A under no circumstances-right before-witnessed elaborate malware is concentrating on company-quality routers to covertly spy on victims in Latin America, Europe, and North America at minimum due to the fact July 2022.
The elusive campaign, dubbed Hiatus by Lumen Black Lotus Labs, has been located to deploy two destructive binaries, a distant obtain trojan dubbed HiatusRAT and a variant of tcpdump that makes it probable to capture packet seize on the goal system.
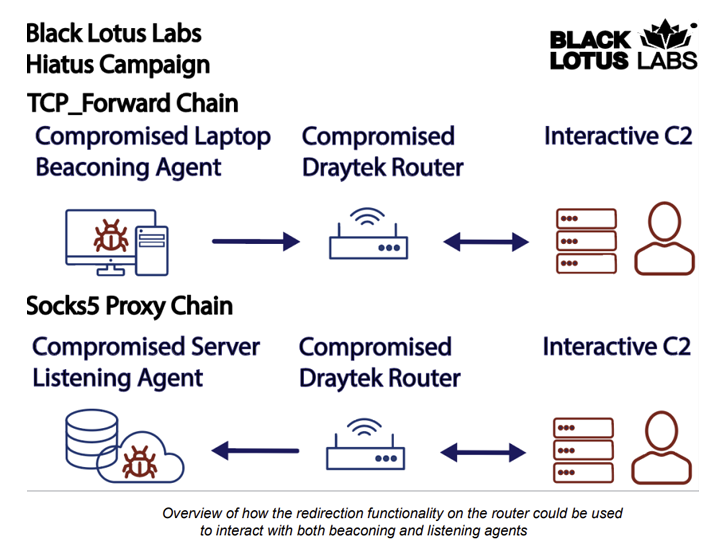
“After a qualified method is infected, HiatusRAT allows the risk actor to remotely interact with the technique, and it utilizes prebuilt functionality […] to change the compromised machine into a covert proxy for the menace actor,” the company stated in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The packet-capture binary enables the actor to observe router targeted traffic on ports connected with email and file-transfer communications.”
The menace cluster primarily singles out conclude-of-existence (EoL) DrayTek Vigor router models 2960 and 3900, with somewhere around 100 internet-uncovered gadgets compromised as of mid-February 2023. Some of the impacted sector verticals include things like prescription drugs, IT solutions/consulting firms, and municipal federal government, amongst some others.
Curiously, this represents only a compact portion of the 4,100 DrayTek 2960 and 3900 routers that are publicly obtainable over the internet, elevating the possibility that “the danger actor is intentionally maintaining a negligible footprint to limit their exposure.”
Offered that the impacted products are high-bandwidth routers that can simultaneously help hundreds of VPN connections, it’s getting suspected that the aim is to spy on targets and set up a stealthy proxy network.
“These products generally stay outdoors the common security perimeter, which indicates they ordinarily are not monitored or current,” Mark Dehus, director of threat intelligence for Lumen Black Lotus Labs, stated. “This helps the actor build and manage extended-phrase persistence without detection.”
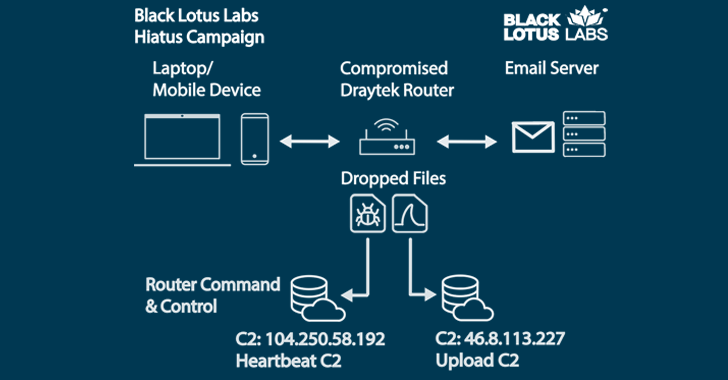
The precise preliminary entry vector utilised in the attacks is mysterious, but a profitable breach is followed by the deployment of a bash script that downloads and executes HiatusRAT and a packet-seize binary.
HiatusRAT is feature-rich and can harvest router facts, managing processes, and speak to a remote server to fetch documents or operate arbitrary commands. It truly is also capable of proxying command-and-management (C2) targeted visitors by means of the router.
Discover the Most recent Malware Evasion Practices and Prevention Strategies
Ready to bust the 9 most hazardous myths about file-based attacks? Be a part of our future webinar and grow to be a hero in the battle in opposition to affected person zero infections and zero-day security functions!
RESERVE YOUR SEAT
The use of compromised routers as proxy infrastructure is likely an endeavor to obfuscate the C2 functions, the scientists mentioned.
The findings appear a lot more than 6 months after Lumen Black Lotus Labs also shed light-weight on an unrelated router-targeted malware marketing campaign that applied a novel trojan known as ZuoRAT.
“The discovery of Hiatus confirms that actors are continuing to go after router exploitation,” Dehus mentioned. “These campaigns reveal the need to have to safe the router ecosystem, and routers need to be regularly monitored, rebooted, and up to date, whilst conclude-of-life equipment need to be replaced.”
Located this posting fascinating? Observe us on Twitter and LinkedIn to go through extra distinctive information we publish.
Some components of this posting are sourced from:
thehackernews.com

 From Disinformation to Deep Fakes: How Threat Actors Manipulate Reality
From Disinformation to Deep Fakes: How Threat Actors Manipulate Reality