An “intricately developed” distant access trojan (RAT) referred to as Xeno RAT has been made accessible on GitHub, creating it readily available to other actors at no additional charge.
Created in C# and appropriate with Windows 10 and Windows 11 working devices, the open-resource RAT comes with a “in depth set of characteristics for distant process management,” in accordance to its developer, who goes by the identify moom825.
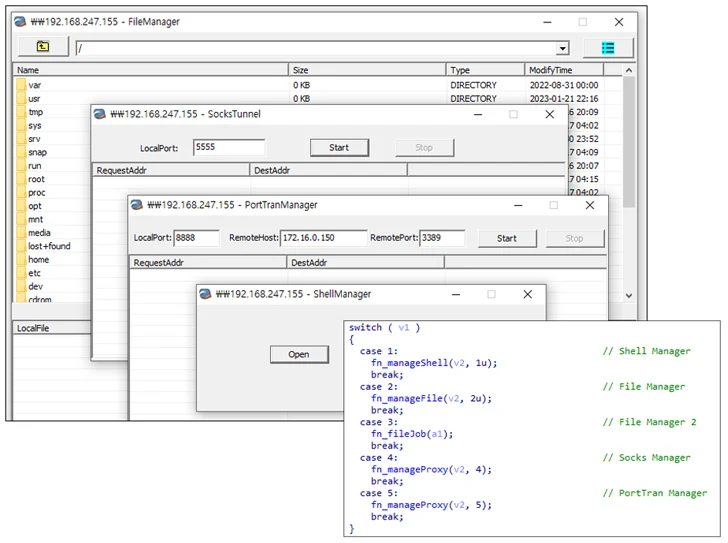
It includes a SOCKS5 reverse proxy and the capacity to report authentic-time audio, as properly as include a hidden virtual network computing (hVNC) module along the strains of DarkVNC, which enables attackers to acquire remote access to an infected pc.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Xeno RAT is designed solely from scratch, guaranteeing a unique and personalized technique to distant obtain equipment,” the developer states in the venture description. An additional notable component is that it has a builder that permits the creation of bespoke variants of the malware.

It can be worth noting that the moom825 is also the developer of a further C#-primarily based RAT identified as DiscordRAT 2., which has been distributed by danger actors in just a malicious npm offer named node-conceal-console-windows, as disclosed by ReversingLabs in Oct 2023.
Cybersecurity organization Cyfirma, in a report published past week, explained it observed Xeno RAT currently being disseminated through the Discord articles delivery network (CDN), the moment once more underscoring how a increase in cost-effective and freely readily available malware is driving an improve in campaigns using RATs.

“The primary vector in the type of a shortcut file, disguised as a WhatsApp screenshot, acts as a downloader,” the organization explained. “The downloader downloads the ZIP archive from Discord CDN, extracts, and executes the next stage payload.”
The multi-stage sequence leverages a system called DLL aspect-loading to launch a malicious DLL, when at the same time using techniques to create persistence and evade examination and detection.

The growth arrives as the AhnLab Security Intelligence Middle (ASEC) exposed the use of a Gh0st RAT variant known as Nood RAT that’s employed in attacks focusing on Linux systems, allowing adversaries to harvest delicate facts.
“Nood RAT is a backdoor malware that can obtain instructions from the C&C server to complete destructive actions such as downloading destructive data files, thieving systems’ inner information, and executing commands,” ASEC explained.
“Even though basic in type, it is equipped with the encryption aspect to stay clear of network packet detection and can obtain instructions from danger actors to have out many malicious actions.”
Located this posting exciting? This report is a contributed piece from one particular of our valued associates. Abide by us on Twitter and LinkedIn to go through a lot more special content we put up.
Some sections of this post are sourced from:
thehackernews.com


 From Alert to Action: How to Speed Up Your SOC Investigations
From Alert to Action: How to Speed Up Your SOC Investigations