Cybersecurity researchers have unearthed a Python variant of a stealer malware NodeStealer that’s geared up to absolutely just take in excess of Fb business accounts as perfectly as siphon cryptocurrency.
Palo Alto Network Device 42 reported it detected the earlier undocumented strain as component of a campaign that commenced in December 2022.
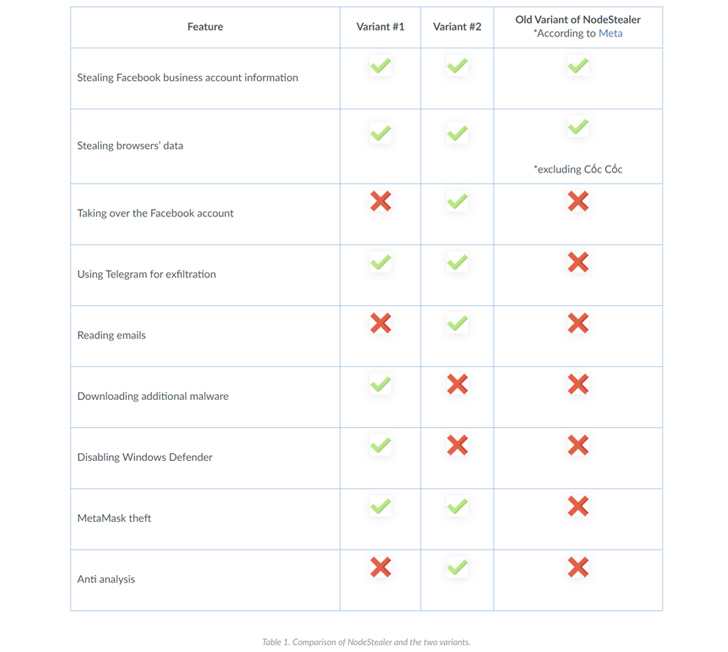
NodeStealer was first uncovered by Meta in Could 2023, describing it as a stealer capable of harvesting cookies and passwords from web browsers to compromise Fb, Gmail, and Outlook accounts. When the prior samples were created in JavaScript, the latest variations are coded in Python.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“NodeStealer poses fantastic risk for the two persons and corporations,” Unit 42 researcher Lior Rochberger explained. “In addition to the direct effects on Fb business enterprise accounts, which is mainly money, the malware also steals qualifications from browsers, which can be applied for even more attacks.”
The attacks start out with bogus messages on Fb that purportedly claim to offer cost-free “professional” funds monitoring Microsoft Excel and Google Sheets templates, tricking victims to obtain a ZIP archive file hosted on Google Generate.

The ZIP file embeds in just it the stealer executable that, besides capturing Facebook business enterprise account information, is designed to download more malware these as BitRAT and XWorm in the type of ZIP documents, disable Microsoft Defender Antivirus, and have out crypto theft by utilizing MetaMask qualifications from Google Chrome, Cốc Cốc, and Courageous web browsers.
The downloads are achieved by usually means of a User Account Handle (UAC) bypass system that employs the fodhelper.exe to execute PowerShell scripts that retrieve the ZIP information from a remote server.
It’s value noting that the FodHelper UAC bypass approach has also been adopted by financially motivated menace actors at the rear of the Casbaneiro banking malware to attain elevated privileges around infected hosts.
Device 42 stated it more spotted an upgraded Python variant of NodeStealer that goes beyond credential and crypto theft by applying anti-analysis attributes, parsing email messages from Microsoft Outlook, and even attempting to get about the related Fb account.
At the time the important information and facts is gathered, the documents are exfiltrated by means of the Telegram API, right after which they are deleted from the equipment to erase the path.

NodeStealer also joins the likes of malware like Ducktail that are aspect of a escalating pattern of Vietnamese menace actors searching to crack into Facebook business accounts for promotion fraud and propagating malware to other users on the social media platform.
The progress comes as menace actors have been observed leveraging WebDAV servers to deploy BATLOADER, which is then utilised to distribute XWorm as part of a multi-phase phishing attack.
“Facebook organization account house owners are inspired to use robust passwords and help multi-factor authentication,” Rochberger explained. “Just take the time to provide education for your business on phishing methods, primarily modern, targeted approaches that play off current occasions, small business requirements and other appealing subject areas.”
Found this write-up fascinating? Comply with us on Twitter and LinkedIn to browse additional exceptional material we post.
Some pieces of this post are sourced from:
thehackernews.com

 European Bank Customers Targeted in SpyNote Android Trojan Campaign
European Bank Customers Targeted in SpyNote Android Trojan Campaign