An unnamed Southeast Asian governing administration has been qualified by numerous China-nexus menace actors as component of espionage campaigns targeting the location more than prolonged periods of time.
“Whilst this action happened all-around the very same time and in some instances even simultaneously on the exact same victims’ devices, just about every cluster is characterized by distinctive resources, modus operandi and infrastructure,” Palo Alto Networks Device 42 researchers Lior Rochberger, Tom Fakterman, and Robert Falcone explained in an exhaustive three-portion report.
The attacks, which qualified distinct governmental entities these as critical infrastructure, community healthcare institutions, community money directors and ministries, have been attributed with moderate self esteem to a few disparate clusters tracked as Stately Taurus (aka Mustang Panda), Alloy Taurus (aka Granite Storm), and Gelsemium.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Mustang Panda utilizes TONESHELL variant and ShadowPad
“The attackers done a cyberespionage procedure that centered on collecting intelligence as nicely as thieving sensitive files and details, whilst protecting a persistent and clandestine foothold,” the scientists claimed, describing it as “highly-targeted and intelligence-driven.”
The activity spanned from the 2nd quarter of 2021 to the 3rd quarter of 2023, leveraging an assortment of equipment to carry out reconnaissance, steal credentials, retain obtain, and conduct post-compromise steps.

Some of the notable software program used to arrive at these goals comprise the LadonGo open-source scanning framework, AdFind, Mimikatz, Impacket, China Chopper web shells, Cobalt Strike, ShadowPad, and a new model of the TONESHELL backdoor.
The malware eschews the use of shellcode in favor of three DLL-primarily based elements to set up persistence on the endpoint, establish command-and-regulate communications with a remote server, and have out information-collecting operations, like command execution, file program interaction, keylogging, and screen capture.
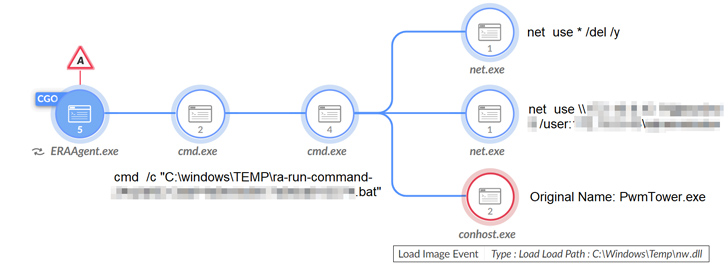
“All through the procedure, the menace actor slowly but surely took command of the victims’ environments, focusing on protecting management for a very long-time period procedure,” the scientists mentioned. “The reason of the risk actor’s attempts appears to be the ongoing collecting and exfiltration of delicate paperwork and intelligence.”
Alloy Taurus Aims to Fly Beneath the Radar
The intrusion established linked to Alloy Taurus is said to have commenced in early 2022 and continued during 2023, leveraging unheard of methods and bypassing security goods for extensive-phrase persistence and reconnaissance.
These attacks, developing in 6 different waves, weaponize security flaws in Microsoft Trade Servers to deploy web shells, which then serves as a conduit to produce additional payloads, counting two formerly mysterious .NET backdoors Zapoa and ReShell to execute arbitrary commands remotely and harvest delicate facts.
Zapoa also incorporates features to extract system data, run shellcode, enumerate operating procedures, load a lot more .NET assembly files to increase its capabilities, and timestamp data files and artifacts with a equipped date, a method known as timestomping.
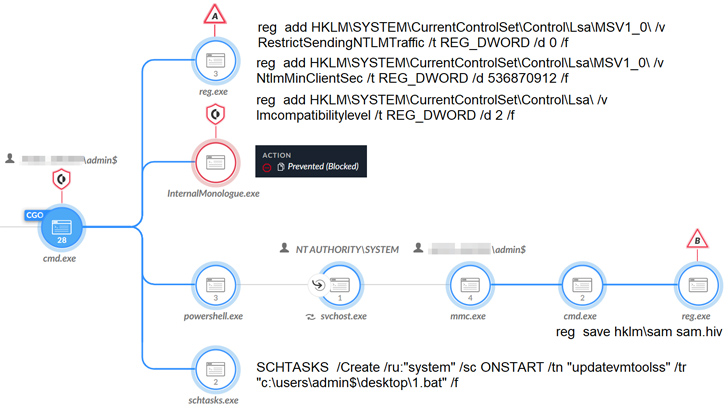
“The threat actor guiding this cluster utilized a experienced tactic, employing multiwave intrusions and exploiting vulnerabilities in Exchange Servers as their most important penetration vector,” the researchers stated.
In some cases, Alloy Taurus has also been noticed carrying out credential theft to facilitate lateral motion by abusing the distant administration tool AnyDesk presently present in the infiltrated environment.
Approaching WEBINARAI vs. AI: Harnessing AI Defenses From AI-Powered Threats
Prepared to tackle new AI-pushed cybersecurity issues? Be part of our insightful webinar with Zscaler to handle the growing threat of generative AI in cybersecurity.
Supercharge Your Abilities
Some of the other application set up by the threat actor contain Cobalt Strike, Quasar RAT, HDoor (a backdoor formerly utilized by Chinese teams like Naikon and Goblin Panda), a Gh0st RAT variant recognized as Gh0stCringe, and Winnti, a multi-useful implant able of granting distant regulate to an infected machine.
Gelsemium Singles Out Susceptible IIS Servers
“This unique cluster had exercise spanning in excess of six months among 2022-2023,” the researchers noted.
“It highlighted a combination of exceptional instruments and techniques that the menace actor leveraged to attain a clandestine foothold and accumulate intelligence from delicate IIS servers belonging to a government entity in Southeast Asia.”
The attack chains capitalize on susceptible web servers to set up web shells and distribute backdoors like OwlProxy and SessionManager, though at the same time using other resources these kinds of as Cobalt Strike, Meterpreter, Earthworm, and SpoolFool for submit-exploitation, tunneling command-and-management targeted traffic, and privilege escalation.
OwlProxy is an HTTP proxy with backdoor functionality that to start with arrived to mild in April 2020. SessionManager, thorough by Kaspersky last July, is a custom made backdoor intended to parse the Cookie discipline inside of inbound HTTP requests to extract the commands issued by the attacker.
“The danger actor obtained access by the use of various web shells, adhering to the attempted set up of various kinds of proxy malware and an IIS backdoor,” the scientists explained. “As some of the menace actor’s attempts to install malware have been unsuccessful, they kept providing new resources, showing their ability to adapt to the mitigation procedure.”
Found this report interesting? Follow us on Twitter and LinkedIn to study a lot more exceptional content material we submit.
Some parts of this post are sourced from:
thehackernews.com

 Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics
Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics