The infamous cybercrime syndicate recognized as FIN7 has been linked to a spear-phishing marketing campaign targeting the U.S. automotive field to deliver a recognized backdoor identified as Carbanak (aka Anunak).
“FIN7 determined employees at the corporation who labored in the IT division and had greater amounts of administrative legal rights,” the BlackBerry investigation and intelligence group stated in a new produce-up.
“They employed the entice of a no cost IP scanning resource to run their effectively-regarded Anunak backdoor and acquire an initial foothold making use of residing off the land binaries, scripts, and libraries (LOLBAS).”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

FIN7, also recognized as Carbon Spider, Elbrus, Gold Niagara, ITG14, Sangria Tempest, is a very well-acknowledged financially enthusiastic e-crime group that has a track history of putting a extensive assortment of market verticals to deliver malware able of thieving information and facts from issue-of-sale (PoS) methods since 2012.
In recent yrs, the threat actor has transitioned to conducting ransomware functions, providing a variety of strains like Black Basta, Cl0p, DarkSide, and REvil. Two Ukrainian customers of the group, Fedir Hladyr and Andrii Kolpakov, have been sentenced to jail in the U.S. to date.
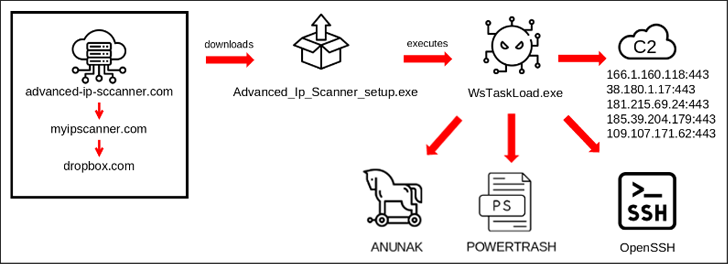
The hottest campaign found out by BlackBerry in late 2023 starts with a spear-phishing email that embeds a booby-trapped connection pointing to a bogus web site (“state-of-the-art-ip-sccanner[.]com”) that masquerades as Highly developed IP Scanner.
“This faux web page redirected to ‘myipscanner[.]com,’ which in turn redirected to an attacker-owned Dropbox that downloaded the malicious executable WsTaskLoad.exe on to the victim’s machine,” the Canadian cybersecurity organization explained.

The binary, for its part, initiates a multi-stage procedure that in the long run leads to the execution of Carbanak. It can be also created to deliver extra payloads these types of as POWERTRASH and set up persistence by putting in OpenSSH for distant accessibility.
It truly is at this time not recognised if the threat actors were being preparing on deploying ransomware, as the infected method was detected early on and removed from the network prior to it could access the lateral movement phase.
Though the target of the attack was a “large multinational automotive company” based mostly in the U.S., BlackBerry stated it observed several comparable malicious domains on the very same company, indicating that it may perhaps be part of a wider campaign by FIN7.
To mitigate the pitfalls posed by these kinds of threats, it really is proposed that corporations be on the lookout for phishing attempts, help multi-factor authentication (MFA), maintain all computer software and systems up-to-day, and watch for strange login attempts.
Located this short article interesting? Comply with us on Twitter and LinkedIn to browse far more distinctive articles we submit.
Some areas of this posting are sourced from:
thehackernews.com


 Recover from Ransomware in 5 Minutes—We will Teach You How!
Recover from Ransomware in 5 Minutes—We will Teach You How!