At a tiny overt midway by means of 2023, credential theft is nevertheless a major thorn in the aspect of IT groups. The coronary heart of the issue is the worth of knowledge to cybercriminals and the evolution of the tactics they use to get keep of it. The 2023 Verizon Information Breach Investigations Report (DBIR) disclosed that 83% of breaches included external actors, with virtually all attacks being financially motivated. Of these breaches by exterior actors, 49% included the use of stolen qualifications.
We’ll discover why credential theft is continue to such an interesting (and prosperous) attack route, and glance at how IT security groups can combat back again in the next fifty percent of 2023 and past.
People are continue to typically the weak backlink
The hallmarks of lots of productive cyberattacks are the willpower, inventiveness, and tolerance risk actors show. Although a consumer may place some attacks through security and awareness coaching, it only requires a person effectively-crafted attack to capture them. At times all it normally takes is for a person to be dashing or pressured. Threat actors craft phony login internet pages, falsified invoices (such as in enterprise email compromise attacks), and redirect email exchanges to trick the end-user into supplying up credentials or cash.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Verizon’s DBIR observed that 74% of breaches involve the human factor, either as a result of human mistake, privilege misuse, social engineering, or stolen credentials. A person fascinating data place was that 50% of all social engineering attacks in 2022 utilised a procedure named ‘pretexting’ – an invented circumstance that tricks a user into offering up their qualifications or undertaking a further valuable motion to the attacker. This exhibits that attackers know buyers are often the weak backlink, and they’re fully commited to using social engineering to get their fingers on credentials. It can be often an less complicated route into an corporation than hacking a complex factor of an IT procedure.
Breaching a technique by way of stolen qualifications
Large businesses with big security budgets are not immune to cyberattacks – even individuals operating the cybersecurity marketplace. Norton Lifelock Password Supervisor presents a recent case review into the lengths attackers will go to in order to get keep of passwords. As noted by the condition of Maine’s Lawyer Standard, Norton notified just about 6,500 shoppers early in 2023 that their info might have been compromised. Via a brute-power attack working with stolen credentials, attackers finally uncovered functioning passwords and swiftly proceeded to log into client accounts, most likely accessing stored consumer strategies.
Despite Norton IT alerting on a massive volume of failed logins and having rapid action, Norton Lifelock Password Manager customers were nevertheless compromised. This underlines the threat that stolen qualifications perform in attacks. No subject the power of a firm’s security, a password stolen from a further less-safeguarded group is hard to reduce from reuse.
As the Verizon report showed, approximately 50 % (49%) of very last year’s breaches stemmed from stolen credentials. So exactly where are attackers obtaining these breached qualifications? And how can you convey to if your users have compromised passwords out there much too?
Acquiring stolen strategies in black markets
Like advanced black marketplaces of previous, on-line black marketplaces peddling stolen qualifications are increasingly widespread. Massive datasets consisting of hundreds of 1000’s of stolen qualifications are readily available for sale although costing peanuts future to the feasible payoff a thriving ransomware or BEC attack could have. These lists are specifically precious for non-complex attackers who deficiency the skills to hack IT methods themselves.
The latest Genesis Sector takedown confirmed how these marketplaces are evolving. Offering “electronic fingerprints” for sale, in its place of just a compromised username and password, frequently up to date identities had been readily available for a membership. A lot more than just a stolen established of credentials, these fingerprints paired with carefully-situated VPN obtain that allowed an attacker far larger access than stolen qualifications on your own can provide.
The shady underground mother nature of these marketplaces will make them tough to find and eliminate. One particular may be eradicated with one more popping up mere times later on. With the median cost of a business enterprise email compromise attack mounting to $50,000 alone in 2023, the acquiring of stolen qualifications is all the more beautiful for menace actors.
Shield your small business from stolen credentials
With a total 49% of breaches involving stolen qualifications and evolving electronic black marketplaces, these types of as Genesis, equipment focused to detecting compromised passwords are important for overworked IT departments. Specops Password Policy withBreached Password Defense will help customers generate much better passwords in Lively Listing with dynamic, instructive consumer comments and blocks the use of around 3 billion exclusive compromised passwords.
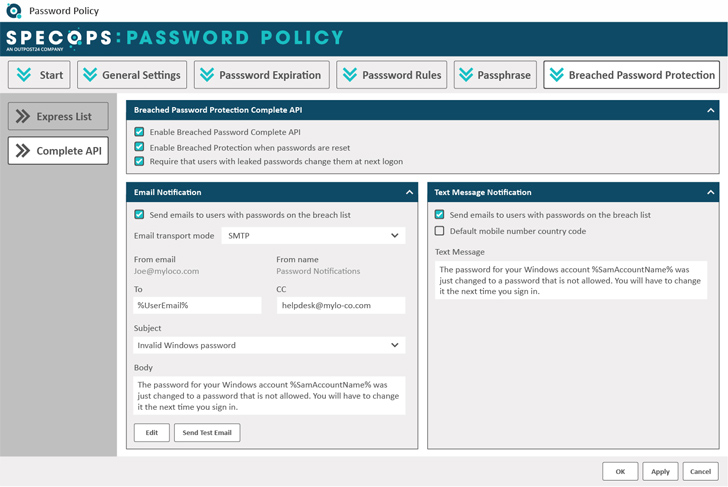
This consists of lists uncovered on dark internet sites such as Genesis and passwords remaining made use of in attacks ideal now on Specops honeypot accounts. IT groups take pleasure in restricted Advert integration, and effortless-to-use finish-consumer interfaces for complying with complex password guidelines and blocking the use of weak and compromised credentials.
Fascinated in taking a to start with action in the direction of superior password security? Scan your Lively Listing with Specops Password Auditor for visibility into how numerous compromised passwords could by now be in your present natural environment. Commence closing off straightforward attack routes today to stay clear of main compromises in the future.
Observed this article intriguing? Adhere to us on Twitter and LinkedIn to read through extra exceptional content we publish.
Some sections of this article are sourced from:
thehackernews.com


 Experts Uncover Weaknesses in PowerShell Gallery Enabling Supply Chain Attacks
Experts Uncover Weaknesses in PowerShell Gallery Enabling Supply Chain Attacks