Select Ukrainian authorities networks have remained contaminated with a malware termed OfflRouter since 2015.
Cisco Talos mentioned its results are based mostly on an investigation of over 100 private files that have been infected with the VBA macro virus and uploaded to the VirusTotal malware scanning system.
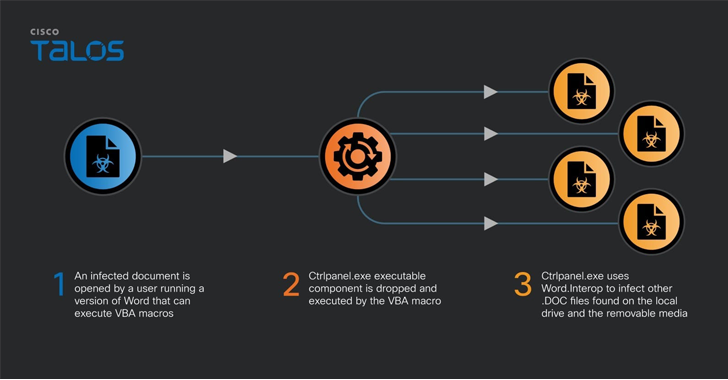
“The files contained VBA code to drop and operate an executable with the name ‘ctrlpanel.exe,'” security researcher Vanja Svajcer mentioned. “The virus is continue to active in Ukraine and is leading to probably private documents to be uploaded to publicly available document repositories.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A hanging factor of OfflRouter is its incapacity to unfold via email, necessitating that it be propagated by way of other means, these types of as sharing documents and removable media, which includes USB memory sticks made up of the infected files.
These design options, intentional or or else, are claimed to have confined the distribute of OfflRouter in Ukraine’s borders and to a several corporations, so escaping detection for just about 10 several years.

It is really currently not identified who is responsible for the malware and there are no indications that it was formulated by a person from Ukraine.
Whoever it is, they have been explained as inventive yet inexperienced owing to the uncommon propagation system and the existence of various problems in the source code.
OfflRouter has been beforehand highlighted by MalwareHunterTeam as early as Might 2018 and yet again by the Personal computer Security Incident Response Crew Slovakia (CSIRT.SK) in August 2021, detailing infected documents uploaded to the Countrywide Police of Ukraine’s website.
The modus operandi has remained almost unchanged, with the VBA macro-embedded Microsoft Term paperwork dropping a .NET executable named “ctrlpanel.exe,” which then infects all documents with the .DOC (not .DOCX) extension found on the method and other removable media with the identical macro.
“The infection iterates by way of a listing of the document candidates to infect and utilizes an ground breaking approach to verify the doc infection marker to stay clear of various an infection procedures – the perform checks the doc generation metadata, adds the generation moments, and checks the value of the sum,” Svajcer said.
“If the sum is zero, the document is viewed as presently infected.”
That mentioned, the attack becomes profitable only when VBA macros are enabled. Microsoft, as of July 2022, has been blocking macros by default in Place of work paperwork downloaded from the internet, prompting danger actors to seek other first accessibility pathways.
A further vital operate of the malware is to make Windows Registry modifications so as to make certain that the executable operates each and every time on booting the system.
“The virus targets only documents with the filename extension .DOC, the default extension for the OLE2 files, and it will not try out to infect other filename extensions,” Svajcer elaborated. “The default Term document filename extension for the a lot more the latest Word versions is .DOCX, so handful of files will be contaminated as a end result.”

That is not all. Ctrlpanel.exe is also outfitted to lookup for likely plugins (with the extension .ORP) present on removable drives and execute them on the equipment, which indicates the malware is expecting the plugins to be sent by using USB drives or CD-ROMs.
Just one the opposite, if the plugins are by now existing on a host, OfflRouter normally takes care of encoding them, copying the information to the root folder of the connected detachable media with the filename extension .ORP, and manipulating them to make them hidden so that they are not visible as a result of the File Explorer when plugging them into a further unit.
That explained, a person significant unidentified is no matter if the original vector is a doc or the executable module ctrlpanel.exe.
“The gain of the two-module virus is that it can be distribute as a standalone executable or as an infected doc,” Svajcer claimed.
“It may perhaps even be advantageous to at first spread as an executable as the module can operate standalone and set the registry keys to make it possible for execution of the VBA code and transforming of the default saved file formats to .DOC just before infecting documents. That way, the infection may perhaps be a little bit stealthier.”
Identified this report appealing? Abide by us on Twitter and LinkedIn to read through additional unique content material we submit.
Some areas of this posting are sourced from:
thehackernews.com


 FIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor
FIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor