Deep fakes are anticipated to develop into a a lot more notable attack vector. Here’s how to recognize them.
What are Deep Fakes?
A deep pretend is the act of maliciously replacing authentic pictures and videos with fabricated kinds to execute details manipulation. To develop visuals, video and audio that are substantial good quality enough to be utilised in deep fakes, AI and ML are expected. These kinds of use of AI, ML and image substitution are as opposed to other types of information manipulation, which use much less serious manipulation methods, like misrepresentation of info, isolating areas of the details or modifying it in a misleading fashion. Etay Maor, Senior Director of Security Tactic at Cato Networks provides “To add issues, the the latest enhancements and accessibility to AI generated text, these kinds of as GPT3, have already been utilized in combination with deepfakes (as a proof of notion) to build interactive, human searching dialogue bots”
What Do Deep Fakes Seem Like?
Deep fakes appear in all shapes and measurements. Some are more simple and some are a lot more highly developed. Some of the most preferred examples of deep fakes are:

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Experience Swap
Confront swapping is the act of replacing the experience in a video clip or image from a single human being to one more. Experience swapping calls for dedicated software program, but it does not have to be dependent on state-of-the-art technology – currently one particular can even find cellular apps that aid face swapping. Encounter swapping that is accessible in mobile applications is ordinarily restricted to simple use situations, like swapping amongst the user’s images and actors’ faces in motion picture scenes.

Much more highly developed confront swapping does exist, but it demands more product schooling and code, and – as a final result – GPUs, which is pricey and source-intense. An example of a a lot more advanced face swapping deep faux can be see in this movie, in which Tom Cruise is swapped with the presenter’s confront:
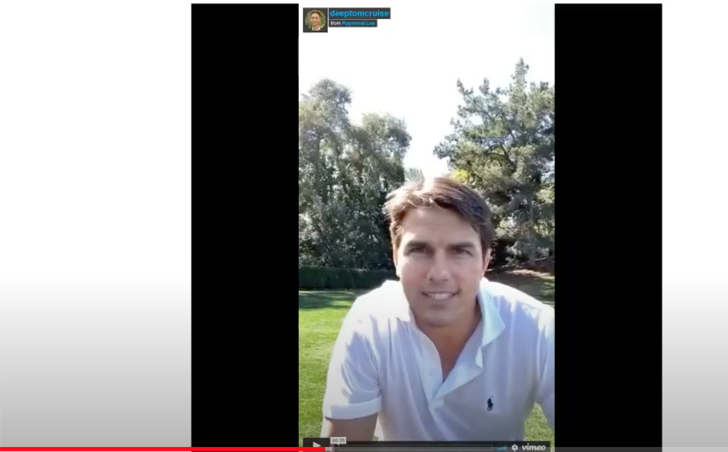
This Tom Cruise encounter swap needed two hours of schooling on a GPU as perfectly as times of qualified movie modifying post-processing. This may well sound like a good deal, but it was also considered a simpler swap than other people, because the presenter experienced a identical haircut to Cruise and can impersonate his voice, which implies fewer instruction and post-processing were essential.
Puppet Master (Lip Sync)
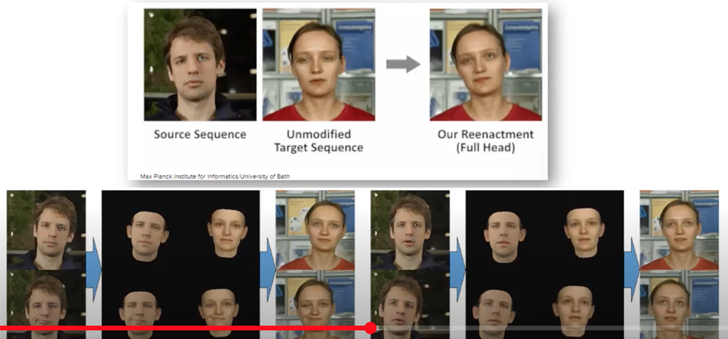
The ‘Puppet Master’ deep faux is a system in which the picture of a person’s mouth actions are manipulated, earning it appear to be like the man or woman is stating a thing they have not essentially claimed. In comparison to confront swapping, which trains a model on the new, swapped encounter, ‘Puppet Master’ trains a model on the deal with of the unique graphic, and specially on the mouth movements.
Here’s what it seems to be like:
[warning – explicit language]

