Tremendous Minimal RPO with Continual Details Security:
Dial Back to Just Seconds Prior to an Attack
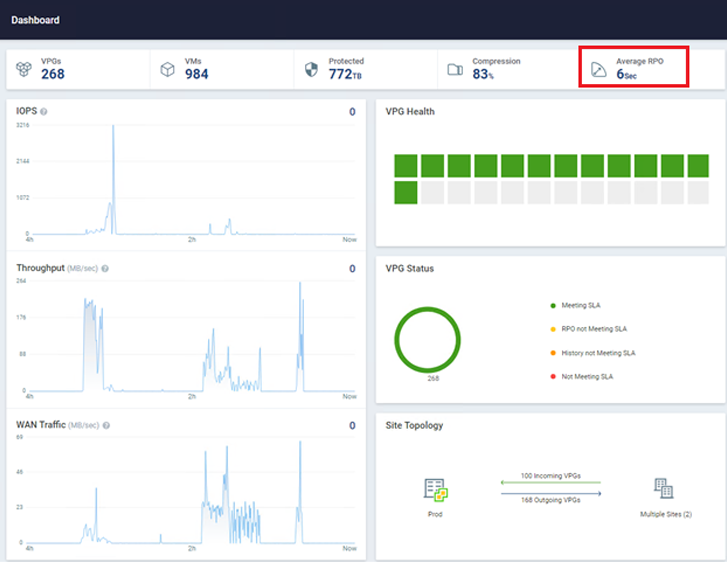
Zerto, a Hewlett Packard Organization firm, can help you detect and recover from ransomware in around serious-time. This solution leverages continual information defense (CDP) to make certain all workloads have the least expensive recovery place goal (RPO) doable. The most beneficial issue about CDP is that it does not use snapshots, agents, or any other periodic knowledge safety methodology. Zerto has no influence on production workloads