In a sign that cybersecurity researchers carry on to be beneath the radar of malicious actors, a evidence-of-principle (PoC) has been identified on GitHub, concealing a backdoor with a “crafty” persistence strategy.
“In this instance, the PoC is a wolf in sheep’s apparel, harboring malicious intent under the guise of a harmless learning device,” Uptycs scientists Nischay Hegde and Siddartha Malladi stated. “Working as a downloader, it silently dumps and executes a Linux bash script, all the while disguising its operations as a kernel-level method.”
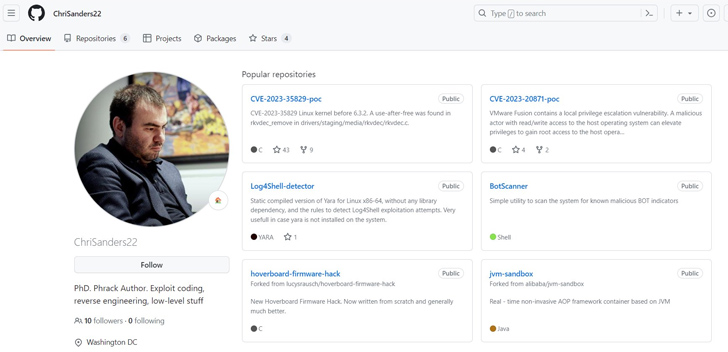
The repository masquerades as a PoC for CVE-2023-35829, a a short while ago disclosed significant-severity flaw in the Linux kernel. It has considering the fact that been taken down, but not just before it was forked 25 instances. One more PoC shared by the exact account, ChriSanders22, for CVE-2023-20871, a privilege escalation bug impacting VMware Fusion, was forked 2 times.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Uptypcs also determined a second GitHub profile containing a bogus PoC for CVE-2023-35829. It is even now readily available as of crafting and has been forked 19 instances. A nearer evaluation of the commit record displays that the variations ended up pushed by ChriSanders22, suggesting it was forked from the original repository.
The backdoor comes with a wide vary of capabilities to steal sensitive details from compromised hosts as well as make it possible for a risk actor to gain remote accessibility by incorporating their SSH essential to the .ssh/authorized_keys file.
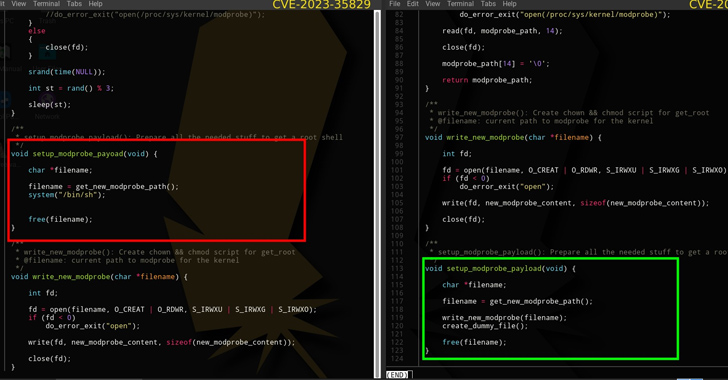
“The PoC intends for us to operate a make command that is an automation resource applied to compile and make executables from resource code documents,” the researchers spelled out. “But in just the Makefile resides a code snippet that builds and executes the malware. The malware names and runs a file named kworker, which adds the $Dwelling/.area/kworker route in $Dwelling/.bashrc, thereby establishing its persistence.”
Impending WEBINARShield Versus Insider Threats: Master SaaS Security Posture Administration
Anxious about insider threats? We have received you included! Join this webinar to check out sensible strategies and the tricks of proactive security with SaaS Security Posture Management.
Join Nowadays
The advancement comes almost a thirty day period immediately after VulnCheck found out a quantity of pretend GitHub accounts posing as security scientists to distribute malware below the guise of PoC exploits for well-liked software package these kinds of as Discord, Google Chrome, Microsoft Exchange Server, Signal, and WhatsApp.
Users who have downloaded and executed the PoCs are encouraged to unauthorized SSH keys, delete the kworker file, erase the kworker route from the bashrc file, and test /tmp/.iCE-unix.pid for opportunity threats.
“Although it can be difficult to distinguish genuine PoCs from misleading types, adopting secure techniques this kind of as tests in isolated environments (e.g., virtual devices) can deliver a layer of security,” the researchers claimed.
Observed this report exciting? Adhere to us on Twitter and LinkedIn to go through much more exceptional articles we publish.
Some components of this article are sourced from:
thehackernews.com

 Rockwell Automation ControlLogix Bugs Expose Industrial Systems to Remote Attacks
Rockwell Automation ControlLogix Bugs Expose Industrial Systems to Remote Attacks