Tibetan, Uyghur, and Taiwanese people today and businesses are the targets of a persistent marketing campaign orchestrated by a danger actor codenamed EvilBamboo to collect delicate information.
“The attacker has produced faux Tibetan internet websites, alongside with social media profiles, probable utilised to deploy browser-primarily based exploits against qualified end users,” Volexity security researchers Callum Roxan, Paul Rascagneres, and Thomas Lancaster explained in a report revealed past 7 days.
“Partly via impersonating present popular communities, the attacker has crafted communities on on the internet platforms, this kind of as Telegram, to support in distribution of their malware.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
EvilBamboo, formerly tracked by the cybersecurity business less than the title Evil Eye, has been connected to various attack waves considering that at minimum 2019, with the threat actor leveraging watering hole attacks to supply spy ware targeting Android and iOS equipment. It is also known as Earth Empusa and POISON CARP.

The intrusions directed from the Apple mobile working system leveraged a then-zero-working day vulnerability in the WebKit browser motor that was patched by Apple in early 2019 to deliver a spyware strain identified as Sleeplessness. Meta, in March 2021, said it detected the danger actor abusing its platforms to distribute malicious sites hosting the malware.
The group is also recognised to use Android malware this kind of as ActionSpy and PluginPhantom to harvest useful details from compromised units less than the guise of dictionary, keyboard, and prayer applications built out there on third-party application retailers.
The hottest findings from Volexity attribute to EvilBamboo three new Android espionage equipment, specifically BADBAZAAR, BADSIGNAL, and BADSOLAR, the very first of which was documented by Lookout in November 2022.
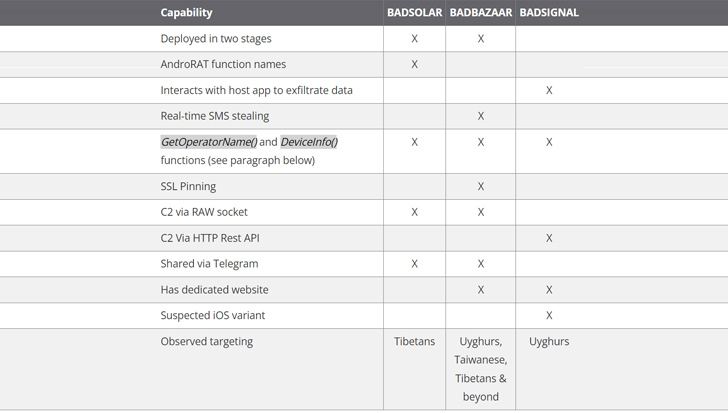
A subsequent report from ESET last thirty day period in-depth two trojanized applications masquerading as Sign and Telegram on the Google Play Shop to entice end users into installing BADSIGNAL. Whilst the Slovak cybersecurity company assigned the bogus to the BADBAZAAR household, citing code similarities, Volexity mentioned, “they also surface to be divergent in their progress and operation.”
Attack chains utilised to distribute the malware families entail the use of APK sharing community forums, phony web-sites advertising and marketing Sign, Telegram, and WhatsApp, Telegram channels devoted to sharing Android apps, and a established of bogus profiles on Fb, Instagram, Reddit, X (previously Twitter), and YouTube.
“The Telegram variants employ the similar API endpoints as the Signal variants to obtain data from the unit and they implement a proxy,” the researchers explained, including it discovered endpoints indicating the existence of an iOS model of BADSIGNAL.
A single of the Telegram channels is also reported to have contained a link to an iOS application named TibetOne that’s no for a longer period out there in the Apple Application Retail outlet.
Future WEBINARAI vs. AI: Harnessing AI Defenses Towards AI-Run Dangers
All set to deal with new AI-pushed cybersecurity issues? Join our insightful webinar with Zscaler to tackle the escalating menace of generative AI in cybersecurity.
Supercharge Your Competencies
Messages shared by using the Telegram teams have also been used to distribute apps backdoored with the BADSOLAR malware as well as booby-trapped links that, when frequented, operate destructive JavaScript to profile and fingerprint the method.
Even though BADBAZAAR is generally utilised to focus on Uyghur and other people today of the Muslim faith, BADSOLAR appears to be utilized primarily with apps that are Tibetan-themed. Even so, both strains incorporate their destructive abilities in the kind of a 2nd phase that’s retrieved from a remote server.
BADSOLAR’s 2nd-stage malware is also a fork of an open up-source Android remote access trojan termed AndroRAT. BADSIGNAL, in distinction, packs all of its information and facts-accumulating functions in the most important offer by itself.
“These strategies mainly depend on customers putting in backdoored applications, which highlights both of those the value of only setting up applications from trustworthy authors and the deficiency of efficient security mechanisms to stop backdoored applications generating their way on to formal application suppliers,” the scientists explained.
“EvilBamboo’s generation of phony internet sites, and the personas tailored to the distinct teams they target, has been a vital part of their operations, enabling them to establish reliable communities that deliver further avenues to focus on people with their spyware or for other exploitation.”
Found this article interesting? Adhere to us on Twitter and LinkedIn to go through much more exceptional content we put up.
Some sections of this short article are sourced from:
thehackernews.com


 New Report Uncovers Three Distinct Clusters of China-Nexus Attacks on Southeast Asian Government
New Report Uncovers Three Distinct Clusters of China-Nexus Attacks on Southeast Asian Government