A peer-to-peer Golang botnet has resurfaced just after a lot more than a 12 months to compromise servers belonging to entities in the healthcare, schooling, and government sectors inside a span of a month, infecting a total of 1,500 hosts.
Dubbed FritzFrog, “the decentralized botnet targets any system that exposes an SSH server — cloud occasions, knowledge middle servers, routers, and so forth. — and is capable of running any destructive payload on contaminated nodes,” Akamai scientists reported in a report shared with The Hacker Information.
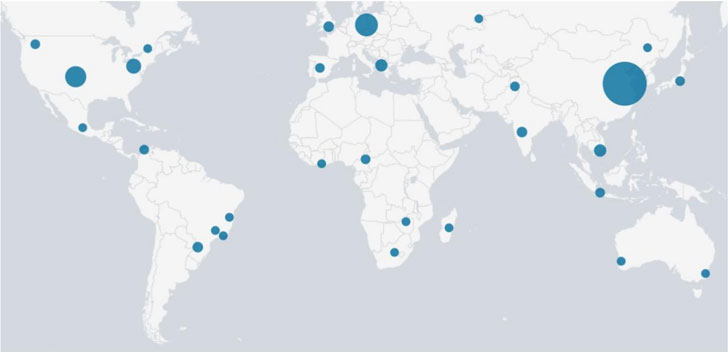
The new wave of attacks commenced in early December 2021, only to decide up tempo and sign-up a 10x expansion in its an infection level in a month’s time, when peaking at 500 incidents per day in January 2022. The cybersecurity firm reported it detected infected machines in a European tv channel network, a Russian producer of health care gear, and multiple universities in East Asia.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
FritzFrog was initial documented by Guardicore in August 2020, elaborating the botnet’s proficiency to strike and infect extra than 500 servers spanning across Europe and the U.S. considering the fact that January that calendar year. A substantial focus of the new bacterial infections, on the other hand, are located in China.
“Fritzfrog depends on the capacity to share information about the network, both to infect new devices and run malicious payloads, this kind of as the Monero crypto miner,” security researcher Ophir Harpaz noticed in 2020.
The botnet’s peer-to-peer (P2P) architecture makes it resilient in that each compromised device in the dispersed network can act as a command-and-command (C2) server as opposed to a one, centralized host. What is additional, the reappearance of the botnet has been accompanied by new additions to its performance, which includes the utilization of a proxy network and the concentrating on of WordPress servers.
The an infection chain propagates more than SSH to fall a malware payload that then executes guidelines gained from the C2 server to run added malware binaries as properly as obtain process information and data files, before exfiltrating them back to the server.
FritzFrog is notable for the truth that the P2P protocol employed is wholly proprietary. Whilst previously variations of the malware procedure masqueraded as “ifconfig” and “nginx,” the new variants attempt to conceal their activities beneath the names “apache2” and “php-fpm.”
Other new attributes integrated into the malware include the use of protected copy protocol (SCP) to copy itself to the distant server, a Tor proxy chaining to mask outgoing SSH connections, an infrastructure to keep track of WordPress servers for adhere to-on attacks, and a blocklist system to keep away from infecting very low-stop methods this sort of as Raspberry Pi equipment.
“A person IP in the blocklist is from Russia. It has several open ports and a extensive checklist of unpatched vulnerabilities, so it may be a honeypot,” the scientists explained. “On top of that, a second entry details to an open up-supply botnet sinkhole. These two entries suggest that the operators are attempting to evade detection and evaluation.”
The inclusion of the SCP attribute may possibly also have offered the first clue as to the malware’s origins. Akamai pointed out that the library, written in Go, has been shared on GitHub by a user found in the Chinese city of Shanghai.
A 2nd piece of data linking the malware to China stems from the simple fact that just one of the new wallet addresses utilized for crypto mining was also utilized as part of the Mozi botnet campaign, whose operators ended up arrested in China previous September.
“These details of evidence, whilst not damning, lead us to believe that a possible url exists to an actor operating in China, or an actor masquerading as Chinese,” the scientists concluded.
Found this post attention-grabbing? Adhere to THN on Facebook, Twitter and LinkedIn to go through a lot more exclusive written content we article.
Some elements of this article are sourced from:
thehackernews.com



 PHP Everywhere Bugs Put 30K+ WordPress Sites at Risk of RCE
PHP Everywhere Bugs Put 30K+ WordPress Sites at Risk of RCE