A severity flaw impacting industrial cellular routers from Milesight may perhaps have been actively exploited in real-planet attacks, new conclusions from VulnCheck expose.
Tracked as CVE-2023-43261 (CVSS rating: 7.5), the vulnerability has been described as a situation of information and facts disclosure that impacts UR5X, UR32L, UR32, UR35, and UR41 routers just before edition 35.3..7 that could help attackers to accessibility logs this sort of as httpd.log as effectively as other sensitive qualifications.
As a result, this could allow remote and unauthenticated attackers to attain unauthorized entry to the web interface, thereby creating it probable to configure VPN servers and even drop firewall protections.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This vulnerability results in being even far more severe as some routers enable the sending and acquiring of SMS messages,” security researcher Bipin Jitiya, who found the issue, claimed before this month. “An attacker could exploit this features for fraudulent routines, possibly causing money harm to the router operator.”

Now, according to VulnCheck’s Jacob Baines, there is evidence that the flaw may have been exploited on a little-scale in the wild.
“We noticed 5.61.39[.]232 trying to log into 6 programs on October 2, 2023,” Baines mentioned. “The influenced systems’ IP addresses geolocate to France, Lithuania, and Norway. They do not appear to be relevant, and all use unique non-default qualifications.”
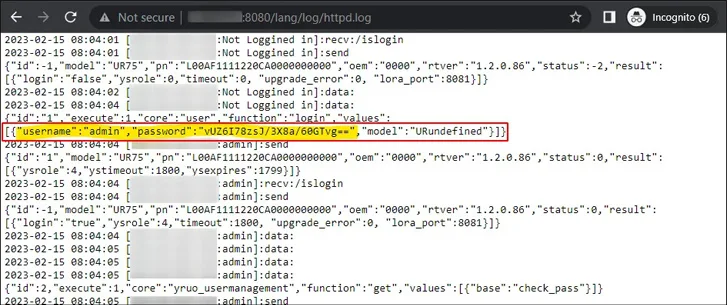
On 4 of the six equipment, the risk actor is stated to have efficiently authenticated on the initial endeavor. On the fifth program, the login was productive the next time, and on the sixth, the authentication resulted in failure.
The qualifications employed to pull off the attack were being extracted from the httpd.log, alluding to the weaponization of CVE-2023-43261. There is no evidence of any further malicious actions, despite the fact that it seems that the mysterious actor checked the options and status internet pages.
According to VulnCheck, while there are roughly 5,500 internet-uncovered Milesight routers, only about 5% are jogging vulnerable firmware versions, and therefore susceptible to the flaw.
“If you have a Milesight Industrial Cellular Router, it truly is likely wise to assume all the qualifications on the procedure have been compromised and to only make new ones, and assure no interfaces are reachable through the internet,” Baines mentioned.
Six Flaws Learned in Titan MFT and Titan SFTP Servers

The disclosure arrives as Fast7 specific a number of security flaws in South River Technologies’ Titan MFT and Titan SFTP servers that, if exploited, could allow remote superuser obtain to afflicted hosts.

The record of vulnerabilities is as follows –
- CVE-2023-45685 – Authenticated Remote Code Execution by using “Zip Slip”
- CVE-2023-45686 – Authenticated Remote Code Execution by way of WebDAV Route Traversal
- CVE-2023-45687 – Session Fixation on Remote Administration Server
- CVE-2023-45688 – Facts Disclosure via Path Traversal on FTP
- CVE-2023-45689 – Details Disclosure by using Path Traversal in Admin Interface
- CVE-2023-45690 – Facts Leak by using Planet-Readable Databases + Logs
“Prosperous exploitation of a number of of these issues grants an attacker remote code execution as the root or Method user,” the enterprise said. “However, all issues are submit-authentication and have to have non-default configurations and are hence not likely to see extensive scale exploitation.”
Found this post interesting? Follow us on Twitter and LinkedIn to examine far more unique material we article.
Some components of this report are sourced from:
thehackernews.com


 CERT-UA Reports: 11 Ukrainian Telecom Providers Hit by Cyberattacks
CERT-UA Reports: 11 Ukrainian Telecom Providers Hit by Cyberattacks