One particular of the enduring worries of creating modern day purposes is to make them much more protected with no disrupting high-velocity DevOps procedures or degrading the developer experience. Present-day cyber risk landscape is rife with subtle attacks aimed at all different pieces of the application source chain and the urgency for software package-creating organizations to undertake DevSecOps tactics that deeply combine security all through the computer software development existence cycle has under no circumstances been better.
Having said that, HOW companies go about it is of critical value. For example, locking down the growth platform, instituting exhaustive code reviews, and imposing heavyweight acceptance processes may increase the security posture of pipelines and code, but you should not count on applications teams to work fluidly sufficient to innovate. The same goes for application security tests uncovering a mountain of vulnerabilities does very little very good if developers have inadequate time or direction to deal with them.
At a higher amount, developing and working a DevSecOps apply implies that your group is capable to work a secure delivery platform, exam for program vulnerabilities, prioritize and remediate vulnerabilities, stop the launch of insecure code, and guarantee the integrity of computer software and all of its artifacts.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
But setting up and jogging a remarkably effective DevSecOps apply implies attaining all of these targets at the very same (or increased) improvement velocity and overall level of developer fulfillment. The adhering to 5 guiding principles are essential to acquiring there.
Tenet 1: Create a collaborative, security-minded tradition
A strong and productive lifestyle is essential to the accomplishment of any team but it is really also the toughest component to get correct. This is in particular true of DevSecOps, as evidenced by a modern sector study revealing that “in excess of half (51%) of IT final decision makers report outright resistance to alter amongst their teams whilst 47% say there is insufficient cross-staff collaboration[1].”
The importance of society for prosperous DevSecOps shouldn’t be underestimated, and it starts with accepting security as a precedence for all stakeholders.
Make security a shared duty
If your business builds, sells, or consumes computer software (which right now is each and every conceivable group on the earth), then just about every solitary worker has an influence on the total security posture– not just these with ‘security’ in their titles. At its main, DevSecOps is a culture of shared obligation, and operating with a common security-oriented way of thinking establishes how well DevSecOps processes in shape into area and can generate superior final decision-generating when selecting DevOps platforms, tooling, and individual security methods.
Mindsets never adjust right away, but alignment and a perception of security accountability can be obtained through the pursuing:
- Dedication to common internal security training– tailored to DevSecOps– that features builders, DevOps engineers, and security engineers. Techniques gaps and needs shouldn’t be underestimated.
- Developer adoption of safe coding methodologies and sources
- Security engineering contributes to software and setting architecture, and design and style critiques. It really is often much easier to recognize and take care of security issues early in the program progress lifecycle.
Crack down functional silos and collaborate continually

Given that DevSecOps is a end result of the confluence of software package advancement, IT operations, and security, breaking down silos and actively collaborating on a constant basis is critical for results. Ordinarily, DevOps-centric organizations working without having any official DevSecOps framework see security moving into the photo like an unwelcome party crasher. Procedure alterations or tooling that are quickly imposed (as opposed to collaboratively picked and instantiated) invariably results in growth pipeline friction and unneeded toil for developers. A common situation entails security mandating supplemental software security checks devoid of consideration for their placement inside of the pipeline, or for how considerably workload is needed to system scanner output and remediate vulnerabilities, which inevitably falls to developers.
Driving collaboration and running as a cohesive DevSecOps staff requires:
- Defining and agreeing on a set of measurable security targets, these as:
- % lessen of software security incidents
- % reduce time used on audit
- % improve in deployment frequency
- % reduce in alter failure rate
- % lessen of vulnerabilities deployed to generation
- % of artifacts deployed to creation with SBOM/SLSA
- Decrease in guide time to zero-day vulnerability remediation
- Involvement from software program developers and DevOps teams in the course of the analysis and procurement processes for new security instruments
- Guaranteeing no DevSecOps approach has a solitary purposeful gatekeeper
- Iteratively optimizing tooling selections and security procedures for developer productivity and velocity
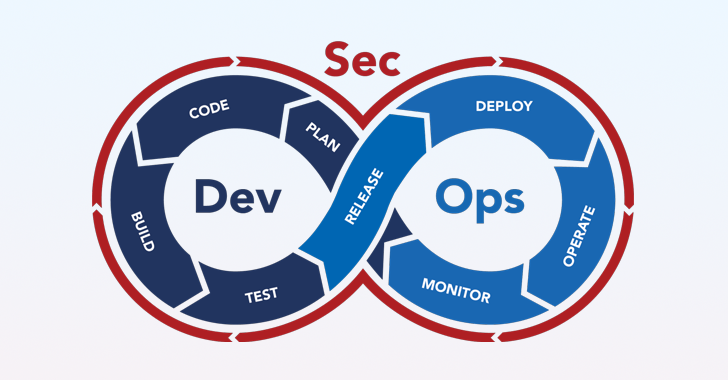
Tenet 2: Shift security information still left, not security workload
Broach the topic of DevSecOps and it’s difficult not to point out ‘shift-left’. The change-left security mantra is so commonplace in latest DevSecOps-oriented articles or blog posts, weblogs, and internet marketing collateral, it truly is simple to believe that by simply just going security checks further more upstream in the software package enhancement lifecycle you have reached a performing DevSecOps software. The truth is that WHAT you change still left is what will make or breaks your DevSecOps achievement.
