Monetary corporations in the Asia-Pacific (APAC) and Middle East and North Africa (MENA) are staying specific by a new model of an “evolving menace” termed JSOutProx.
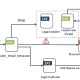
“JSOutProx is a refined attack framework utilizing equally JavaScript and .NET,” Resecurity claimed in a complex report printed this week.
“It employs the .NET (de)serialization function to interact with a main JavaScript module jogging on the victim’s device. After executed, the malware permits the framework to load various plugins, which carry out more destructive routines on the target.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Initial identified in December 2019 by Yoroi, early attacks distributing JSOutProx have been attributed to a risk actor tracked as Solar Spider. The operations keep track of history of placing banking companies and other major corporations in Asia and Europe.
In late 2021, Rapid Mend Security Labs detailed attacks leveraging the distant access trojan (RAT) to single out workforce of compact finance financial institutions from India. Other marketing campaign waves have taken intention at Indian government institutions as far back again as April 2020.

Attack chains are recognised to leverage spear-phishing e-mail bearing malicious JavaScript attachments masquerading as PDFs and ZIP archives containing rogue HTA information to deploy the greatly obfuscated implant.
“This malware has various plugins to complete numerous functions these kinds of as exfiltration of details, performing file method functions,” Fast Mend noted [PDF] at the time. “Apart from that, it also has many procedures with offensive capabilities that carry out numerous functions.”
The plugins let it to harvest a huge variety of information from the compromised host, management proxy settings, seize clipboard articles, accessibility Microsoft Outlook account information, and get a person-time passwords from Symantec VIP. A one of a kind element of the malware is its use of the Cookie header area for command-and-management (C2) communications.
JSOutProx also stands for the truth that it’s a completely practical RAT carried out in JavaScript.
“JavaScript simply just does not offer you as substantially flexibility as a PE file does,” Fortinet FortiGuard Labs mentioned in a report released in December 2020, describing a campaign directed from governmental financial and monetary sectors in Asia.
“Having said that, as JavaScript is utilised by lots of web-sites, it seems to most buyers as benign, as folks with standard security awareness are taught to steer clear of opening attachments that conclude in .exe. Also, since JavaScript code can be obfuscated, it easily bypasses antivirus detection, enabling it to filter by way of undetected.”
The latest set of attacks documented by Resecurity entails using bogus SWIFT or MoneyGram payment notifications to trick email recipients into executing the destructive code. The activity is explained to have witnessed a spike setting up February 8, 2024.
The artifacts have been observed hosted on GitHub and GitLab repositories, which have given that been blocked and taken down.
“At the time the destructive code has been productively sent, the actor removes the repository and creates a new just one,” the cybersecurity firm reported. “This tactic is possible linked to the actor employs to manage multiple malicious payloads and differentiate targets.”

The specific origins of the e-crime group powering the malware are presently unidentified, even though the victimology distribution of the attacks and the sophistication of the implant alludes to them originating from China or affiliated with it, Resecurity posited.
The development arrives as cyber criminals are promoting on the dark web new program termed GEOBOX that repurposes Raspberry Pi units for conducting fraud and anonymization.
Provided for only $80 for each thirty day period (or $700 for a lifetime license), the software permits the operators to spoof GPS locations, emulate distinct network and application settings, mimic settings of recognised Wi-Fi obtain factors, as effectively as bypass anti-fraud filters.
This sort of instruments could have really serious security implications as they open up the door to a wide spectrum of crimes like condition-sponsored attacks, corporate espionage, dark web market place functions, fiscal fraud, anonymous distribution of malware, and even obtain to geofenced content material.
“The relieve of accessibility to GEOBOX raises considerable considerations in the cybersecurity neighborhood about its potential for widespread adoption amid a variety of menace actors,” Resecurity stated.
Located this post attention-grabbing? Follow us on Twitter and LinkedIn to go through more exceptional written content we put up.
Some elements of this post are sourced from:
thehackernews.com


 Researchers Identify Multiple China Hacker Groups Exploiting Ivanti Security Flaws
Researchers Identify Multiple China Hacker Groups Exploiting Ivanti Security Flaws