Federal government organizations in Central Asia are the focus on of a advanced espionage marketing campaign that leverages a previously undocumented strain of malware dubbed DownEx.
Bitdefender, in a report shared with The Hacker Information, reported the exercise remains energetic, with proof likely pointing to the involvement of Russia-primarily based danger actors.
The Romanian cybersecurity organization claimed it first detected the malware in a extremely targeted attack aimed at foreign government establishments in Kazakhstan in late 2022. Subsequently, a further attack was noticed in Afghanistan.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The use of a diplomat-themed lure doc and the campaign’s emphasis on facts exfiltration indicates the involvement of a state-sponsored group, although the correct id of the hacking outfit continues to be indeterminate at this stage.

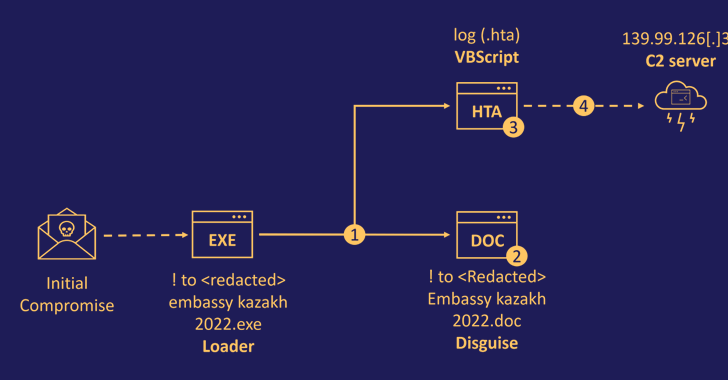
The preliminary intrusion vector for the campaign is suspected to be a spear-phishing email bearing a booby-trapped payload, which is a loader executable that masquerades as a Microsoft Word file.
Opening the attachment potential customers to the extraction of two information, which include a decoy document that’s displayed to the target although a malicious HTML application (.HTA) with embedded VBScript code operates in the track record.
The HTA file, for its part, is developed to establish call with a distant command-and-command (C2) server to retrieve a future-phase payload. Whilst the actual character of the malware is not unknown, it is mentioned to be a backdoor to build persistence.
The attacks are also notable for using a selection of tailor made applications for carrying out write-up-exploitation things to do. This consists of –
- Two C/C++-primarily based binaries (wnet.exe and utility.exe) to enumerate all the methods on a network,
- A Python script (assistance.py) to set up an infinite conversation loop with the C2 server and get guidelines to steal documents with certain extensions, delete information created by other malware, and capture screenshots, and
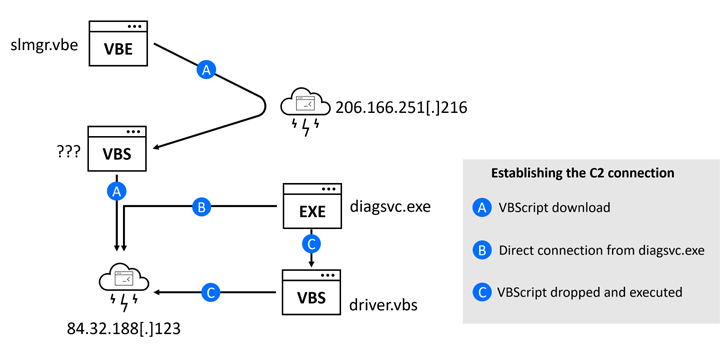
- A C++-based mostly malware (diagsvc.exe aka DownEx) that is mainly built to exfiltrate files to the C2 server
Approaching WEBINARLearn to Halt Ransomware with Authentic-Time Safety
Join our webinar and master how to end ransomware attacks in their tracks with serious-time MFA and company account safety.
Help save My Seat!
Two other variants of DownEx have also been earthed, the initially of which executes an intermediate VBScript to harvest and transmit the documents in the form of a ZIP archive.
The other version, which is downloaded by means of a VBE script (slmgr.vbe) from a remote server, eschews C++ for VBScript, but retains the same functionality as the previous.
“This is a fileless attack – the DownEx script is executed in memory and by no means touches the disk,” Bitdefender reported. “This attack highlights the sophistication of a present day cyberattack. Cybercriminals are obtaining new methods for building their attacks far more dependable.”
Discovered this report appealing? Comply with us on Twitter and LinkedIn to go through extra exceptional material we submit.
Some sections of this article are sourced from:
thehackernews.com

 Why Honeytokens Are the Future of Intrusion Detection
Why Honeytokens Are the Future of Intrusion Detection