selected by the U.S. Department of Commerce’s National Institute of Expectations and Technology (NIST) as the candidate for normal encryption in a bid to tackle upcoming cyber attacks posed by the arrival of quantum computing. Kyber-768 is around the security equal of AES-192.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The encryption algorithm has already been adopted by Cloudflare, Amazon Web Services, and IBM.
X25519Kyber768 is a hybrid algorithm that brings together the output of X25519, an elliptic curve algorithm extensively utilised for crucial settlement in TLS, and Kyber-768 to build a robust session critical to encrypt TLS connections.
“Hybrid mechanisms such as X25519Kyber768 present the flexibility to deploy and exam new quantum-resistant algorithms whilst ensuring that connections are still shielded by an current safe algorithm,” O’Brien explained.
Though it’s envisioned to get several yrs, maybe even a long time, for quantum computer systems to pose critical dangers, specified types of encryption are prone to an attack called “harvest now, decrypt later” (aka retrospective decryption) in which information that is encrypted right now is harvested by menace actors in hopes of decrypting it later when cryptanalysis results in being easier thanks to technological breakthroughs.
This is in which quantum personal computers come in, as they are capable of efficiently executing specific computations in a method that can trivially defeat current cryptographic implementations.
“In TLS, even while the symmetric encryption algorithms that protect the data in transit are considered harmless in opposition to quantum cryptanalysis, the way that the symmetric keys are established is not,” O’Brien claimed.
“This indicates that in Chrome, the sooner we can update TLS to use quantum-resistant session keys, the faster we can secure consumer network targeted visitors towards long term quantum cryptanalysis.”

Enterprises that encounter network appliance incompatibility issues pursuing the rollout are suggested to disable X25519Kyber768 in Chrome using the PostQuantumKeyAgreementEnabled company policy, which is out there starting up in Chrome 116, as a non permanent evaluate.
The improvement arrives as Google said it is really modifying the release cadence of Chrome security updates from bi-weekly to weekly to minimize the attack window and address the increasing patch gap dilemma that allows danger actors additional time to weaponize released n-working day and zero-day flaws.
“Bad actors could possibly get edge of the visibility into these fixes and acquire exploits to utilize towards browser consumers who haven’t still acquired the deal with,” Amy Ressler from the Chrome Security Workforce stated. “That’s why we believe it is really genuinely critical to ship security fixes as soon as feasible, to decrease this ‘patch gap.'”
Identified this write-up fascinating? Abide by us on Twitter and LinkedIn to examine far more distinctive written content we post.
Some components of this post are sourced from:
thehackernews.com


 Researchers Shed Light on APT31’s Advanced Backdoors and Data Exfiltration Tactics
Researchers Shed Light on APT31’s Advanced Backdoors and Data Exfiltration Tactics