and can obtain RPOs in the region of 5-15 seconds across hundreds of digital equipment at the same time. For illustration, the natural environment in the picture below has just about 1,000 VMs becoming shielded with an ordinary RPO of just six seconds!

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Software-Centric Defense:
Group Your VMs to Obtain Software-Amount Regulate
You can defend your VMs with the Zerto software-centric tactic using Virtual Defense Groups (VPGs). This logical grouping of VMs makes sure that your total application stacks can be recovered in a single cohesive unit, with checkpoints taken only seconds aside from the exact similar level in time throughout multiple VMs in the team.
Authentic-Time, In-Line Encryption Detection:
Get Early Warning When an Attack Takes place
Zerto can detect feasible ransomware attacks in true-time, unlike other solutions that require to wait for a backup to total prior to scanning the facts. Zerto scans knowledge in-line in true-time as it is staying replicated, offering you the earliest warning sign of a probable cyberattack occurring within your ecosystem.
Find out Extra about Actual-Time Encryption with Zerto.
Let’s consider a appear at what a ransomware attack and Zerto restoration glimpse like.
In a true-existence cyberattack state of affairs, you wouldn’t knowingly encrypt your information. It is apparent that the file server in this graphic has been infected with ransomware, which encrypted the information hosted in just it.
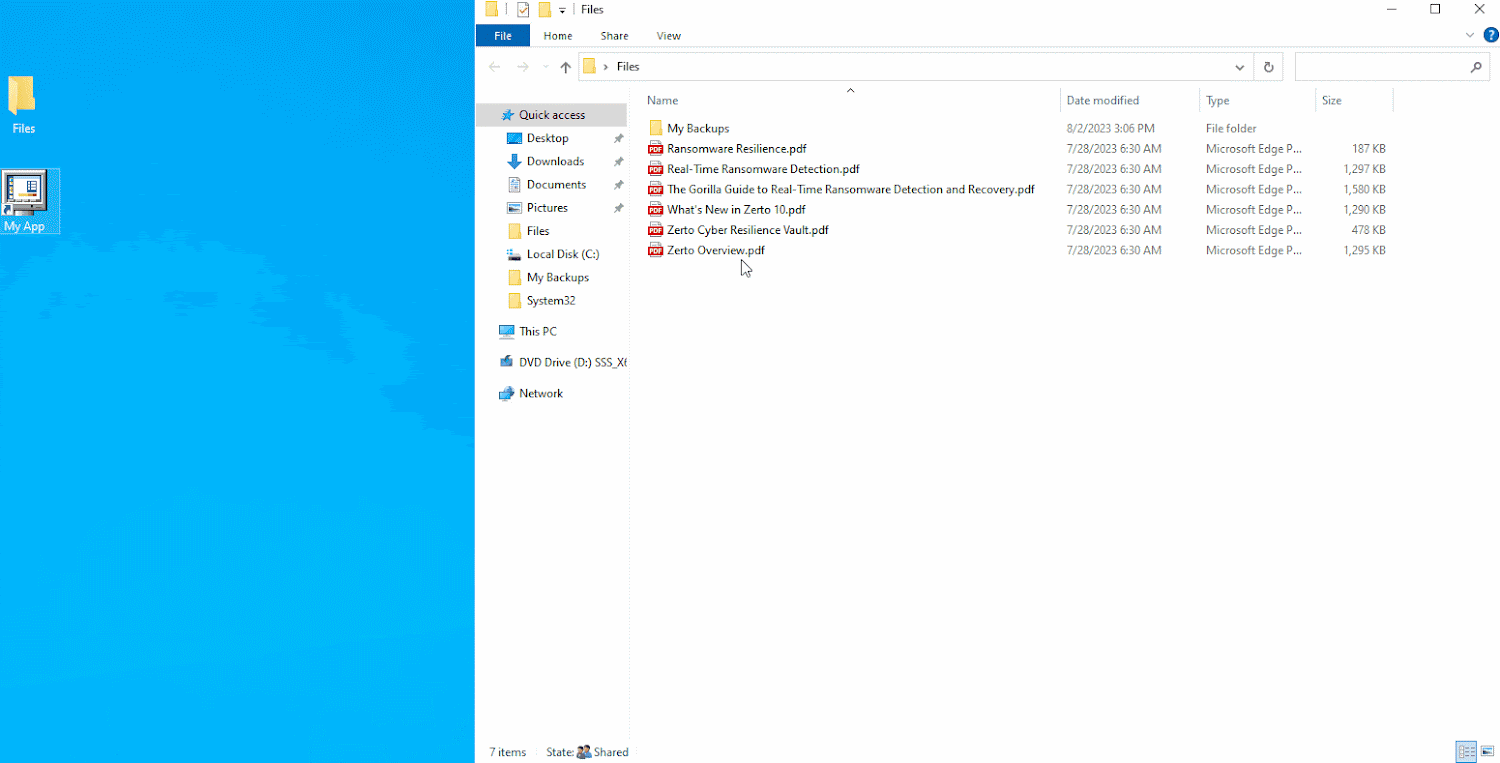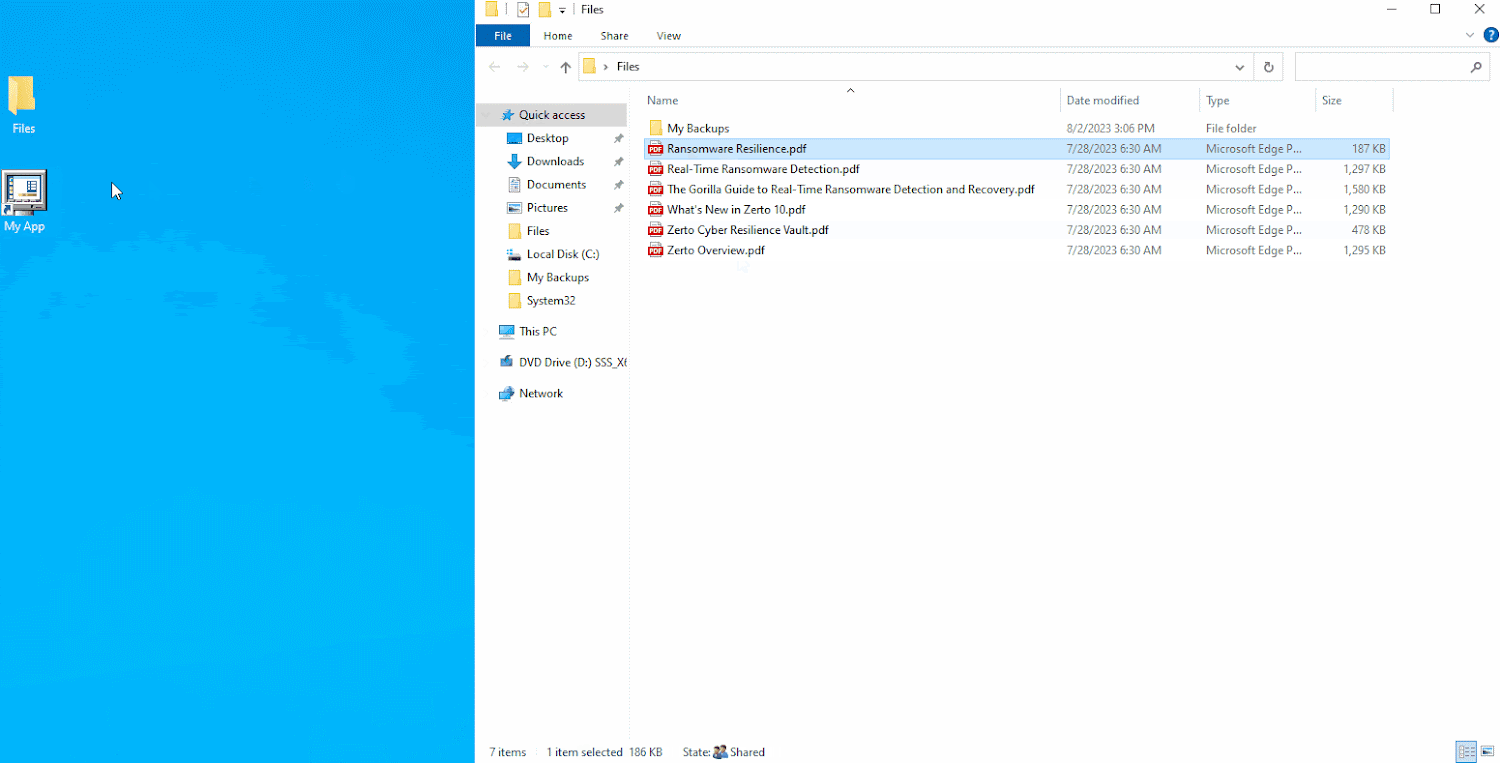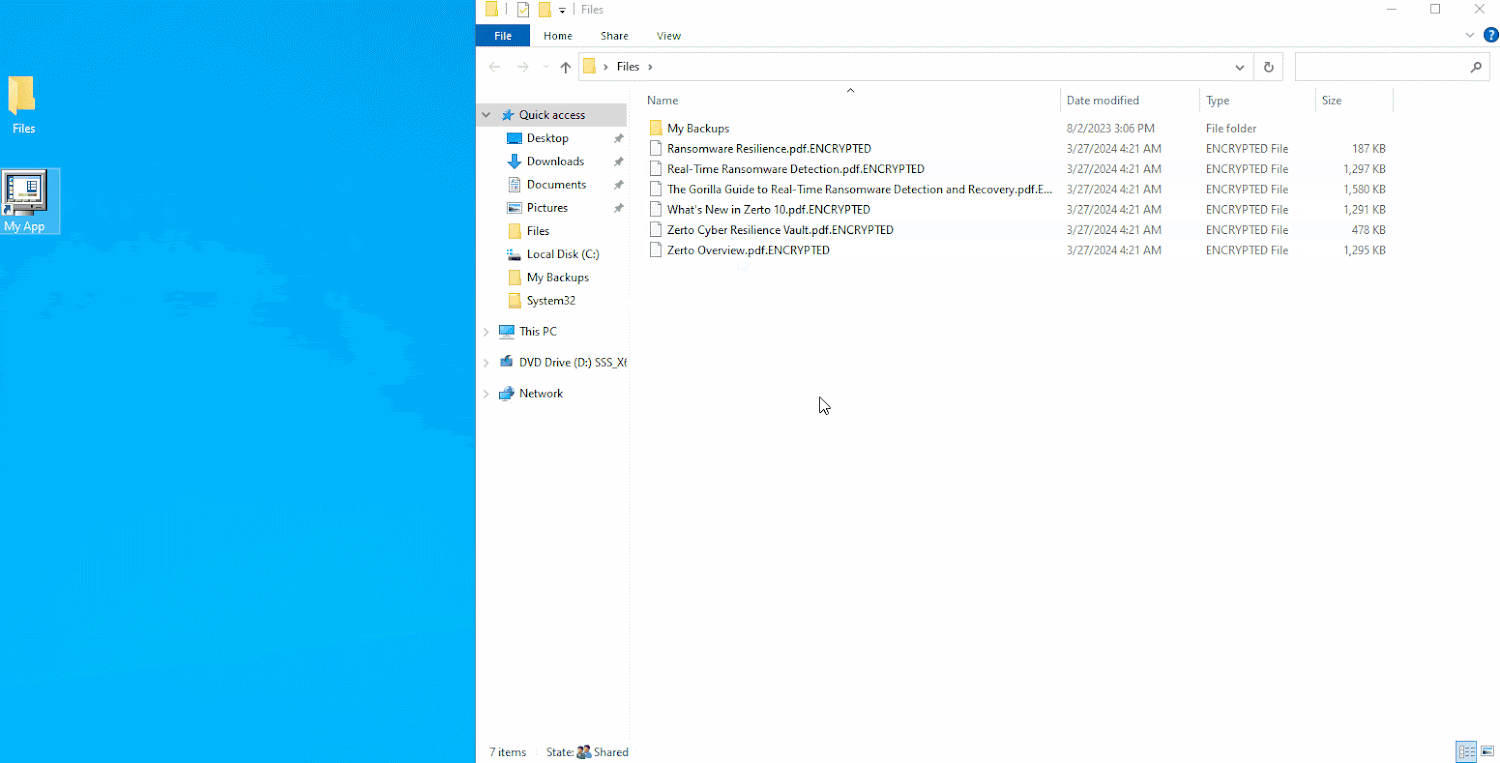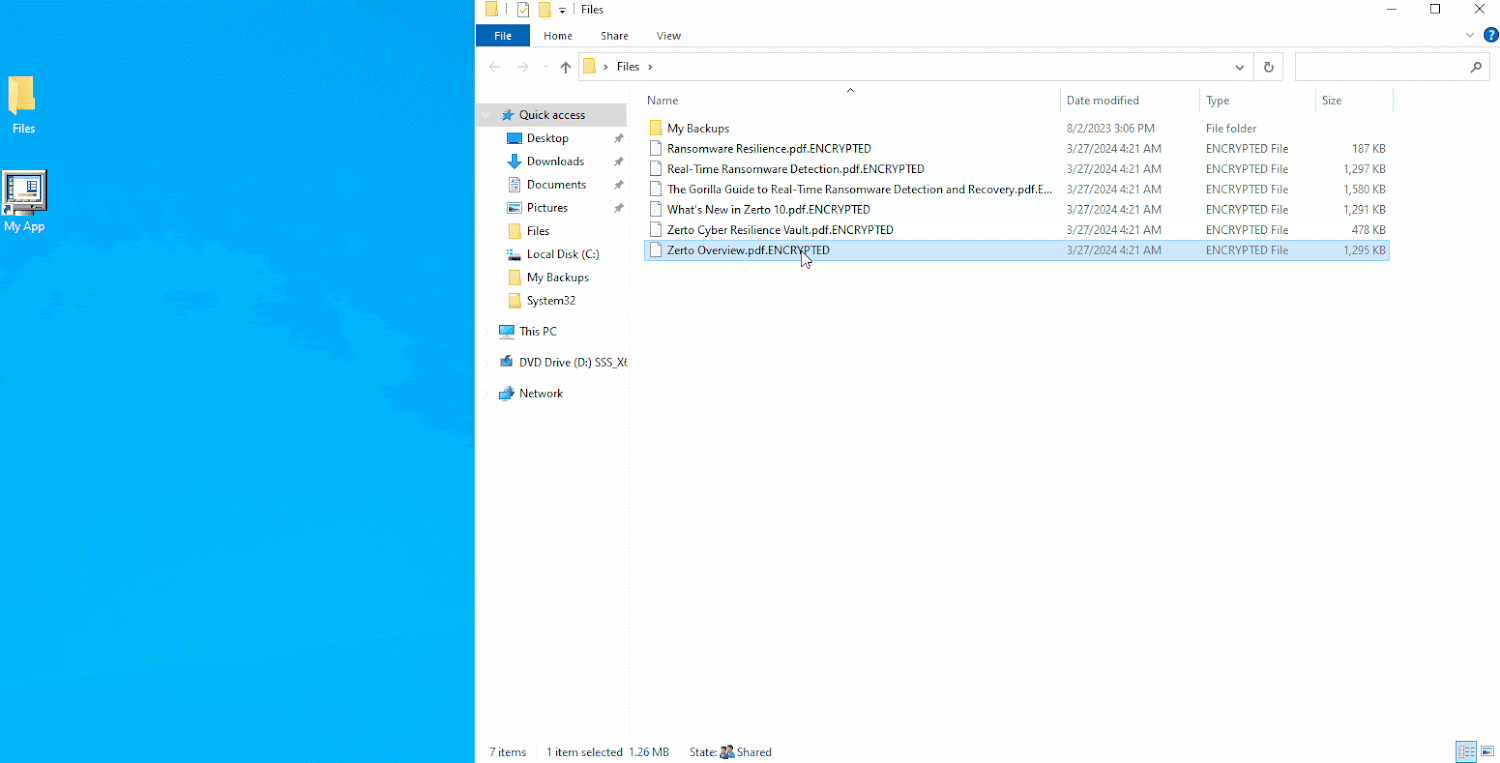
Soon after a ransomware attack, files will all be encrypted and can not be employed.
