An lively espionage marketing campaign has been attributed to the risk actor recognised as Molerats that abuses legit cloud products and services like Google Push and Dropbox to host malware payloads and for command-and-regulate and the exfiltration of data from targets across the Middle East.
The cyber offensive is thought to have been underway due to the fact at the very least July 2021, according to cloud-dependent information and facts security organization Zscaler, continuing past attempts by the hacking group to carry out reconnaissance on the goal hosts and plunder delicate data.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Molerats, also tracked as TA402, Gaza Hackers Staff, and Excessive Jackal, is an state-of-the-art persistent threat (APT) team that’s mostly targeted on entities working in the Center East. Attack exercise affiliated with the actor has leveraged geopolitical and armed forces themes to entice customers to open Microsoft Business office attachments and click on on malicious back links.
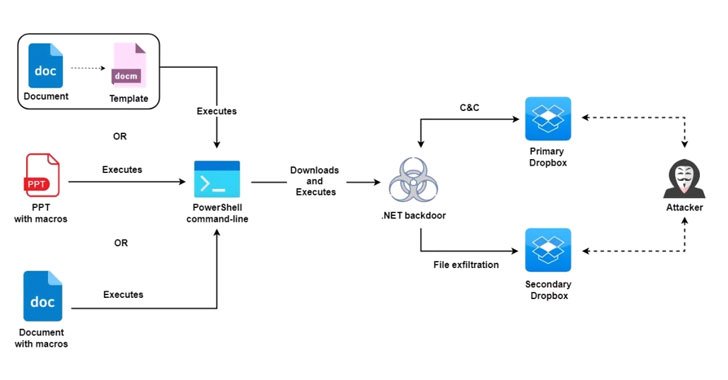
The most up-to-date campaign in-depth by Zscaler is no various in that it makes use of decoy themes linked to ongoing conflicts between Israel and Palestine to supply a .NET backdoor on infected units that, in convert, abuses the Dropbox API to build communications with an adversary-controlled server and transmit knowledge.
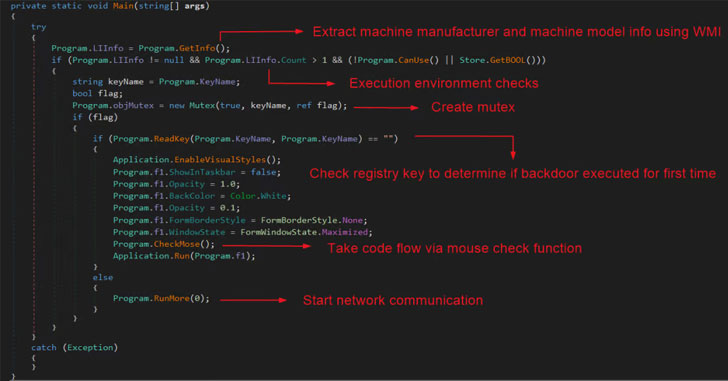
The implant, which works by using certain command codes to commandeer the compromised machine, supports abilities to take snapshots, list and add data files in applicable directories, and run arbitrary commands. Investigating the attack infrastructure, the scientists stated they found at minimum 5 Dropbox accounts applied for this function.
“The targets in this marketing campaign had been selected precisely by the threat actor and they involved critical members of banking sector in Palestine, individuals relevant to Palestinian political get-togethers, as well as human rights activists and journalists in Turkey,” Zscaler ThreatLabz scientists Sahil Antil and Sudeep Singh stated.
Located this report intriguing? Abide by THN on Facebook, Twitter and LinkedIn to study a lot more exclusive material we post.
Some parts of this report are sourced from:
thehackernews.com


 Hackers Planted Secret Backdoor in Dozens of WordPress Plugins and Themes
Hackers Planted Secret Backdoor in Dozens of WordPress Plugins and Themes