Federal government entities, armed service businesses, and civilian end users in Ukraine and Poland have been targeted as aspect of a collection of campaigns designed to steal sensitive data and attain persistent remote obtain to the contaminated systems.
The intrusion established, which stretches from April 2022 to July 2023, leverages phishing lures and decoy files to deploy a downloader malware termed PicassoLoader, which functions as a conduit to launch Cobalt Strike Beacon and njRAT.
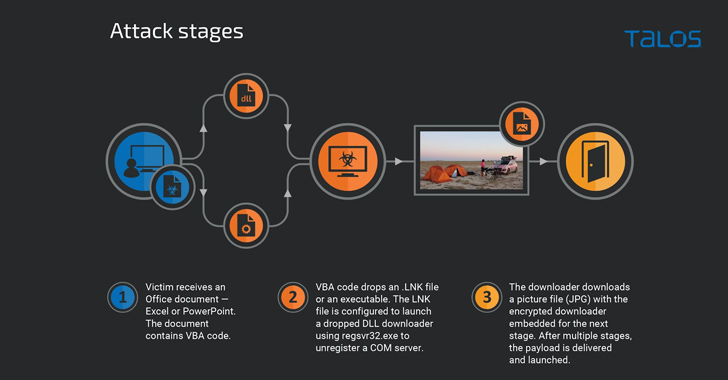
“The attacks made use of a multistage infection chain initiated with malicious Microsoft Place of work paperwork, most typically employing Microsoft Excel and PowerPoint file formats,” Cisco Talos researcher Vanja Svajcer reported in a new report. “This was adopted by an executable downloader and payload hid in an graphic file, possible to make its detection far more hard.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Some of the activities have been attributed to a danger actor called GhostWriter (aka UAC-0057 or UNC1151), whose priorities are explained to align with the Belarusian government.
It is really value noting that a subset of these attacks has already been documented above the earlier year by Ukraine’s Laptop or computer Crisis Response Crew (CERT-UA) and Fortinet FortiGuard Labs, 1 of which employed macro-laden PowerPoint paperwork to deliver Agent Tesla malware in July 2022.
The an infection chains purpose to influence victims to allow macros, with the VBA macro engineered to fall a DLL downloader known as PicassoLoader that subsequently reaches out to an attacker-managed internet site to fetch the up coming-stage payload, a authentic graphic file that embeds the last malware.
The disclosure will come as CERT-UA thorough a range of phishing functions distributing the SmokeLoader malware as properly as a smishing attack developed to acquire unauthorized command of targets’ Telegram accounts.
Very last thirty day period, CERT-UA disclosed a cyber espionage marketing campaign aimed at condition businesses and media representatives in Ukraine that can make use of email and instantaneous messengers to distribute documents, which, when introduced, outcomes in the execution of a PowerShell script identified as LONEPAGE to fetch upcoming-stage browser stealer (THUMBCHOP) and keylogger (CLOGFLAG) payloads.
Approaching WEBINARShield From Insider Threats: Grasp SaaS Security Posture Management
Nervous about insider threats? We have obtained you protected! Be a part of this webinar to take a look at realistic procedures and the tricks of proactive security with SaaS Security Posture Management.
Be a part of Today
GhostWriter is one between the many danger actors that have set their sights on Ukraine. This also consists of the Russian nation-state team APT28, which has been noticed employing HTML attachments in phishing e-mails that prompt recipients to modify their UKR.NET and Yahoo! passwords because of to suspicious activity detected in their accounts so as to redirect them to bogus landing internet pages that in the long run steal their qualifications.
The development also follows the adoption of a “typical five-period playbook” by hackers linked with the Russian navy intelligence (GRU) in their disruptive operations towards Ukraine in a “deliberate effort and hard work to improve the pace, scale, and intensity” of their attacks.
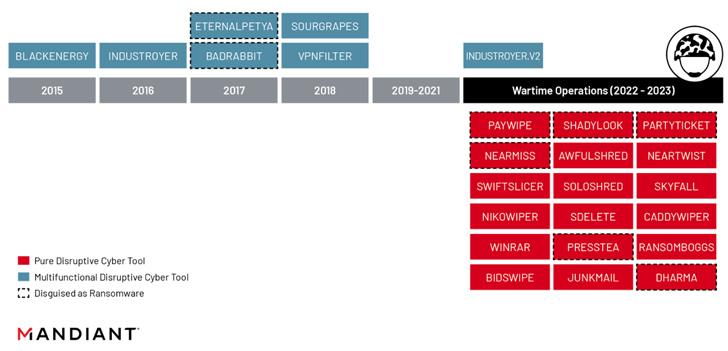
This comprises having benefit of residing-on-the-edge infrastructure to get original access, making use of living-off-the-land tactics to carry out reconnaissance, lateral motion and details theft to limit their malware footprint and evade detection, building persistent, privileged entry via team coverage objects (GPO), deploying wipers, and telegraphing their functions by means of hacktivist personas on Telegram.
“The gains the playbook affords are notably suited for a speedy-paced and highly contested functioning natural environment, indicating that Russia’s wartime aims have very likely guided the GRU’s chosen tactical classes of action,” Google-owned Mandiant stated.
Discovered this write-up appealing? Abide by us on Twitter and LinkedIn to read more exclusive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 TeamTNT’s Silentbob Botnet Infecting 196 Hosts in Cloud Attack Campaign
TeamTNT’s Silentbob Botnet Infecting 196 Hosts in Cloud Attack Campaign