A new attack marketing campaign dubbed CLOUD#REVERSER has been observed leveraging legit cloud storage solutions like Google Push and Dropbox to phase malicious payloads.
“The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently includes command-and-management-like functions by applying Google Travel and Dropbox as staging platforms to control file uploads and downloads,” Securonix scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker Information.
“The scripts are intended to fetch information that match certain patterns, suggesting they are waiting for commands or scripts placed in Google Drive or Dropbox.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The commencing place of the attack chain is a phishing email bearing a ZIP archive file, which is made up of an executable that masquerades as a Microsoft Excel file.

In an intriguing twist, the filename can make use of the concealed right-to-remaining override (RLO) Unicode character (U+202E) to reverse the order of the people that appear soon after that character in the string.
As a end result, the filename “RFQ-101432620247fl*U+202E*xslx.exe” is exhibited to the target as “RFQ-101432620247flexe.xlsx,” hence deceiving them into imagining that they are opening an Excel doc.
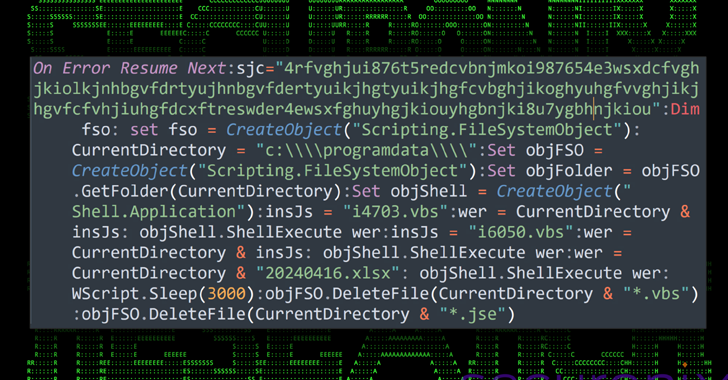
The executable is made to drop a total of 8 payloads, including a decoy Excel file (“20240416.xlsx”) and a seriously obfuscated Visual Primary (VB) Script (“3156.vbs”) which is liable for displaying the XLSX file to the person to manage the ruse and launch two other scripts named “i4703.vbs” and “i6050.vbs.”

Both of those scripts are applied to set up persistence on the Windows host by means of a scheduled process by masquerading them as a Google Chrome browser update endeavor to stay clear of increasing purple flags. That reported, the scheduled jobs are orchestrated to operate two exclusive VB scripts referred to as “97468.tmp” and “68904.tmp” each moment.
Every single of these scripts, in convert, is employed to run two diverse PowerShell scripts “Tmp912.tmp” and “Tmp703.tmp,” which are made use of to hook up to an actor-controlled Dropbox and Google Travel account and obtain two much more PowerShell scripts referred to as “tmpdbx.ps1” and “zz.ps1”
The VB scripts are then configured to run the newly downloaded PowerShell scripts and fetch additional data files from the cloud expert services, including binaries that could be executed depending on the process policies.
“The late-phase PowerShell script zz.ps1 has features to download files from Google Generate based on certain requirements and preserve them to a specified route on the area program within the ProgramData listing,” the scientists stated.
The fact that the two the PowerShell scripts are downloaded on-the-fly indicates they could be modified by the threat actors at will to specify the documents that can be downloaded and executed on the compromised host.

Also downloaded by way of 68904.tmp is one more PowerShell script that’s able of downloading a compressed binary and functioning it specifically from memory in purchase to maintain network connection to the attacker’s command-and-regulate (C2) server.
The improvement is when all over again a signal that threat actors are significantly misusing respectable products and services to their benefit and fly under the radar.
“This technique follows a widespread thread wherever menace actors manage to infect and persist onto compromised devices while preserving to blend into normal background network sounds,” the scientists reported.
“By embedding malicious scripts in seemingly innocuous cloud platforms, the malware not only makes sure sustained obtain to qualified environments but also makes use of these platforms as conduits for information exfiltration and command execution.”
Identified this short article attention-grabbing? Adhere to us on Twitter and LinkedIn to examine extra exclusive content we post.
Some pieces of this report are sourced from:
thehackernews.com

 SolarMarker Malware Evolves to Resist Takedown Attempts with Multi-Tiered Infrastructure
SolarMarker Malware Evolves to Resist Takedown Attempts with Multi-Tiered Infrastructure