The technology behind the ‘Puppet Master’ is primarily based on synthesizing the mask, i.e. the original graphic, and positioning it on major of the model of the individual who is impersonating and lip syncing them.
Audio
The 3rd outstanding style of deep bogus is audio-based. Audio deep fakes are audio documents that take a actual person’s voice and make it appears like they are saying some thing they experienced under no circumstances said. Audio deep fakes are created by getting audio data files, allocating annotations to the appears, teaching an ML design centered on the annotations to affiliate appears with text and then generating a new audio file.
Here is what is sounds like:
Deep Fakes vs. Low cost Fixes
Not all modified photographs or audio are deep fakes. Though deep fakes are media synthesized or modified applying AI, cheap fixes are media synthesized or modified using reduced-tech procedures, which are effortless to place. They usually have distortions and have been clearly manipulated. Here’s what a inexpensive fix seems to be like:
The Cyber Risk of Deep Fakes
Deep fakes have develop into much more practical and available and they are also a lot quicker to generate than ever before. This can make them a effective software for weaponization. As a result, they pose a risk for firms and for nations. They can be made use of for cyber criminal offense, social engineering, fraud, by threat actor nations to affect foreign functions, and a lot more.
For example, deep bogus was utilised to mimic a CEO’s voice and persuade an government to wire $243,000 to a fraud account. Etay Maor of Cato Networks “Business enterprise email comprise and phishing attacks are turning into more durable and more durable to detect based mostly on simple analysis of the language applied. There is a require for a holistic strategy, such as the one particular presented by a single seller SASE resolution, that can detect the attack at various multiple choke points and not depend on isolated level solutions that are doomed to fall short”. In a further scenario, a deep fake was introduced as proof in a little one custody circumstance.
Deep fakes can also be utilized for spreading disinformation, i.e fake distribution of details to affect public opinion or obscure the truth of the matter. For illustration, deep fakes could be utilized to impersonate earth leaders and ignite an attack, or to impersonate a CEO and manipulate a firm’s stock rate. In other cases, deep fakes enable plausible deniability, in which individuals could deny all sources of media by declaring they are deep fakes, which generates a social breach of belief.
At last, deep faux can be employed for defamation, i.e harming someone’s good standing. For illustration, by creating revenge porn.
How to Detect Deep Fakes
There are two main kinds of methods for correctly detecting deep fakes:
- Lower-level detection techniques
- Higher-level detection approaches
Low-stage Detection Procedures
Low-degree detection strategies count on ML designs that are skilled to recognize artifacts or pixellations that ended up launched by the deep pretend era course of action. These artifacts may possibly be imperceptible to the human eye, but the types, which had been skilled on genuine illustrations or photos and deep phony visuals, are capable to detect them.

Substantial-degree Detection Approaches
High-level detection strategies use versions that can detect semantically significant options. These contain unnatural actions, like blinking, head-pose or exclusive mannerisms, and phoneme-viseme mismatches.
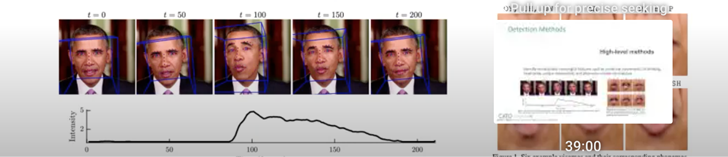
Today, these detection methods are viewed as exact. Nonetheless, as deep bogus technology increases and turns into additional refined, they are envisioned to develop into less successful and will need to have to be updated and enhanced. In addition to these approaches, each individual a single of us can assistance detect deep fakes by verifying the media resource of films and visuals we acquire.
To find out additional about diverse styles of cybersecurity attacks and how to protect against them, Cato Networks’ Cyber Security Masterclass sequence is obtainable for your viewing.
Located this short article interesting? Comply with us on Twitter and LinkedIn to read a lot more special content material we put up.
Some elements of this short article are sourced from:
thehackernews.com


 Core Members of DoppelPaymer Ransomware Gang Targeted in Germany and Ukraine
Core Members of DoppelPaymer Ransomware Gang Targeted in Germany and Ukraine