The AvosLocker ransomware gang has been connected to attacks towards critical infrastructure sectors in the U.S., with some of them detected as not long ago as Might 2023.
That is according to a new joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Company (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-assistance (RaaS) operation’s tactics, procedures, and techniques (TTPs).
“AvosLocker affiliates compromise organizations’ networks by working with legit software and open up-resource remote program administration equipment,” the businesses reported. “AvosLocker affiliate marketers then use exfiltration-based mostly facts extortion practices with threats of leaking and/or publishing stolen details.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The ransomware pressure initially emerged on the scene in mid-2021, and has because leveraged subtle tactics to disable antivirus safety as a detection evasion evaluate. It influences Windows, Linux, and VMware ESXi environments.
A crucial hallmark of AvosLocker attacks is the reliance on open-resource resources and residing-off-the-land (LotL) ways, leaving no traces that could lead to attribution. Also utilized are reputable utilities like FileZilla and Rclone for facts exfiltration as nicely as tunneling tools these kinds of as Chisel and Ligolo.

Command-and-management (C2) is accomplished by implies of Cobalt Strike and Sliver, although Lazagne and Mimikatz are applied for credential theft. The attacks also hire customized PowerShell and Windows Batch scripts for lateral movement, privilege escalation, and disarming security software program.
“AvosLocker affiliates have uploaded and utilised tailor made web shells to enable network entry,” the companies mentioned. Yet another new ingredient is an executable named NetMonitor.exe that masquerades as a network checking device but truly capabilities as a reverse proxy to permit the danger actors to hook up to the host from outside the victim’s network.
CISA and FBI are recommending critical infrastructure businesses to implement needed mitigations to decrease the likelihood and influence of AvosLocker ransomware and other ransomware incidents.
This contains adopting software controls, limiting the use of RDP and other remote desktop services, limiting PowerShell use, demanding phishing-resistant multi-factor authentication, segmenting networks, retaining all methods up-to-day, and keeping periodic offline backups.
The improvement comes as Mozilla warned of ransomware attacks leveraging malvertising campaigns that trick end users into setting up trojanized versions of Thunderbird, eventually major to the deployment of file-encrypting malware and commodity malware households this kind of as IcedID.
Ransomware attacks in 2023 have witnessed a significant surge, even as threat actors are transferring quickly to deploy ransomware in just 1 day of original obtain in far more than 50% of engagements, in accordance to Secureworks, dropping from the earlier median dwell time of 4.5 times in 2022.
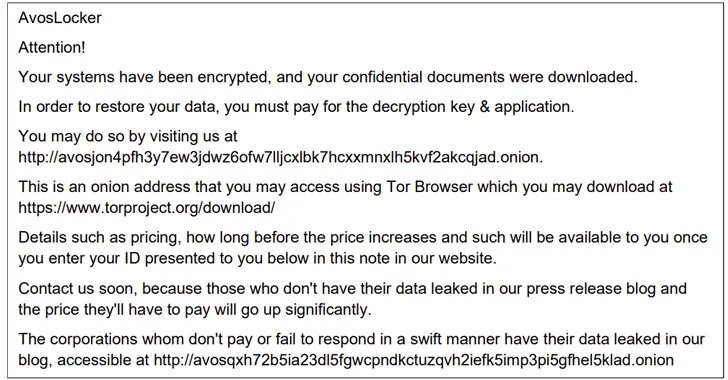
What’s additional, in much more than 10 p.c of incidents, ransomware was deployed within just 5 hours.
“The driver for the reduction in median dwell time is possible thanks to the cybercriminals’ wish for a reduce likelihood of detection,” Don Smith, vice president of danger intelligence at Secureworks Counter Danger Unit, said.
“As a outcome, danger actors are concentrating on easier and more quickly to employ functions, rather than large, multi-web page organization-wide encryption events that are noticeably extra sophisticated. But the risk from individuals attacks is continue to superior.”
Exploitation of public facing apps, stolen credentials, off-the-shelf malware, and exterior distant companies have emerged as the three greatest preliminary access vectors for ransomware attacks.
To rub salt into the wound, the RaaS model and the ready availability of leaked ransomware code have decreased the barrier to entry for even newbie criminals, building it a worthwhile avenue to make illicit income.
“When we even now see common names as the most lively menace actors, the emergence of several new and extremely energetic menace teams is fuelling a considerable increase in sufferer and information leaks,” Smith extra. “Irrespective of higher profile takedowns and sanctions, cybercriminals are masters of adaptation, and so the threat proceeds to acquire tempo.”

Microsoft, in its yearly Digital Protection Report, reported 70% of corporations encountering human-operated ransomware experienced fewer than 500 staff, and that 80 to 90 % of all compromises originate from unmanaged gadgets.
Telemetry knowledge gathered by the organization exhibits that human-operated ransomware attacks have long gone up much more than 200 p.c considering the fact that September 2022. Magniber, LockBit, Hive, and BlackCat comprised almost 65 per cent of all ransomware encounters.
On leading of that, around 16 percent of modern thriving human-operated ransomware attacks associated the two encryption and exfiltration, though a 13 % utilized exfiltration only.
“Ransomware operators are also significantly exploiting vulnerabilities in much less typical software program, creating it more difficult to predict and protect from their attacks,” the tech giant stated. “This reinforces the relevance of a holistic security method.”
Redmond explained it also noticed a “sharp increase” in the use of remote encryption during human-operated ransomware attacks, accounting for 60 percent on common more than the earlier 12 months.
“Alternatively of deploying destructive data files on the sufferer system, encryption is carried out remotely, with the system course of action doing the encryption, which renders process-based remediation ineffective,” Microsoft described. “This is a signal of attackers evolving to further limit their footprint.”
Identified this post appealing? Stick to us on Twitter and LinkedIn to browse additional special content material we post.
Some parts of this post are sourced from:
thehackernews.com


 Malicious NuGet Package Targeting .NET Developers with SeroXen RAT
Malicious NuGet Package Targeting .NET Developers with SeroXen RAT