Cybersecurity scientists have uncovered a earlier undocumented superior backdoor dubbed Deadglyph employed by a danger actor acknowledged as Stealth Falcon as section of a cyber espionage campaign.
“Deadglyph’s architecture is strange as it is made up of cooperating components – one a native x64 binary, the other a .NET assembly,” ESET reported in a new report shared with The Hacker Information.
“This mix is abnormal due to the fact malware typically works by using only one programming language for its components. This distinction may possibly show separate advancement of those people two components though also taking benefit of exceptional features of the distinctive programming languages they make the most of.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It’s also suspected that the use of distinct programming languages is a deliberate tactic to hinder evaluation, making it a whole lot far more challenging to navigate and debug.
Compared with other standard backdoors of its type, the instructions are acquired from an actor-managed server in the type of further modules that allow it to produce new procedures, read documents, and collect information and facts from the compromised units.
Stealth Falcon (aka FruityArmor) was very first exposed by the Citizen Lab in 2016, linking it to a set of specific adware attacks in the Middle East aimed at journalists, activists, and dissidents in the U.A.E. making use of spear-phishing lures embedding booby-trapped backlinks pointing to macro-laced documents to produce a tailor made implant able of executing arbitrary instructions.

A subsequent investigation undertaken by Reuters in 2019 disclosed a clandestine procedure referred to as Project Raven that concerned a team of former U.S. intelligence operatives who ended up recruited by a cybersecurity organization named DarkMatter to spy on targets critical of the Arab monarchy.
Stealth Falcon and Venture Raven are considered to be the similar team dependent on the overlaps in tactics and concentrating on.
The group has due to the fact been joined to the zero-working day exploitation of Windows flaws such as CVE-2018-8611 and CVE-2019-0797, with Mandiant noting in April 2020 that the espionage actor “utilised extra zero-days than any other team” from 2016 to 2019.
In 2019, ESET comprehensive the adversary’s use of a backdoor named Win32/StealthFalcon that was observed to use the Windows History Smart Transfer Services (BITS) for command-and-manage (C2) communications and to get finish management of an endpoint.
Deadglyph is the most current addition to Stealth Falcon’s arsenal, according to the Slovak cybersecurity organization, which analyzed an intrusion at an unnamed governmental entity in the Middle East.
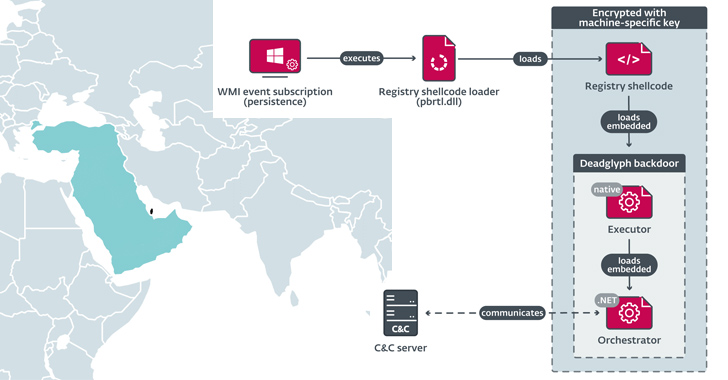
The correct process applied to deliver the implant is now mysterious, but the original part that activates its execution is a shellcode loader that extracts and loads shellcode from the Windows Registry, which subsequently launches Deadglyph’s native x64 module, referred to as the Executor.
The Executor then proceeds with loading a .NET part recognised as the Orchestrator that, in convert, communicates with the command-and-regulate (C2) server to await further more instructions. The malware also engages in a sequence of evasive maneuvers to fly below the radar, counting the ability to uninstall alone.
The commands acquired from the server are queued for execution and can slide into a person of a few groups: Orchestrator duties, Executor responsibilities, and Add jobs.
“Executor duties offer you the capacity to deal with the backdoor and execute supplemental modules,” ESET stated. “Orchestrator duties provide the capacity to control the configuration of the Network and Timer modules, and also to terminate pending tasks.”
Forthcoming WEBINARAI vs. AI: Harnessing AI Defenses Towards AI-Powered Pitfalls
All set to tackle new AI-driven cybersecurity issues? Sign up for our insightful webinar with Zscaler to handle the developing danger of generative AI in cybersecurity.
Supercharge Your Techniques
Some of the identified Executor jobs comprise process generation, file accessibility, and method metadata selection. The Timer module is made use of to poll the C2 server periodically in mixture with the Network module, which implements the C2 communications making use of HTTPS Write-up requests.
Add duties, as the name indicates, enable the backdoor to upload the output of commands and faults.
ESET explained it also discovered a control panel (CPL) file that was uploaded to VirusTotal from Qatar, which is stated to have functioned as a commencing issue for a multi-stage chain that paves the way for a shellcode downloader that shares some code resemblances with Deadglyph.
Even though the nature of the shellcode retrieved from the C2 server stays unclear, it has been theorized that the written content could likely provide as the installer for the Deadglyph malware.
Deadglyph will get its name from artifacts discovered in the backdoor (hexadecimal IDs 0xDEADB001 and 0xDEADB101 for the Timer module and its configuration), coupled with the existence of a homoglyph attack impersonating Microsoft (“Ϻicrоsоft Corpоratiоn”) in the Registry shellcode loader’s VERSIONINFO resource.
“Deadglyph offers a assortment of counter-detection mechanisms, including steady checking of process procedures and the implementation of randomized network patterns,” the business stated. “Furthermore, the backdoor is capable of uninstalling alone to minimize the probability of its detection in specified conditions.”
Found this post interesting? Comply with us on Twitter and LinkedIn to read additional distinctive material we article.
Some parts of this short article are sourced from:
thehackernews.com

 Apple and Chrome Zero-Days Exploited to Hack Egyptian ex-MP with Predator Spyware
Apple and Chrome Zero-Days Exploited to Hack Egyptian ex-MP with Predator Spyware