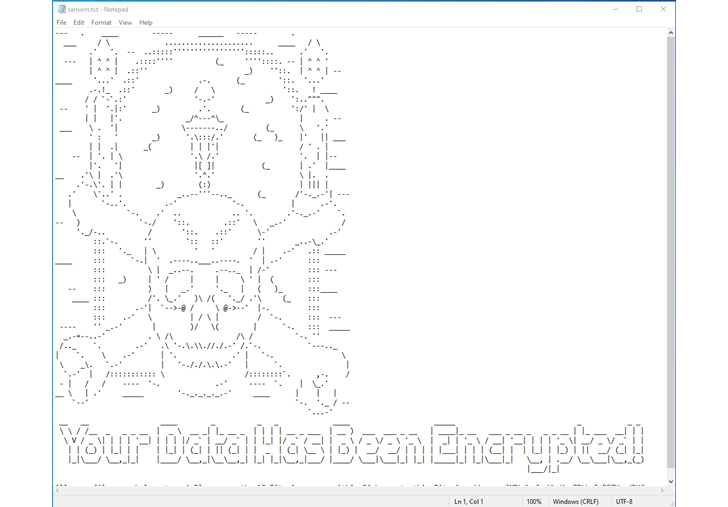
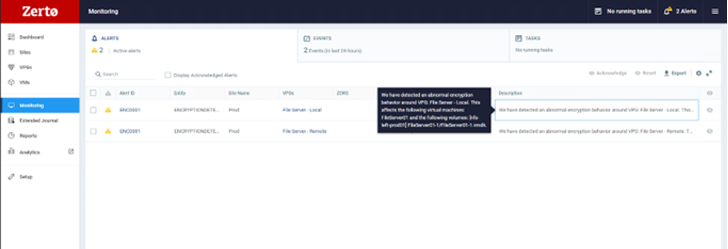
Making use of Zerto, early in a cyberattack, you may see a activated warning in your Zerto console, indicating likely suspicious action on your VM. You can drill down to see the exact disk the anomalous activity is currently being produced from, enabling you to rapidly establish infected machines, limit blast radius, and develop a timeline of gatherings to help in investigations and forensics submit-recovery, as shown in this picture.
Instantaneous File Stage Recovery:
Restore an Application or a VM—or Even Drill Down to a Solitary File
On an attack, you can expect to acquire automatic alerts by way of email or notifications from the Zerto extensible APIs, enabling you to choose motion quickly. You can restore information directly back again into the VM in real time, from only seconds before the encryption celebration, making certain minimal details loss.
The graphic under shows how. First, decide on Restore, then Files.
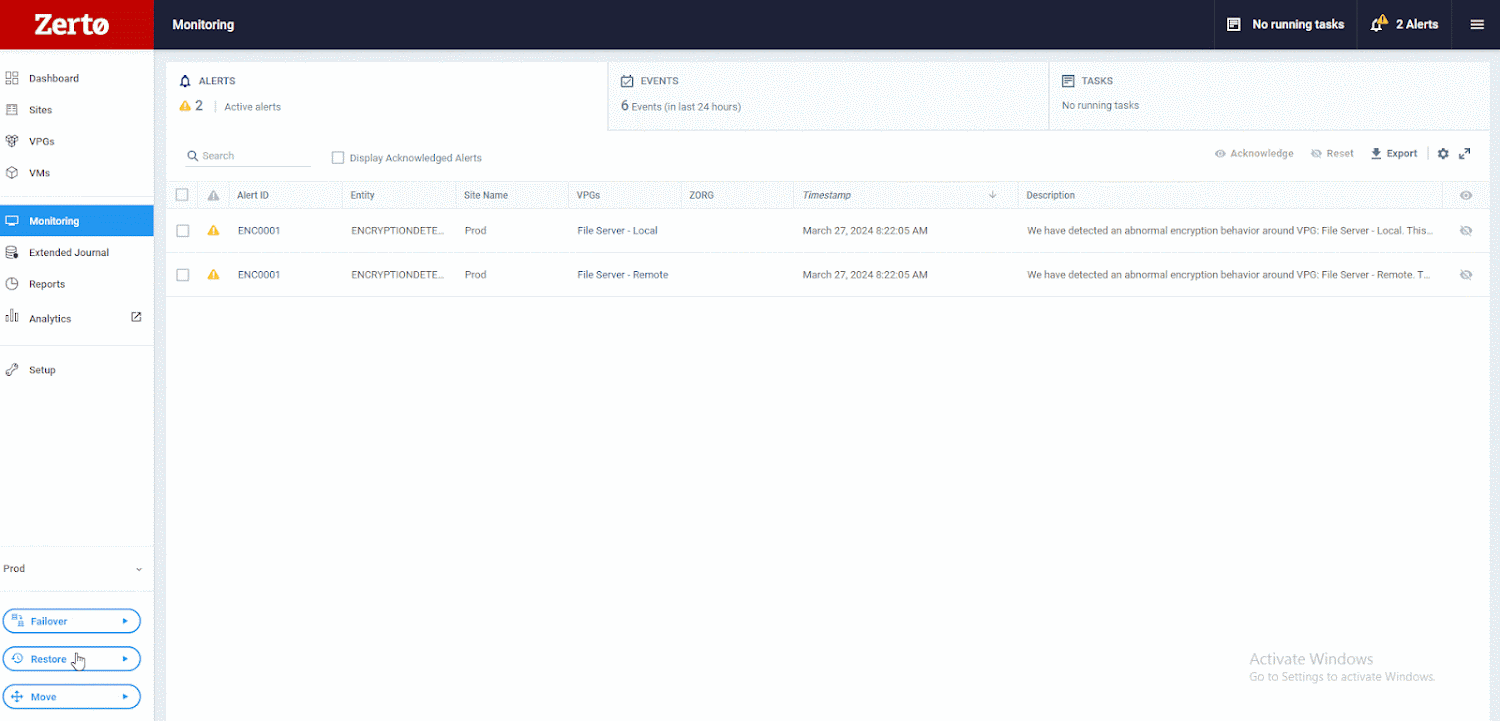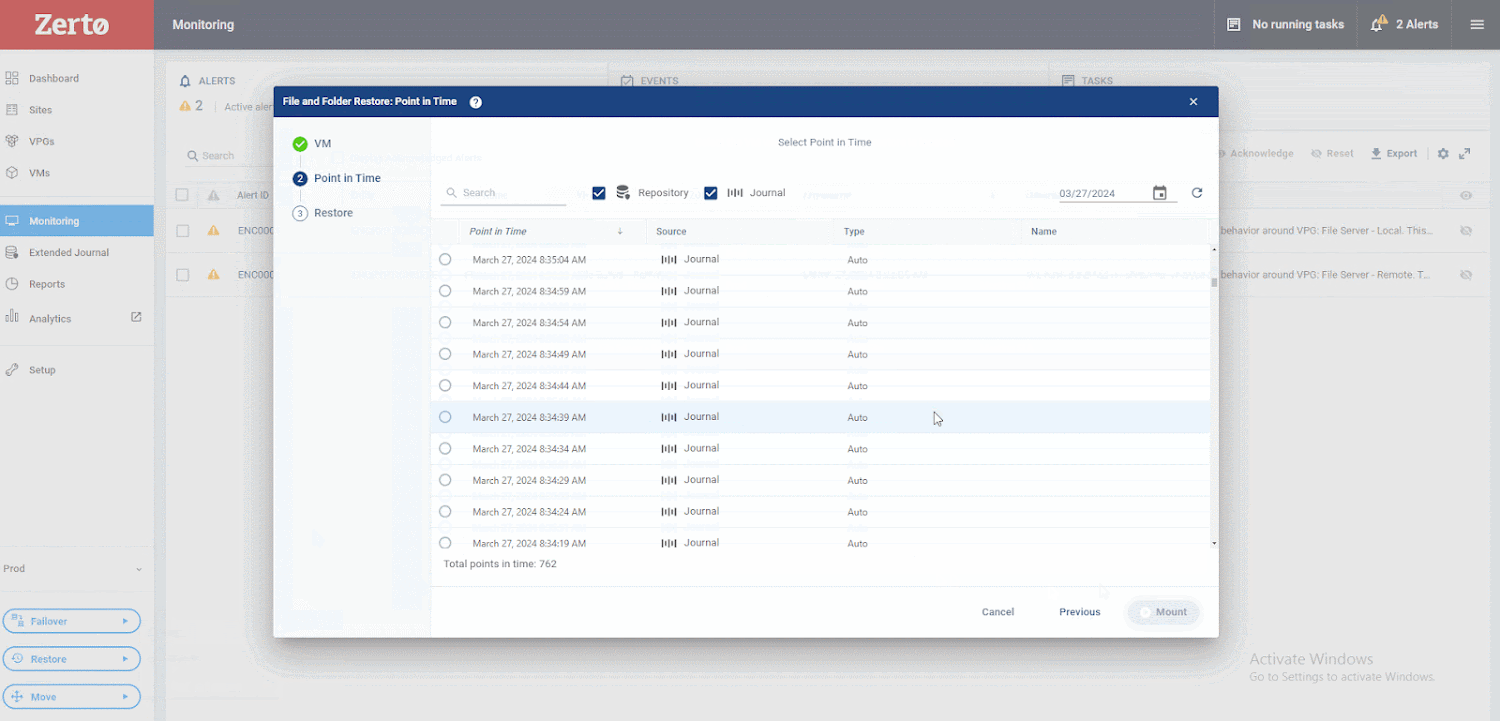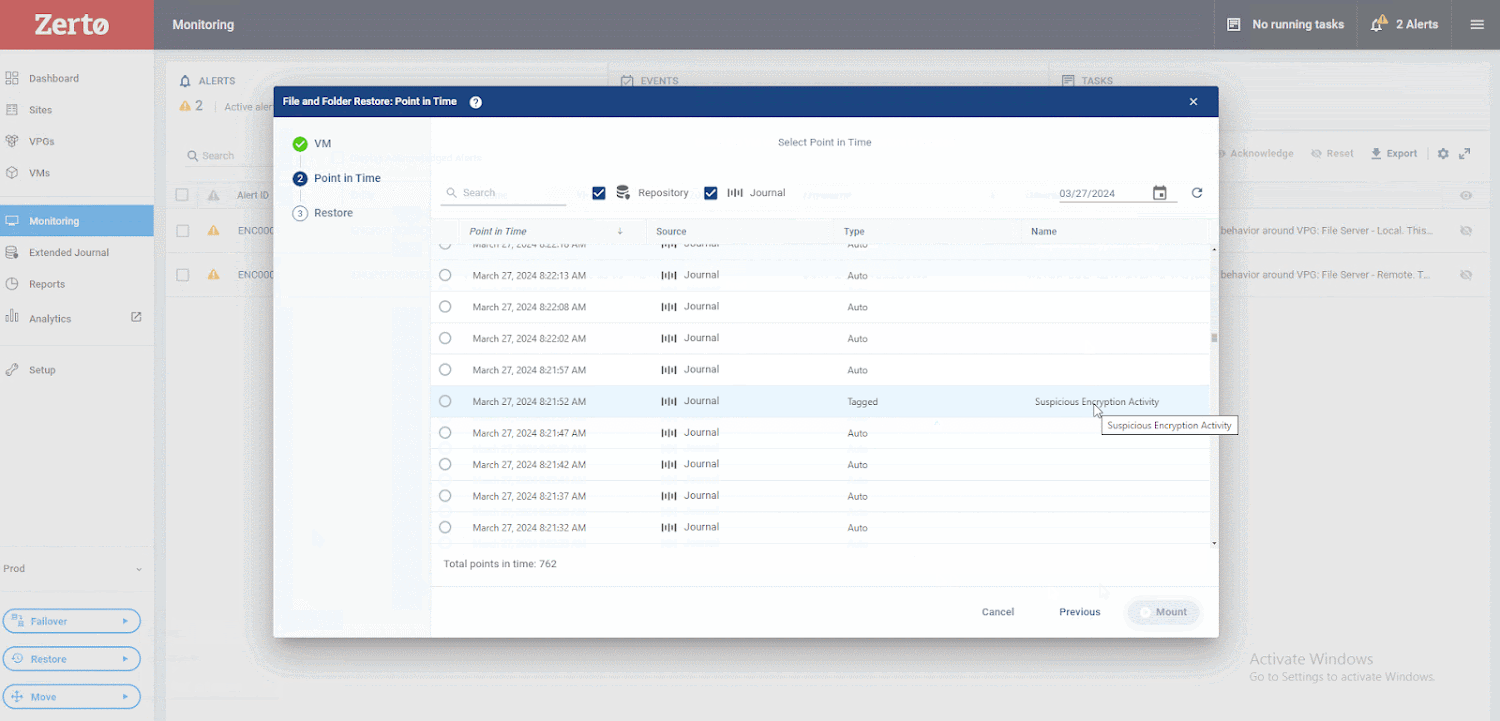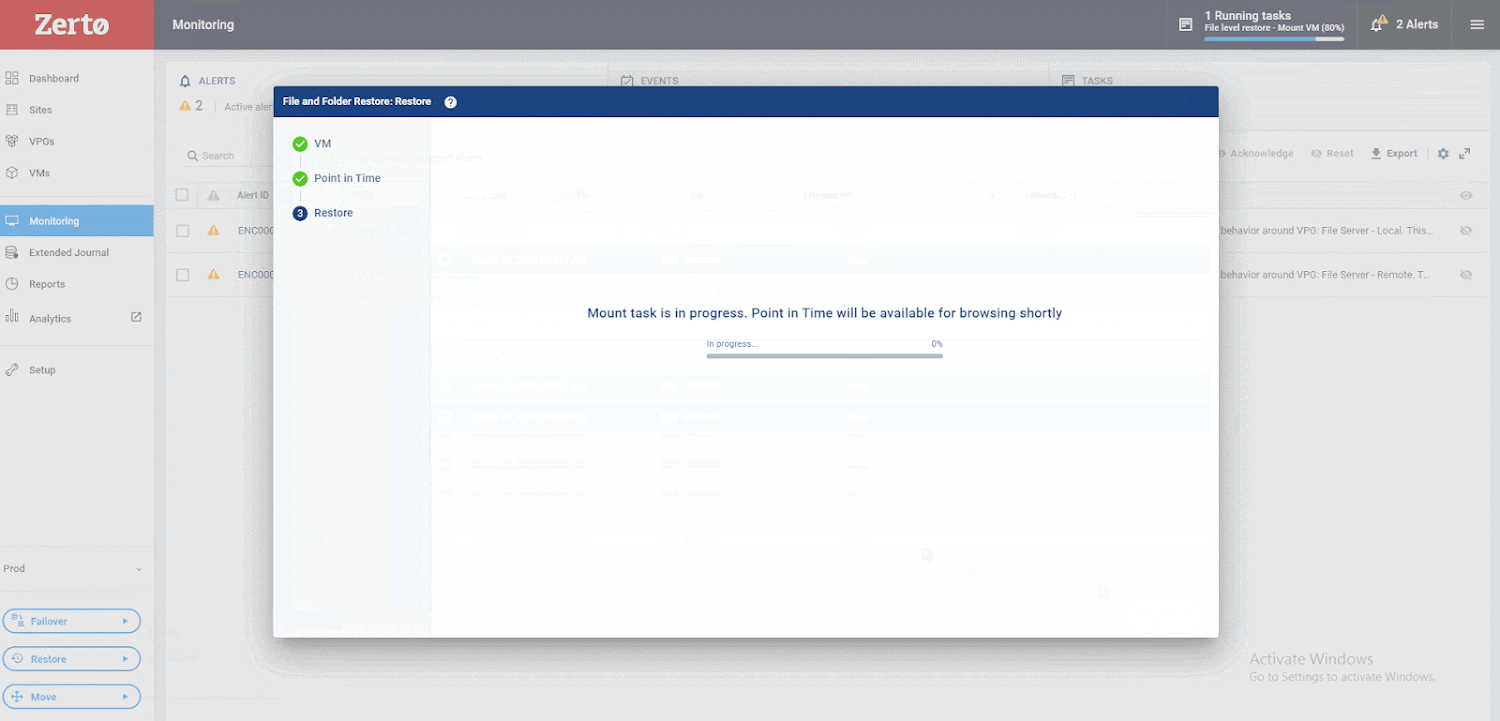
