Lively flaws in the PowerShell Gallery could be weaponized by risk actors to pull off provide chain attacks towards the registry’s customers.
“These flaws make typosquatting attacks unavoidable in this registry, although also making it extremely difficult for consumers to establish the correct owner of a offer,” Aqua security scientists Mor Weinberger, Yakir Kadkoda, and Ilay Goldman mentioned in a report shared with The Hacker Information.
Maintained by Microsoft, PowerShell Gallery is a central repository for sharing and attaining PowerShell code, which includes PowerShell modules, scripts, and Preferred State Configuration (DSC) assets. The registry offers 11,829 exceptional offers and 244,615 packages in total.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The issues recognized by the cloud security agency have to do with the service’s lax coverage encompassing offer names, lacking protections from typosquatting attacks, as a result enabling attackers to add malicious PowerShell modules that look authentic to unsuspecting end users.

A second flaw pertains to the ability of a poor actor to spoof the metadata of a module — such as Author(s), Copyright, and Description fields — to make it appear more respectable, thereby deceiving unwitting people into putting in them.
“The only way for buyers to establish the serious author/owner is to open up the ‘Package Details’ tab,” the scientists explained.
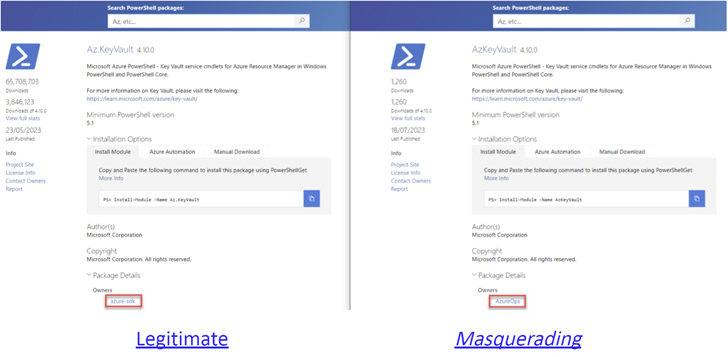
“Even so, this will only lead them to the profile of the phony writer, as the attacker can freely choose any name when creating a user in the PowerShell Gallery. Hence, pinpointing the real writer of a PowerShell module in the PowerShell Gallery poses a challenging activity.”
Also uncovered is a 3rd flaw that could be abused by attackers to enumerate all package deal names and versions, which include those that are unlisted and meant to be hidden from general public check out.
This can be completed by utilizing the PowerShell API “https://www.powershellgallery.com/api/v2/Offers?$skip=range,” enabling an attacker to achieve unrestricted entry to the comprehensive PowerShell offer databases, like related versions.

“This uncontrolled accessibility delivers destructive actors with the ability to research for possible sensitive details inside unlisted offers. As a result, any unlisted bundle that is made up of confidential info, turns into remarkably inclined to compromise,” the scientists discussed.
Aqua claimed it described the shortcomings to Microsoft in September 2022, next which the Windows maker is mentioned to have put in place reactive fixes as of March 7, 2023. The troubles, even so, keep on being reproducible.
“As we more and more depend on open-supply projects and registries, the security hazards connected with them grow to be extra well known,” the scientists concluded.
“The duty for securing consumers principally lies with the platform. It truly is essential that PowerShell Gallery, and related platforms, get required ways to boost their security actions.”
Observed this posting fascinating? Observe us on Twitter and LinkedIn to browse much more distinctive articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 Guide: How Google Workspace-based Organizations can leverage Chrome to improve Security
Guide: How Google Workspace-based Organizations can leverage Chrome to improve Security