A new monetarily determined campaign that commenced in December 2022 has noticed the unidentified risk actor driving it deploying a novel ransomware strain dubbed MortalKombat and a clipper malware regarded as Laplas.
Cisco Talos mentioned it “observed the actor scanning the internet for sufferer machines with an exposed remote desktop protocol (RDP) port 3389.”
The attacks, for each the cybersecurity organization, primarily focuses on people, compact companies, and big organizations situated in the U.S., and to a lesser extent in the U.K., Turkey, and the Philippines.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
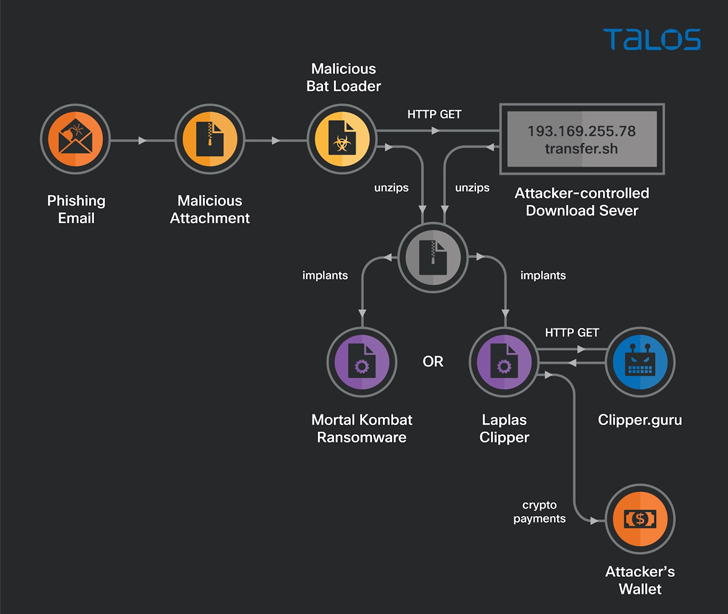
The setting up level that kicks off the multi-phase attack chain is a phishing email bearing a malicious ZIP file which is made use of as a pathway to deliver both the clipper or the ransomware.
In addition to applying cryptocurrency-themed email lures impersonating CoinPayments, the risk actor is also recognised to erase an infection markers in an try to address its tracks.
MortalKombat, very first detected in January 2023, is capable of encrypting technique, application, backup, and virtual machine documents in the compromised method. It further corrupts Windows Explorer, disables the Operate command window, and gets rid of purposes and folders from Windows startup.
A supply code analysis of the ransomware reveals that it can be section of the Xorist spouse and children of ransomware, Cisco Talos researcher Chetan Raghuprasad mentioned.
The Laplas clipper is a Golang variant of malware that came to light in November 2022. It can be created to keep track of the clipboard for any cryptocurrency wallet tackle and substitute it with an actor-managed wallet to carry out fraudulent transactions.
“The clipper reads the target machine’s clipboard contents and executes a functionality to accomplish frequent expression pattern matching to detect the cryptocurrency wallet address,” Raghuprasad discussed.
“When a cryptocurrency wallet handle is identified, the clipper sends the wallet tackle back to the clipper bot. In reaction, the clipper gets an attacker-managed wallet deal with very similar to the victim’s and overwrites the first cryptocurrency wallet handle in the clipboard.”
Observed this article exciting? Follow us on Twitter and LinkedIn to go through much more unique content material we submit.
Some sections of this post are sourced from:
thehackernews.com


 Threat Analysis: VMware ESXi Attacks Soared in 2022
Threat Analysis: VMware ESXi Attacks Soared in 2022