A hitherto undocumented risk actor working for virtually a 10 years and codenamed MoustachedBouncer has been attributed to cyber espionage attacks aimed at foreign embassies in Belarus.
“Considering that 2020, MoustachedBouncer has most possible been capable to accomplish adversary-in-the-center (AitM) attacks at the ISP degree, within Belarus, in order to compromise its targets,” ESET security researcher Matthieu Faou said, describing the team as skilled and advanced.
The adversary, lively because at least 2014, is assessed to be aligned with Belarusian interests, probable using a lawful interception procedure these types of as SORM to conduct its AitM attacks as properly as deploy disparate resources called NightClub and Disco.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
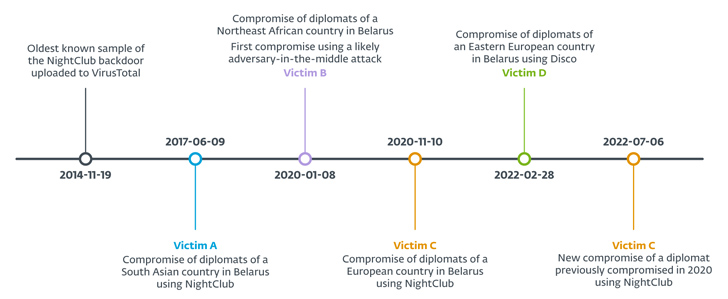
Each the Windows malware frameworks assistance extra spying plugins such as a screenshotter, an audio recorder, and a file stealer. The oldest sample of NightClub dates back again to November 19, 2014, when it was uploaded to VirusTotal from Ukraine.

Embassy staff members from four unique nations have been targeted considering the fact that June 2017: two from Europe, 1 from South Asia, and one particular from Northeast Africa. One particular of the European diplomats was compromised two times in November 2020 and July 2022. The names of the nations had been not discovered.
MoustachedBouncer is also considered to operate carefully with a different sophisticated persistent menace (APT) actor recognised as Winter season Vivern (aka TA473 or UAC-0114), which has a monitor file of hanging governing administration officers in Europe and the U.S.
The specific initial infection vector made use of to deliver NightClub is presently not known. The distribution of Disco, on the other hand, is attained by suggests of an AitM attack.
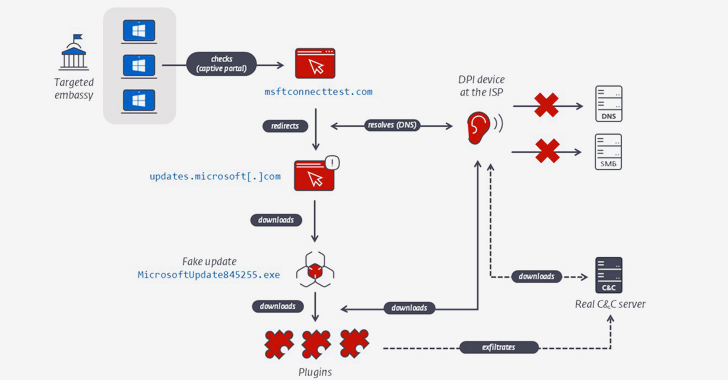
“To compromise their targets, MoustachedBouncer operators tamper with their victims’ internet obtain, probably at the ISP level, to make Windows imagine it truly is guiding a captive portal,” Faou explained. “For IP ranges targeted by MoustachedBouncer, the network site visitors is tampered at the ISP level, and the latter URL redirects to a seemingly legit, but fake, Windows Update URL.”
“Even though the compromise of routers in order to conduct AitM on embassy networks can’t be totally discarded, the presence of lawful interception abilities in Belarus suggests the visitors mangling is taking place at the ISP level somewhat than on the targets’ routers,” Fou claimed.
Two Belarusian internet assistance vendors (ISPs), viz Unitary Company A1 and Beltelecom, are suspected to be included in the marketing campaign, for every the Slovak cybersecurity corporation.
Victims who land on the bogus site are greeted with a message urging them to install critical security updates by clicking on a button. In performing so, a rogue Go-dependent “Windows Update” installer is downloaded to the equipment that, when executed, sets up a scheduled endeavor to operate one more downloader binary accountable for fetching additional plugins.
The add-ons extend on Disco’s functionality by capturing screenshots each and every 15 seconds, executing PowerShell scripts, and location up a reverse proxy.
A significant aspect of the plugins is the use of the Server Message Block (SMB) protocol for details exfiltration to command-and-management servers that are inaccessible more than the internet, creating the threat actor’s infrastructure really resilient.

Also applied in the January 2020 attack aimed at diplomats of a Northeast African place in Belarus is a C# dropper referred to as SharpDisco, which facilitates the deployment of two plugins by signifies of a reverse shell in buy to enumerate connected drives and exfiltrate files.
The NightClub framework also contains a dropper that, in transform, launches an orchestrator part to harvest information of curiosity and transmit them around the Basic Mail Transfer Protocol (SMTP) protocol. More recent variants of NightClub located in 2017 and 2020 also include a keylogger, audio recorder, screenshotter, and a DNS-tunneling backdoor.
“The DNS-tunneling backdoor (ParametersParserer.dll) uses a tailor made protocol to send out and obtain facts from a malicious DNS server,” Faou spelled out. “The plugin adds the data to exfiltrate as portion of the subdomain name of the area that is employed in the DNS ask for.”
The commands supported by the modular implant allow the risk actor to research for data files matching a precise pattern, read, copy, and take away data files, write to documents, duplicate directories, and produce arbitrary procedures.
It is really believed that NightClub is utilized in scenarios wherever visitors interception at the ISP degree isn’t really attainable since of anonymity-boosting mitigations this sort of as the use of an end-to-close encrypted VPN in which internet visitors is routed outdoors of Belarus.
“The main takeaway is that organizations in overseas nations in which the internet can not be trustworthy ought to use an finish-to-conclusion encrypted VPN tunnel to a reliable spot for all their internet website traffic in get to circumvent any network inspection units,” Faou explained.
Located this article appealing? Follow us on Twitter and LinkedIn to examine much more special content material we post.
Some components of this article are sourced from:
thehackernews.com

 Enhancing TLS Security: Google Adds Quantum-Resistant Encryption in Chrome 116
Enhancing TLS Security: Google Adds Quantum-Resistant Encryption in Chrome 116