Change left security is predicated on the confirmed notion that executing software security exams previously in software advancement pipelines (as opposed to just prior to generation) final results in a superior over-all likelihood of catching regarded code and artifact vulnerabilities and remediating them in a well timed fashion. Having said that, if builders on your own bear the overall burden of running checks, collecting scanner output, and prioritizing vulnerabilities on prime of remediating them, the resulting psychological load and toil is specified to impact the speed to manufacturing. Alternatively, the most effective approach lies in following these guidelines:
- Security really should possess the orchestration and automation of software security tests all through CI and CD pipelines
- Take out the load of deduplicating and prioritizing detected vulnerabilities from builders. As a substitute, security should really make certain developers get a completely processed vulnerability list in a well timed fashion
- Speed up remediation by creating actionable developer-oriented advice for comprehension and resolving each and every vulnerability
 Figure 1: Orchestration of software security exams through the computer software enhancement pipeline
Figure 1: Orchestration of software security exams through the computer software enhancement pipeline
Tenet 3: Keep good governance and guardrails
Because almost everything moves quick in the DevOps planet, it is really uncomplicated to make faults. But even tiny issues or omissions, such as a missed CVE (Widespread Vulnerabilities and Exposures) or an unauthorized configuration modify in a growth pipeline, can come with significant security and compliance risk. For this purpose, the value of thorough governance and stringent guardrails all through the full improvement natural environment can’t be overestimated. If your DevSecOps exercise is effective, you have created it effortless for stakeholders to do the correct issues and challenging for them to do the erroneous issues. This can be achieved with the next steering:
- Implement fantastic-grained Position-primarily based Obtain Management (RBAC) in the course of the growth atmosphere to guarantee good utilization and operation. Typical RBAC is generally based on a one property (part), but good-grained RBAC enables more robust security by having into account numerous properties, these kinds of as time of working day, consumer teams, business hierarchy, etcetera.
- Overlay insurance policies on leading of pipelines to help builders to manage their pipelines and to give security and compliance teams the capacity to call for security checks. The Open up Coverage Agent (OPA) typical is an superb plan-as-code strategy for this.
- Use templates anywhere possible to reduce unforced mistakes that lead to security and compliance risk. Templates should really have security ideal methods, specially relating to the execution of security scans. Use of templates should really be enforced via policies that make certain security scans are carried out.
Tenet 4: Emphasis on securing the computer software offer chain (and not just your individual source code)
The problem of securing present day programs has become progressively complex, largely because of to the huge array of open supply software program (OSS) parts and other 3rd party artifacts that software program producers use to develop their programs. Just about every of these parts introduces new potential vulnerabilities into the end item, which puts the software’s shoppers and individuals at risk. An application’s overall security and compliance risk is a functionality of all the code, persons, devices, and processes that contribute to the improvement and supply of that application’s software artifacts, equally inside of and exterior of an business.

As this kind of, open up supply program artifacts are a desirable goal for cyber attackers, as evidenced by the significant-profile breaches that compromised Solarwinds, Log4j, and Codecov. Compromise just one application developing block, and there is likely to wreak havoc on the tens or hundreds of 1000’s of conclusion consumers of that element. For this rationale, the concentration of DevSecOps ought to broaden beyond the organization’s supply code to the complete software program source chain, which is the SUM Complete of all the code, persons, systems, and processes that contribute to the development and supply of software package artifacts, both equally inside and outside of an firm.
For the critical reason of ensuring the integrity of any application manufactured by the firm, DevSecOps groups must undertake resources and techniques in accordance with the SLSA framework and with Government Order 14028.