Upcoming, select the VM you want to restore from and to. As soon as you’ve got designed these alternatives, you can look through Zerto’s exceptional journaling abilities. You will observe there are over 700 factors in time, only seconds apart, that you can recuperate from. This guarantees your RPO is as low as possible. Then, you can expect to evaluate these checkpoints, determining the types Zerto has tagged as suspicious. Afterward, you can go back again a small further more and study the kinds marked as cleanse. This process makes it possible for you to recuperate right in advance of suspicious activity was detected.
Now, you can browse the files and folders you wish to restore utilizing a very simple wizard. Pick out the files you want to restore, choose a set of credentials to authenticate into the VM, and hit Restore,

as proven below. Your files will now get better right back again into production without the use of any brokers inside the OS and with only seconds of knowledge loss.

The restoration system is simple and fast to attain, with minimum disruption to any firm.
Now, let’s contemplate how we would get better in the party of a much larger-scale attack that impacts multiple VMs or even hundreds at the same time. By utilizing the failover functionality in Zerto, you can set off a total failover of all chosen VPGs and the VMs inside them to a secondary web site. This secondary internet site could be one more VMware web-site, Hyper-V, or even a community cloud. With full automation and orchestration, a Zerto failover can reach rewards like these:
- 1000’s of VMs with an RTO of minutes
- Whole re-IP of just about every VM, if essential
- Restoring directly onto output-grade storage of your selection with no added migrations essential (this kind of as Storage vMotion)
- Restoring directly again onto manufacturing-grade compute with no any even further measures this kind of as vMotion
This type of recovery is suitable for cyber recovery since significant-scale recoveries can be hard to achieve with backup resources that are not designed for restoration at scale.
Rapid Failover to Secondary Site with Comprehensive Automation and Orchestration: Mobilize, Move, and Get better with Automated Processes

As you can see, Zerto has some one of a kind and remarkable abilities when it arrives to ransomware resilience.
To summarize:
- Zerto allows you to recuperate in minutes to just seconds in advance of an attack, from files and folders to countless numbers of VMs producing complicated purposes.
- Real-time, in-line encryption detection helps establish anomalous exercise, restrict blast radius, and deliver the earliest warning sign that an attack may well be taking place.
- A full, crafted-in automation and orchestration suite means there’s no will need for further resources to be certain your big-scale recoveries are as uncomplicated and rapid as doable.
Will not wait for an attack to transpire! Protect your firm and gain confidence with Zerto. Test Zerto absolutely free for 14 days!
Found this report appealing? This post is a contributed piece from one of our valued companions. Comply with us on Twitter and LinkedIn to read through extra exceptional content material we article.
Some areas of this write-up are sourced from:
thehackernews.com

 How to Conduct Advanced Static Analysis in a Malware Sandbox
How to Conduct Advanced Static Analysis in a Malware Sandbox