The persistent danger actors behind the SolarMarker information and facts-stealing malware have founded a multi-tiered infrastructure to complicate legislation enforcement takedown initiatives, new findings from Recorded Upcoming display.
“The main of SolarMarker’s operations is its layered infrastructure, which is composed of at least two clusters: a main 1 for active functions and a secondary one particular most likely applied for tests new procedures or focusing on particular regions or industries,” the enterprise stated in a report released very last 7 days.
“This separation boosts the malware’s capacity to adapt and react to countermeasures, building it particularly difficult to eradicate.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
SolarMarker, identified by the names Deimos, Jupyter Infostealer, Polazert, and Yellow Cockatoo, is a refined threat that has exhibited a constant evolution due to the fact its emergence in September 2020. It has the capability to steal details from many web browsers and cryptocurrency wallets, as well as focus on VPN and RDP configurations.

Amongst the leading qualified verticals are schooling, governing administration, healthcare, hospitality, and small and medium-sized enterprises, per details gathered given that September 2023. This involves well known universities, governing administration departments, world resort chains, and health care vendors. A the vast majority of the victims are found in the U.S.
Over the several years, the malware authors have targeted their enhancement efforts on making it a lot more stealthy by means of improved payload dimensions, the use of legitimate Authenticode certificates, novel Windows Registry variations, and the capability to operate it specifically from memory instead than disk.
Infection pathways usually contain hosting SolarMarker on bogus downloader internet sites advertising popular program that can be frequented by a victim either inadvertently or owing to lookup motor optimization (Seo) poisoning, or through a backlink in a destructive email.
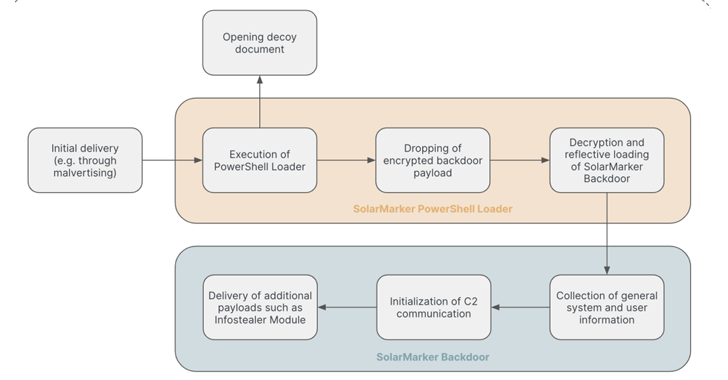
The original droppers choose the type of executables (EXE) and Microsoft Computer software Installer (MSI) data files that, when launched, guide to the deployment of a .NET-based mostly backdoor that’s responsible for downloading added payloads for facilitating information theft.

Alternate sequences leverage the counterfeit installers to drop a respectable application (or a decoy file), even though simultaneously launching a PowerShell loader for offering and executing the SolarMarker backdoor in memory.
SolarMarker attacks around the past calendar year have also involved the supply of a Delphi-primarily based hVNC backdoor known as SolarPhantom that makes it possible for for remotely controlling a target equipment with out their information.
“In recent conditions, SolarMarker’s risk actor has alternated involving Inno Setup and PS2EXE instruments to deliver payloads,” cybersecurity firm eSentire observed in February 2024.
As a short while ago as two months back, a new PyInstaller version of the malware was spotted in the wild propagated working with a dishwasher manual as a decoy, in accordance to a malware researcher who goes by the name Squiblydoo and has extensively documented SolarMarker above the yrs.
There is proof to suggest that SolarMarker is the work of a lone actor of unfamiliar provenance, while prior study from Morphisec has alluded to a doable Russian relationship.

Recorded Future’s investigation into the server configurations joined to the command-and-control (C2) servers has uncovered a multi-tiered architecture that is section of two broad clusters, one of which is possible made use of for screening applications or for focusing on specific locations or industries.
The layered infrastructure contains a set of Tier 1 C2 servers that are in direct make contact with with victim equipment. These servers link to a Tier 2 C2 server via port 443. Tier 2 C2 servers, similarly communicate with Tier 3 C2 servers by means of port 443, and Tier 3 C2 servers persistently hook up to Tier 4 C2 servers through the similar port.
“The Tier 4 server is considered the central server of the procedure, presumably utilized for effectively administering all downstream servers on a lengthy-phrase basis,” the cybersecurity organization said, introducing it also observed the Tier 4 C2 server speaking with a further “auxiliary server” through port 8033.
“Whilst the precise purpose of this server continues to be unfamiliar, we speculate that it is utilised for monitoring, probably serving as a health and fitness test or backup server.”
Found this report fascinating? Observe us on Twitter and LinkedIn to study extra special articles we post.
Some parts of this post are sourced from:
thehackernews.com

 Five Core Tenets Of Highly Effective DevSecOps Practices
Five Core Tenets Of Highly Effective DevSecOps Practices