Securing the software source chain requires DevSecOps groups to:
- Govern the use of open source software program factors in the course of CI and CD pipelines. This is best obtained through a plan-as-code approach (based mostly on the OPA common), which lets for authoring personalized guidelines that factor in a broad selection of OSS artifact characteristics, these kinds of as edition, license, PURL, and provider, alongside with main indicators of risk. No matter whether the purpose is to assure the good use of open resource libraries or block the use of particular OSS artifacts for security explanations, strong governance is vital.
- Undertake in depth abilities for producing, controlling, and analyzing software program charges of resources (SBOMs) for computer software artifacts. An SBOM is essential for comprehending the elements and dependencies inside an software, which in flip enables corporations to handle software pitfalls properly. Far more and much more program-consuming corporations are necessitating thorough SBOMs from distributors, reliable with Government Get 14028 mandates.
- Produce and confirm SLSA compliance outside of the minimal prerequisites of amount 1. The SLSA framework is a really helpful indicates of shielding in opposition to artifact tampering. It will allow for creating a verifiable document across the offer chain with information that associates identities and programs with the program. This information and facts can be verified and signed during the software development lifecycle. The greater the stage, the stronger the integrity warranty.
- Establish a total chain of custody for all software package artifacts. In the realm of computer software, chain of custody is in depth proof of every thing that transpires to a software artifact throughout enhancement pipelines, like who created or modified the artifact, which security tests it underwent, and what the test results were. Accomplishing a full chain of custody is mainly a functionality of the underlying CI/CD platform as well as integrated pipeline tooling and it is vital for keeping the trustworthiness of software package from improvement to deployment. Owning a thorough software package chain of custody also significantly accelerates vulnerability remediation, which is normally an exhaustive system of manually parsing logs and piecing together incomplete data in tracing the new vulnerability back to impacted software program parts.
Tenet 5: Obtain ‘continuous security’ by automation and AI

DevOps has come to be synonymous with the tactics of continual integration and ongoing deployment, so it stands to explanation that DevSecOps should really end result in constant security. A massive component of DevSecOps accomplishment is becoming able to continue to keep tempo with (and even get ahead of) application improvement velocity. When it invariably usually takes time for a nascent DevSecOps plan to develop agility in addition to usefulness, a important to accelerating DevSecOps maturity is the use of intelligent automation and AI. Listed here are quite a few essential recommendations for how and wherever to apply them:
- Orchestrate security scans throughout pipelines. This is easiest obtained with a platform approach, whereby the fundamental DevOps platform integrates with a wide variety of SAST, SCA, Container, and DAST scanning resources and executes scans when the pipeline is operate. Coverage-as-code governance is one more similar kind of computerized mitigation. For illustration, an OPA coverage can be enforced to fall short a pipeline if particular security conditions is not achieved.
- Automate vulnerability checklist deduplication and prioritization for developers. 1 of the major parts of toil for builders is acquiring to offer with a mountain of unprocessed scanner output knowledge. For the reason of optimizing time-to-remediation for critical vulnerabilities (alongside with preserving developer efficiency and knowledge), automating the system of deduplicating and prioritizing vulnerabilities is a ought to.
- Create remediation steering with AI. To further more increase the speed of remediation and lessen developer toil, providing AI-created explanations for vulnerabilities and prescriptive remediation assistance is a big gain to builders.
Conclusion
Whilst there is no doubt about the criticality of a very effective DevSecOps exercise to software program-generating corporations, there are really few obvious standards on how to establish a person that strengthens overall application security posture without having incorporating toil or degrading the developer knowledge.
The 5 core DevSecOps tenets (together with their respective sets of recommendations) reviewed in this paper help DevSecOps groups to build and maintain a good operational basis. As modern-day DevOps technologies and procedures continue on to speedily evolve, there will constantly be uncharted security issues to tackle. So long as developers, DevOps engineers, and security practitioners operate collectively as a cohesive device, the route to DevSecOps excellence is a great deal clearer. If you are interested in a more deep dive into these ideas, I really encourage you to download the Definitive Manual to Secure Program Shipping.
Identified this article exciting? This report is a contributed piece from 1 of our valued associates. Adhere to us on Twitter and LinkedIn to read through extra exceptional written content we article.
Some areas of this write-up are sourced from:
thehackernews.com

 Streamlining IT Security Compliance Using the Wazuh FIM Capability
Streamlining IT Security Compliance Using the Wazuh FIM Capability