A new malware marketing campaign has been exploiting the updating system of the eScan antivirus application to distribute backdoors and cryptocurrency miners like XMRig through a long-standing menace codenamed GuptiMiner targeting huge corporate networks.
Cybersecurity firm Avast reported the action is the function of a risk actor with achievable connections to a North Korean hacking group dubbed Kimsuky, which is also identified as Black Banshee, Emerald Sleet, and TA427.
“GuptiMiner is a remarkably refined danger that employs an intriguing an infection chain alongside with a pair of tactics that involve accomplishing DNS requests to the attacker’s DNS servers, carrying out sideloading, extracting payloads from innocent-hunting pictures, signing its payloads with a custom made reliable root anchor certification authority, between other people,” Avast stated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The intricate and elaborate an infection chain, at its main, leverages a security shortcoming in the update system of Indian antivirus seller eScan to propagate the malware by suggests of an adversary-in-the-center (AitM) attack.

Specially, it entails hijacking the updates by substituting the deal file with a destructive version by taking advantage of the reality that the downloads had been not signed and secured working with HTTPS. The issue, which went unnoticed for at least 5 many years, has been rectified as of July 31, 2023.
The rogue DLL (“updll62.dlz”) executed by the eScan software package aspect-masses a DLL (“variation.dll”) to activate a multi-stage sequence starting up with a PNG file loader that, in flip, employs malicious DNS servers to make contact with a command-and-manage (C2) server and fetch a PNG file with appended shellcode.
“GuptiMiner hosts their have DNS servers for serving accurate location domain addresses of C&C servers through DNS TXT responses,” scientists Jan Rubín and Milánek stated.
“As the malware connects to the malicious DNS servers right, the DNS protocol is fully divided from the DNS network. Thus, no reputable DNS server will at any time see the targeted visitors from this malware.”
The PNG file is then parsed to extract the shellcode, which is then dependable for executing a Gzip loader that is created to decompress yet another shellcode working with Gzip and execute it in a different thread.
The third-phase malware, dubbed Puppeteer, pulls all the strings, in the long run deploying the XMRig cryptocurrency miner and backdoors on the infected programs.
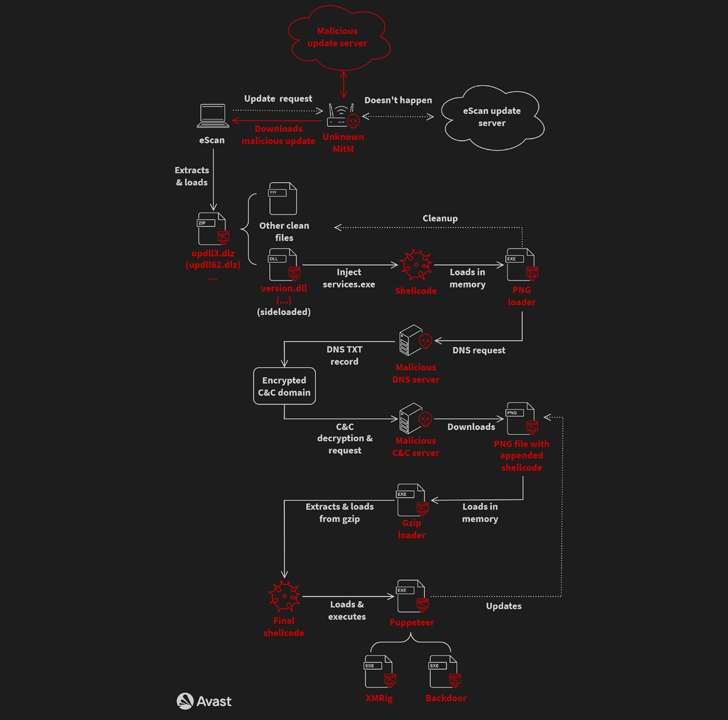
Avast explained it encountered two distinct styles of backdoors that arrive equipped with capabilities to allow lateral motion, take instructions from the menace actor, and supply supplemental elements as required.
“The 1st is an improved establish of PuTTY Link, providing SMB scanning of the community network and enabling lateral motion around the network to potentially vulnerable Windows 7 and Windows Server 2008 devices on the network,” the scientists defined.
“The 2nd backdoor is multi-modular, accepting instructions from the attacker to set up a lot more modules as nicely as concentrating on scanning for stored non-public keys and crypto wallets on the local process.”
The deployment of XMRig has been described as “unforeseen” for what is actually otherwise a complex and meticulously executed operation, increasing the probability that the miner acts as a distraction to protect against victims from exploring the genuine extent of the compromise.
GuptiMiner, recognized to be energetic considering that at least 2018, also would make use of many procedures like anti-VM and anti-debug tips, code virtualization, dropping the PNG loader throughout technique shutdown activities, storing payloads in Windows Registry, and incorporating a root certification to Windows’ certification store to make the PNG loader DLLs seem trustworthy.

The hyperlinks to Kimusky arrive from an information stealer that, whilst not dispersed by GuptiMiner or by way of the infection movement, has been made use of “throughout the complete GuptiMiner marketing campaign” and shares overlaps with a keylogger previously determined as used by the team.
It is really currently not distinct who the targets of the marketing campaign are, but GuptiMiner artifacts have been uploaded to VirusTotal from India and Germany as early as April 2018, with Avast telemetry info highlighting new bacterial infections probable originating from out-of-date eScan customers.
The results arrive as the Korean National Police Company (KNPA) termed out North Korean hacking crews this kind of as Lazarus, Andariel, and Kimsuky for focusing on the protection sector in the place and exfiltrating valuable info from some of them.
A report from the Korea Economic Day by day mentioned the threat actors penetrated the networks of 83 South Korean protection contractors and stole confidential data from about 10 of them from October 2022 to July 2023.
Found this article fascinating? Follow us on Twitter and LinkedIn to read through extra unique material we article.
Some pieces of this write-up are sourced from:
thehackernews.com


 CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers
CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers