Cybersecurity researchers have learned a situation of privilege escalation connected with a Microsoft Entra ID (previously Azure Energetic Directory) application by taking advantage of an deserted reply URL.
“An attacker could leverage this deserted URL to redirect authorization codes to on their own, exchanging the sick-gotten authorization codes for access tokens,” Secureworks Counter Risk Unit (CTU) stated in a specialized report published last week.
“The menace actor could then get in touch with Energy Platform API by using a center-tier services and attain elevated privileges.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Subsequent liable disclosure on April 5, 2023, the issue was dealt with by Microsoft by way of an update produced a day later on. Secureworks has also designed offered an open-source instrument that other organizations can use to scan for deserted reply URLs.

Reply URL, also referred to as redirect URI, refers to the place the place the authorization server sends the user at the time the app has been productively approved and granted an authorization code or access token.
“The authorization server sends the code or token to the redirect URI, so it is vital you register the suitable location as component of the application registration process,” Microsoft notes in its documentation.
Secureworks CTU stated it discovered an deserted Dynamics Knowledge Integration app reply URL related with the Azure Website traffic Supervisor profile that created it possible to invoke the Electric power System API through a middle-tier service and tamper with the natural environment configurations.
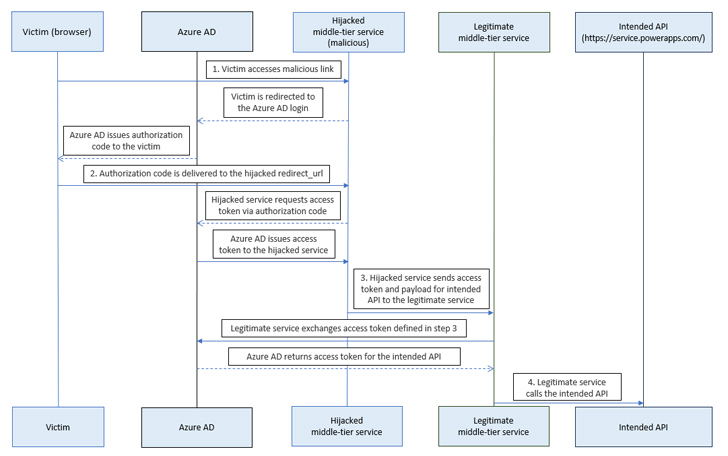
In a hypothetical attack situation, this could have been used to get the program administrator purpose for an present support principal and deliver requests to delete an setting, as perfectly as abuse the Azure Ad Graph API to collect information and facts about the focus on in get to stage comply with-on routines.
This, however, banking institutions on the risk that a target clicks on a malicious url, as a consequence of which the authorization code issued by Microsoft Entra ID upon logging is sent to a redirect URL hijacked by the danger actor.

The disclosure will come as Kroll uncovered an uptick in DocuSign-themed phishing strategies employing open up redirects, enabling adversaries to propagate specially crafted URLs that, when clicked, redirect potential victims to a destructive site.
“By crafting a deceptive URL that leverages a reliable web site, destructive actors can extra effortlessly manipulate people into clicking the url, as well as deceiving/bypassing network technology that scans back links for destructive written content,” Kroll’s George Glass reported.
“This effects in a victim staying redirected to a destructive web-site built to steal sensitive details, these types of as login credentials, credit score card aspects or private information.”
Observed this post interesting? Adhere to us on Twitter and LinkedIn to go through extra special material we put up.
Some elements of this post are sourced from:
thehackernews.com


 Developers Beware: Malicious Rust Libraries Caught Transmitting OS Info to Telegram Channel
Developers Beware: Malicious Rust Libraries Caught Transmitting OS Info to Telegram Channel