Processing alerts rapidly and successfully is the cornerstone of a Security Functions Centre (SOC) professional’s job. Danger intelligence platforms can drastically boost their capability to do so. Let’s obtain out what these platforms are and how they can empower analysts.
The Problem: Warn Overload
The modern day SOC faces a relentless barrage of security alerts generated by SIEMs and EDRs. Sifting by these alerts is both of those time-consuming and useful resource-intense. Examining a potential danger normally needs searching throughout various resources before acquiring conclusive proof to confirm if it poses a serious risk. This process is further more hampered by the disappointment of paying precious time investigating artifacts that in the long run transform out to be fake positives.
As a outcome, a major part of these situations stay uninvestigated. This highlights a critical problem: finding necessary information and facts linked to distinctive indicators immediately and correctly. Threat data platforms provide a resolution. These platforms empower you to glance up any suspicious URL, IP, or other indicator and obtain fast insights into its likely risk. A single these platform is Risk Intelligence Lookup from ANY.Operate.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Threat Intelligence Platforms to the Rescue
Specialized platforms for SOC investigations leverage their databases of menace facts, aggregated from assorted resources. Consider, for illustration, ANY.RUN’s Risk Intelligence Lookup (TI Lookup). This system collects Indicators of Compromise (IOCs) from tens of millions of interactive assessment sessions (tasks) done inside of the ANY.Run sandbox.
The system provides an further dimension of threat data: logs of procedures, registry and network exercise, command line contents, and other process data created through sandbox evaluation periods. Users can then search for appropriate specifics throughout these fields.
Danger Intelligence Platforms Positive aspects
Further Visibility into Threats
Alternatively of relying on scattered info sources, these kinds of platforms provide a single level of obtain to lookup for IOCs throughout many information factors. This includes URLs, file hashes, IP addresses, logged occasions, command traces, and registries, making it possible for for additional comprehensive menace identification and investigation.
Speedier Warn Investigations
When a security incident takes place, time is of the essence. TI platforms assistance get relevant menace intelligence details rapidly, enabling a further knowledge of the attack’s character, impacted devices, and compromise scope. This can drastically speed up and make improvements to response attempts.
Proactive Menace Searching
Threat intelligence platforms empower teams to actively hunt for known IOCs related with unique malware households. This proactive approach can support uncover hidden threats prior to they escalate into significant incidents.
They can offer obtain to data that may expose prospective vulnerabilities connected with regarded threats. This info can inform risk assessments and help organizations prioritize security initiatives based on the most pressing risks.
Threat Examination and Final decision-Producing
Armed with detailed insights into malware conduct, groups can more precisely evaluate threats and make informed choices about containment, remediation, and upcoming preventative steps. This continual discovering cycle strengthens the overall security posture and group competency.
Danger Intelligence System Question Examples
Exploring with Particular person Indicators

Picture you suspect a compromised program in just your network is downloading destructive documents. You pinpoint a specific IP address as the opportunity supply and make a decision to look into even further. Enter the IP tackle into the lookup bar of a menace intelligence system. Promptly, the platform flags the handle as malicious and linked to the Remcos malware, providing details on domains, ports, and even documents connected with this IP.
It also supplies entry to assessment sessions where this IP address was concerned and lists Practices, Approaches, & Procedures (TTPs) utilized by malware in these classes.

You can analyze every single session in detail by simply just clicking on it. The system will just take you to the session’s webpage in the ANY.Run sandbox, the place you will be equipped to investigate all the procedures, connections, and registry activity, as very well as obtain the malware’s config and IOCs or download a thorough risk report.
Versatile Lookup with Wildcards
A further handy aspect of danger intelligence platforms like TI Lookup is the skill to submit wildcards and put together queries.
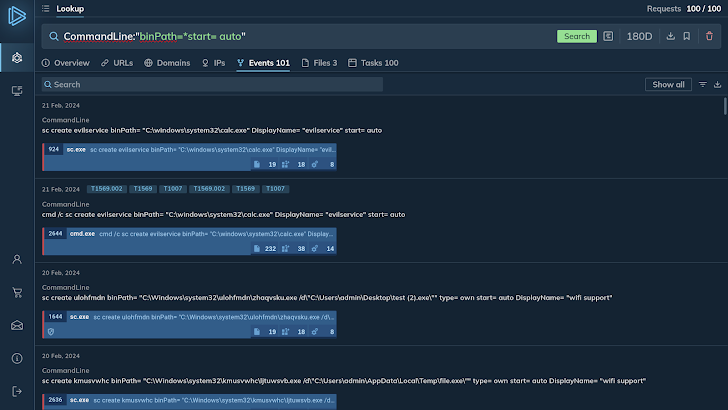
For occasion, the query “binPath=*start= car” utilizes the asterisk wildcard and lookups for any command line with “binPath=” adopted by any people that stop with “start= auto”.
The platform returns a hundred classes the place the exact fragment appeared. A nearer evaluation of the look for results indicates that this certain command line artifact is characteristic of the Tofsee malware.
Merged Look for Requests
One more choice for conducting an investigation is to pool collectively all offered indicators and post them to the menace intelligence system to discover all circumstances where by these standards show up collectively.
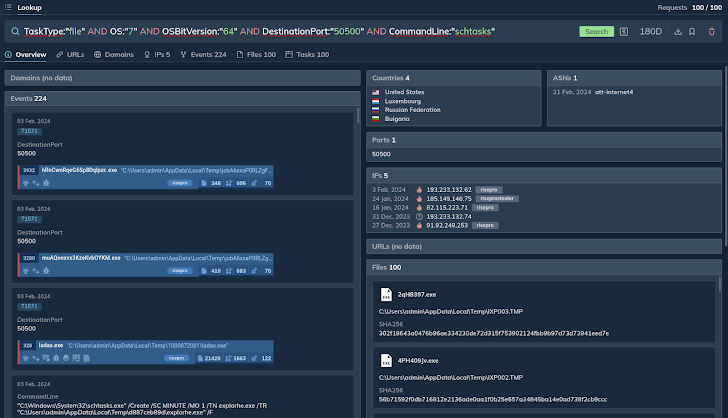
For case in point, you can construct a question that lookups for all tasks (periods) categorized as “file,” run on Windows 7, with a 64-little bit running method, connecting to port 50500 and containing the string “schtasks” in the command line.
The system then identifies a lot of periods that satisfy the specified requirements and additionally gives a record of IPs tagged with “RisePro,” highlighting the malware dependable.
Check out Threat Intelligence Lookup
Menace Intelligence Lookup from ANY.Operate allows you investigate threats with precision. Evaluate procedures, documents, network exercise, and a lot more. Refine your look for with 30+ fields, like IPs, domains, logged activities, and MITRE procedures. Blend parameters for holistic understanding. Use wildcard queries to increase your attain.
Request a trial to receive 50 free of charge requests to investigate the system.
Identified this article intriguing? This write-up is a contributed piece from just one of our valued associates. Stick to us on Twitter and LinkedIn to go through a lot more unique written content we article.
Some areas of this write-up are sourced from:
thehackernews.com


 Five Eyes Agencies Expose APT29’s Evolving Cloud Attack Tactics
Five Eyes Agencies Expose APT29’s Evolving Cloud Attack Tactics