Bogus installers for Adobe Acrobat Reader are staying used to distribute a new multi-purposeful malware dubbed Byakugan.
The starting up level of the attack is a PDF file penned in Portuguese that, when opened, demonstrates a blurred image and asks the victim to click on on a backlink to obtain the Reader software to perspective the articles.
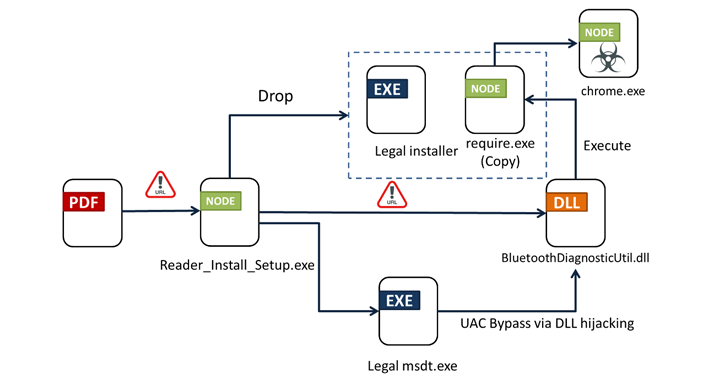
In accordance to Fortinet FortiGuard Labs, clicking the URL prospects to the shipping of an installer (“Reader_Install_Set up.exe”) that activates the an infection sequence. Particulars of the marketing campaign were first disclosed by the AhnLab Security Intelligence Center (ASEC) past month.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The attack chain leverages methods like DLL hijacking and Windows Person Access Manage (UAC) bypass to load a malicious dynamic-hyperlink library (DLL) file named “BluetoothDiagnosticUtil.dll,” which, in switch, masses unleashes the ultimate payload. It also deploys a authentic installer for a PDF reader like Wondershare PDFelement.
The binary is outfitted to collect and exfiltrate system metadata to a command-and-command (C2) server and drop the most important module (“chrome.exe”) from a distinctive server that also acts as its C2 for getting documents and commands.
“Byakugan is a node.js-centered malware packed into its executable by pkg,” security researcher Pei Han Liao mentioned. “In addition to the principal script, there are quite a few libraries corresponding to capabilities.”

This incorporates setting up persistence, checking the victim’s desktop employing OBS Studio, capturing screenshots, downloading cryptocurrency miners, logging keystrokes, enumerating and uploading information, and grabbing details saved in web browsers.
“There is a developing pattern to use both of those clean and destructive parts in malware, and Byakugan is no exception,” Fortinet claimed. “This approach raises the total of sound created for the duration of investigation, generating exact detections additional tricky.”
The disclosure comes as ASEC unveiled a new campaign that propagates the Rhadamanthys data stealer below the guise of an installer for groupware.
“The risk actor established a pretend site to resemble the initial internet site and exposed the site to the users applying the advertisement function in research engines,” the South Korean cybersecurity firm explained. “The malware in distribution employs the indirect syscall approach to cover from the eyes of security answers.”
It also follows a discovery that a manipulated model of Notepad++ is staying employed by unidentified danger actors to propagate the WikiLoader malware (aka WailingCrab).
Located this post attention-grabbing? Stick to us on Twitter and LinkedIn to go through a lot more special articles we submit.
Some pieces of this article are sourced from:
thehackernews.com

 New Wave of JSOutProx Malware Targeting Financial Firms in APAC and MENA
New Wave of JSOutProx Malware Targeting Financial Firms in APAC and MENA