Cybersecurity scientists have shared particulars about a now-patched security flaw in Windows MSHTML system that could be abused to bypass integrity protections on focused equipment.
The vulnerability, tracked as CVE-2023-29324 (CVSS rating: 6.5), has been described as a security characteristic bypass. It was dealt with by Microsoft as section of its Patch Tuesday updates for May perhaps 2023.
Akamai security researcher Ben Barnea, who found out and noted the bug, famous that all Windows variations are afflicted, but pointed out Microsoft, Exchange

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
servers with the March update omit the susceptible element.

“An unauthenticated attacker on the internet could use the vulnerability to coerce an Outlook shopper to hook up to an attacker-managed server,” Barnea mentioned in a report shared with The Hacker Information.
“This benefits in NTLM credentials theft. It is a zero-click on vulnerability, indicating it can be triggered with no consumer interaction.”
It really is also worth noting that CVE-2023-29324 is a bypass for a deal with Microsoft place in put in March 2023 to resolve CVE-2023-23397, a critical privilege escalation flaw in Outlook that the business said has been exploited by Russian danger actors in attacks aimed at European entities given that April 2022.
Forthcoming WEBINARLearn to Halt Ransomware with True-Time Defense
Be part of our webinar and master how to stop ransomware attacks in their tracks with authentic-time MFA and assistance account safety.
Help save My Seat!
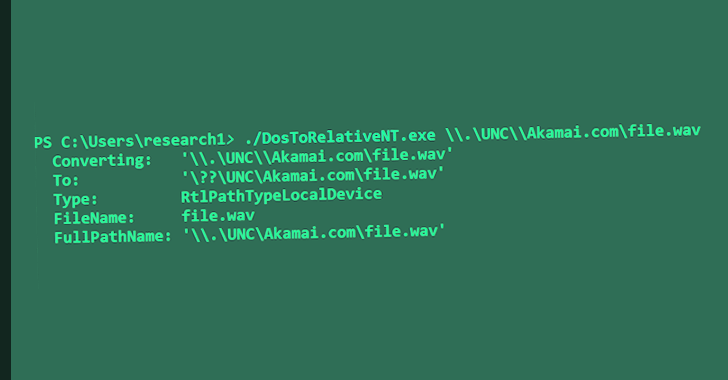
Akamai stated the issue stems from intricate handling of paths in Windows, thus letting a risk actor to craft a malicious URL that can sidestep internet security zone checks.
“This vulnerability is still another illustration of patch scrutinizing foremost to new vulnerabilities and bypasses,” Barnea claimed. “It is a zero-simply click media parsing attack surface that could potentially include critical memory corruption vulnerabilities.”
In purchase to stay totally safeguarded, Microsoft is further recommending end users to put in Internet Explorer Cumulative updates to deal with vulnerabilities in the MSHTML platform and scripting engine.
Uncovered this post fascinating? Comply with us on Twitter and LinkedIn to browse extra exceptional content material we write-up.
Some elements of this short article are sourced from:
thehackernews.com

 Sophisticated DownEx Malware Campaign Targeting Central Asian Governments
Sophisticated DownEx Malware Campaign Targeting Central Asian Governments