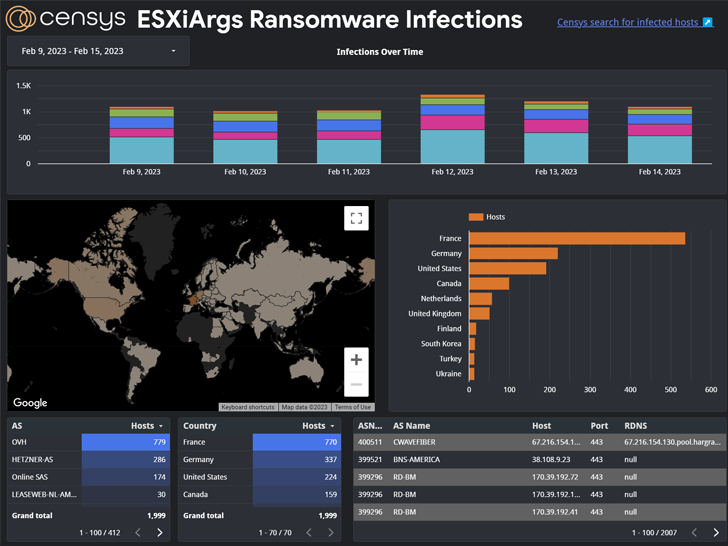
More than 500 hosts have been recently compromised en masse by the ESXiArgs ransomware pressure, most of which are situated in France, Germany, the Netherlands, the U.K., and Ukraine.
The findings arrive from attack surface management organization Censys, which discovered “two hosts with strikingly related ransom notes relationship again to mid-October 2022, just after ESXi variations 6.5 and 6.7 reached stop of lifestyle.”
The first set of infections dates back again to October 12, 2022, significantly previously than when the campaign began to obtain traction at the start off of February 2023. Then on January 31, 2023, the ransom notes on the two hosts are mentioned to have been updated with a revised version that matches the kinds made use of in the present-day wave.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
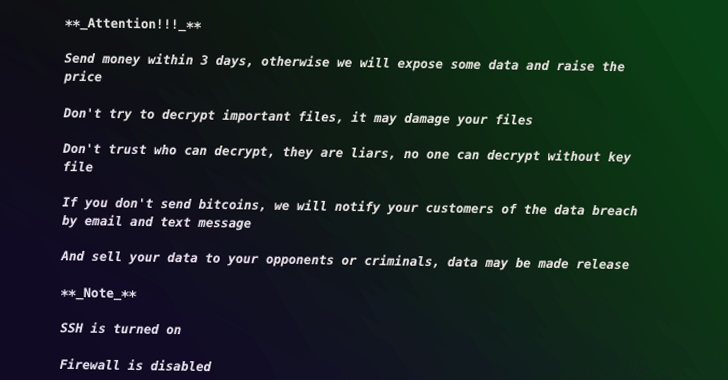
Some of the vital variations amongst the two ransom notes involve the use of an onion URL instead of a Tox chat ID, a Proton Mail deal with at the base of the take note, and a decrease ransom demand (1.05 Bitcoin vs. 2.09 Bitcoin).
“Each individual variant of the ransom notes from Oct 2022 by way of February 2023 are strikingly equivalent in wording to the notice of an previously ransomware variant, Cheerscrypt, which gained notoriety in early 2022,” researchers Mark Ellzey and Emily Austin reported.
It really is worth noting that ESXiArgs is suspected to be based mostly on the leaked Babuk ransomware code, which also spawned other variants these as Cheerscrypt and PrideLocker last yr.
The growth arrives much less than a week following the menace actors returned with a new variant that tweaks the encryption process and the ransom notice pursuing the launch of a decryptor to support recuperate contaminated units.
The U.S. Cybersecurity and Infrastructure Security Company (CISA) has due to the fact mentioned that the attackers are “possible focusing on conclusion-of-daily life ESXi servers or ESXi servers that do not have the accessible ESXi program patches used.”
“The vulnerability in VMware ESXi is a crystal clear reminder of the worth of keeping methods up to day with the most current security patches when also using solid perimeter protection,” Bitdefender’s Martin Zugec mentioned.
“Attackers you should not want to scour for new exploits or novel methods when they know that many businesses are vulnerable to older exploits owing, in aspect, to the lack of proper patch management and risk administration.”
The spike also coincides with an 87% year-around-calendar year enhance in ransomware attacks targeting industrial organizations in 2022, with 437 out of 605 attacks putting the manufacturing sector, for every a new report from Dragos, in element fueled by continued evolution in ransomware-as-a-services (RaaS) designs.
Info gathered by the industrial security company reveals that 189 ransomware attacks had been described in the remaining quarter of 2022 alone. Top specific verticals bundled manufacturing (143), meals and beverage (15), vitality (14), pharma (9), oil and fuel (4), and mining (1).
Located this posting fascinating? Comply with us on Twitter and LinkedIn to browse extra exceptional content we write-up.
Some areas of this write-up are sourced from:
thehackernews.com

 Experts Warn of Surge in Multipurpose Malware
Experts Warn of Surge in Multipurpose Malware