The ESXiArgs ransomware attack that started out infecting servers of VMware ESXi hypervisors from February 2, 2023, is the newest of a extended record of destructive strategies exploiting ESXi vulnerabilities.
Menace intelligence organization Recorded Long term has tracked ESXi-focused ransomware due to the fact 2020. In a menace examination report revealed on February 13, 2023, the firm explained it thinks virtual equipment (VM) orchestration applications such as ESXi will ever more be utilised by destructive actors in the future “as companies continue on virtualizing their critical infrastructure and business enterprise systems.”
VMware’s hypervisors, nonetheless, are progressively interesting to threat actors, with the report noting “an roughly 3-fold boost in ransomware focusing on ESXi among 2021 and 2022, with offerings offered from several groups which include ALPHV, LockBit, and BlackBasta.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
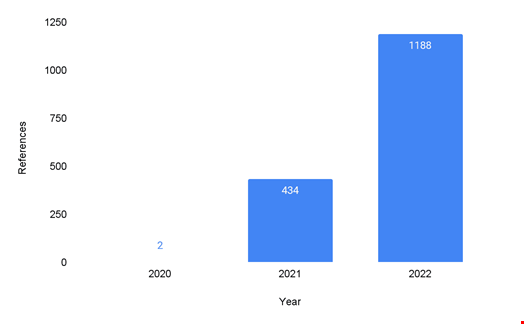 Ransomware attacks targeted on ESXi exhibit a three-fold increase in a single year. Supply: Recorded Upcoming
Ransomware attacks targeted on ESXi exhibit a three-fold increase in a single year. Supply: Recorded Upcoming
ESXi exploits were pretty much non-existent in 2020, notes the report, explaining that during this time “threat actors mostly qualified Windows-centered networks because of to the availability of original obtain presented by the pandemic and various critical vulnerabilities.”
Cyber-attacks exploiting ESXi jumped to 434 in 2021 and Recorded Upcoming observed that an even a lot more substantial surge happened in 2022, with ESXi-focused cyber-attacks reaching at the very least 1188.
Attaining Initial Access
In most cases, danger actors make use of ESXi vulnerabilities to gain initial obtain, “specifically via distant code execution (RCE) or authentication bypass,” scientists noted.
Several corporations, like US Cybersecurity and Infrastructure Security Agency (CISA) and France’s CERT-FR, think that the ESXiArgs ransomware marketing campaign exploited a 2021 vulnerability (CVE-2021-21974).
Recorded Long run also uncovered that danger actors attacking ESXi usually try out to get administrator qualifications, permit SSH on the ESXi servers, and then escalate to root privileges for unrestricted obtain.
“This type of obtain working with respectable credentials is challenging to detect because of to its means to mix into normal system administrator things to do [by] abusing native instructions to carry out their actions,” the report reads.
The immaturity of antivirus and EDR options that protect ESXi also lowers the technical barrier for danger actors deploying malware on ESXi as opposed with individuals concentrating on Windows.
Backdoors, Ransomware and SharpSphere
Once they have gained privileged access to the ESXi servers, attackers normally use it for a few purposes:
- Setting up backdoors
- Deploying ransomware
- Using a article-exploitation toolkit these kinds of as SharpSphere, a C# implementation of vSphere’s Web Products and services API, to deploy credential dumping attacks, for instance.
A Multi-Faceted Mitigation Solution Necessary
The report notes that mitigating these attacks is no easy job “due to the complex nature of hypervisors.” It requires a multi-faceted, multi-layered tactic.
To start with, “traditional defenses, potent password guidelines, and minimizing the attack surface can supply a great offer of deterrence to menace actors,” reads the report. But it will not reduce additional subtle attacks.
For better defense, Recorded Potential endorses employing the subsequent:
- Allow multi-factor authentication (MFA) and implement it on higher-privileged accounts
- Produce alerts on account modifications, enabling of expert services, and authentication styles
- Chorus from applying Active Directory authentication for directors
- Disable SSH and Shell entry to ESXi. However, if they will have to be enabled, contemplate location timeouts and enabling crucial-only authentication
- Put into action network segmentation for the ESXi administration network
- Reduce the variety of open up ESXi firewall ports, and use vSphere Client, ESXCLI, or PowerCLI commands to look at and handle the standing of ports
- Be certain that software program, drivers, and other parts of ESXi are respectable and empower Safe Boot on ESXi to execute validation of the components at boot time
- Put in and configure Reliable Platform Module 2. chips, as this offers the most helpful VMware-supported process of making sure the integrity of program elements on the method
- Prohibit code execution inside of ESXi with VMkernel.Boot.execInstalledOnly.
Although “ransomware targeting ESXi will carry on to be a danger to companies, placing them at risk of operational downtime, aggressive disadvantage, and problems to their manufacturer, […] organizations must keep on to deploy virtualized infrastructure, but it is critical to put into practice security greatest methods and related precautions as made use of in existing infrastructure,” the report concludes.
Some parts of this article are sourced from:
www.infosecurity-magazine.com


 Microsoft patches three zero days, 77 security vulnerabilities in February Patch Tuesday
Microsoft patches three zero days, 77 security vulnerabilities in February Patch Tuesday