Many European clients of distinctive banking institutions are being focused by an Android banking trojan referred to as SpyNote as part of an intense campaign detected in June and July 2023.
“The adware is dispersed by means of email phishing or smishing campaigns and the fraudulent pursuits are executed with a blend of distant obtain trojan (RAT) capabilities and vishing attack,” Italian cybersecurity company Cleafy reported in a complex investigation launched Monday.
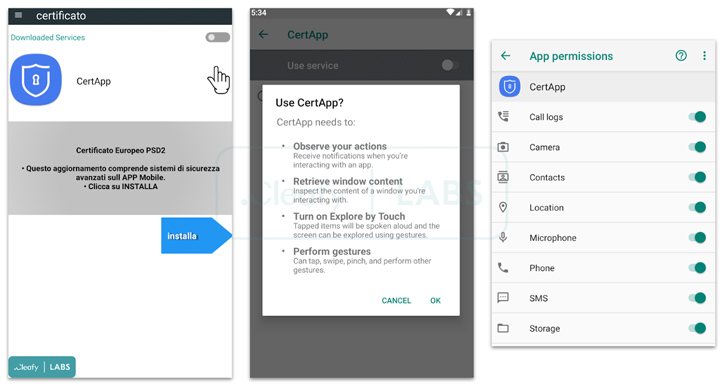
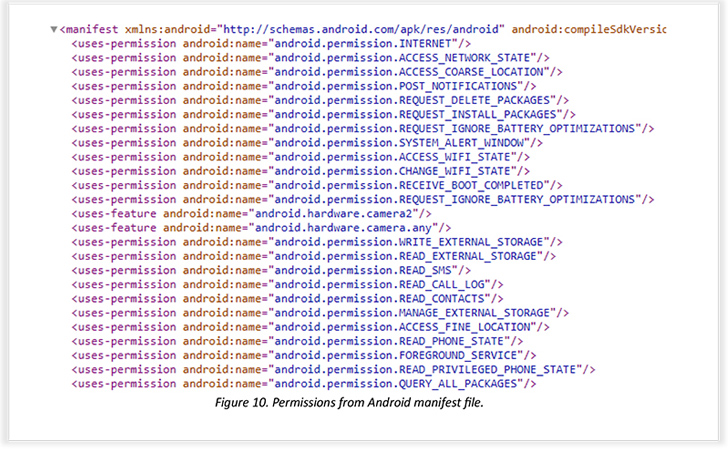
SpyNote, also known as SpyMax, is very similar to other Android banking Trojans in that it requires Android’s accessibility permissions in purchase to grant itself other vital permissions and assemble delicate facts from infected units. What helps make the malware pressure notable is its dual features as spyware and complete lender fraud.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The attack chains start with a bogus SMS message urging consumers to install a banking app by clicking on the accompanying connection, redirecting the target to the authentic TeamViewer QuickSupport application accessible on the Google Engage in Retailer.
“TeamViewer has been adopted by numerous [threat actors] to execute fraud operations as a result of social engineering attacks,” security researcher Francesco Iubatti reported. “In unique, the attacker phone calls the target, impersonating bank operators, and performs fraudulent transactions specifically on the victim’s machine.”
The concept is to use TeamViewer as a conduit to achieve remote entry to the victim’s phone, and stealthily set up the malware. The several types of details harvested by SpyNote incorporate geolocation information, keystrokes, monitor recordings, and SMS messages to bypass SMS-centered two-factor authentication (2FA).
The disclosure arrives as the hack-for-employ the service of operation recognized as Bahamut has been linked to a new campaign focusing on people today in the Center East and South Asia regions with the objective of putting in a dummy chat application named SafeChat that conceals an Android malware dubbed CoverIm.
Delivered to victims by using WhatsApp, the application homes identical attributes as that of SpyNote, requesting for accessibility permissions and some others to accumulate contact logs, contacts, data files, place, SMS messages, as very well as set up supplemental apps and steal info from Facebook Messenger, imo, Signal, Telegram, Viber, and WhatsApp.

Cyfirma, which uncovered the latest activity, claimed the practices used by this threat actor overlap with a different nation-condition actor regarded as the DoNot Group, which was not long ago observed employing rogue Android applications published to the Perform Store to infect folks situated in Pakistan.
While the specific details of the social engineering part of the attack is unclear, Bahamut is recognised to rely on fictitious personas on Fb and Instagram, pretending to be tech recruiters at substantial tech providers, journalists, students, and activists to trick unwitting buyers into downloading malware on their equipment.
“Bahamut applied a array of tactics to host and distribute malware, including jogging a network of malicious domains purporting to present secure chat, file-sharing, connectivity providers, or information programs,” Meta unveiled in May well 2023. “Some of them spoofed the domains of regional media stores, political businesses, or reputable application merchants, probable to make their backlinks surface a lot more legit.”
Found this short article attention-grabbing? Stick to us on Twitter and LinkedIn to read far more unique material we put up.
Some components of this posting are sourced from:
thehackernews.com


 What is Data Security Posture Management (DSPM)?
What is Data Security Posture Management (DSPM)?