Shutterstock
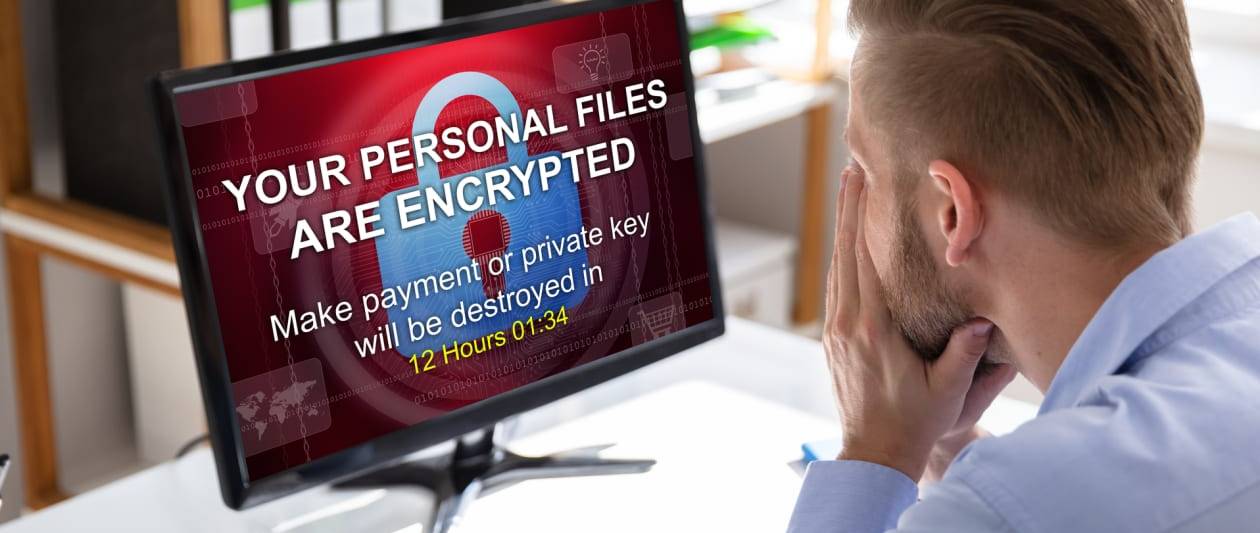
Mid-sized corporations are now the most important focus on of ransomware gangs, with hackers looking for to steer clear of the general public scrutiny that comes with heading just after significant-profile public expert services or properly-identified brands.
The National Cyber Security Centre (NCSC), along with its US and Australian counterparts, said criminals are no more time engaging in the sort of “massive-game looking” that have resulted in environment-large press coverage in the latest several years, as outlined in a joint advisory published on Wednesday.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The FBI have noticed that attacks on Colonial Pipeline, JBS Foodstuff, and Kaseya in 2021 in individual, led to a recognizable change in conduct.
“Big-game” attacks had also been noticed in Australia and the UK around the training course of the 12 months, with the NCSC describing the major victims of 2021 as “businesses, charities, the legal occupation, and general public expert services in the Instruction, Community Authorities, and Wellness Sectors”.
Nevertheless, hackers are now opting to focus on mid-sized organisations in an hard work to reduce public – and usually international – scrutiny, the report uncovered. It comes immediately after a latest Mitre-Harris Poll survey observed that practically nine in ten Americans believe that a ransomware attack need to be handled as an act of terrorism, which could most likely direct to increased prospects of the involvement of regulation enforcement.
Making use of cyber prison expert services-for-use has become a well-known tactic among hackers, along with phishing emails and the exploitation of remote desktop protocols (RDP) as nicely as software program vulnerabilities.
The organizations are urging organisations to retain all functioning techniques and application up to date, to protected and monitor RDPs, and raise their use of multi-factor authentication (MFA) – a safety method which is regarded to lessen account breaches by 50%.
Staff should also be sufficiently ready for likely attacks with the assist of consumer coaching programmes and phishing exercises, the advisory warned.
The shift away from significant-profile targets has been predicted by a quantity of cyber security researchers adhering to the Colonial Pipeline attack. In July 2021, Quest senior director of solution management Paul Robichaux advised IT Pro that “ransomware gangs that bring in also significantly notice by attacking the mistaken targets are likely to provide the heat on them selves and get set out of company as a result of law enforcement action”.
For this reason, the “smarter” hackers “will decide their targets more carefully, equally by sector and by geography”.
“The smartest will emphasis only on territories where by there is not likely to be any significant regulation enforcement or intelligence community response and aim all their exercise there,” he included.
Some pieces of this write-up are sourced from:
www.itpro.co.uk

 FritzFrog P2P Botnet Attacking Healthcare, Education and Government Sectors
FritzFrog P2P Botnet Attacking Healthcare, Education and Government Sectors