The a few zero-day flaws resolved by Apple on September 21, 2023, were being leveraged as component of an iPhone exploit chain in an try to deliver a adware strain identified as Predator focusing on previous Egyptian member of parliament Ahmed Eltantawy amongst May perhaps and September 2023.
“The concentrating on took location following Eltantawy publicly stated his plans to operate for President in the 2024 Egyptian elections,” the Citizen Lab mentioned, attributing the attack with superior self-confidence to the Egyptian government owing to it getting a regarded customer of the business spying instrument.
According to a joint investigation executed by the Canadian interdisciplinary laboratory and Google’s Danger Examination Team (TAG), the mercenary surveillance resource is reported to have been sent through hyperlinks sent on SMS and WhatsApp.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
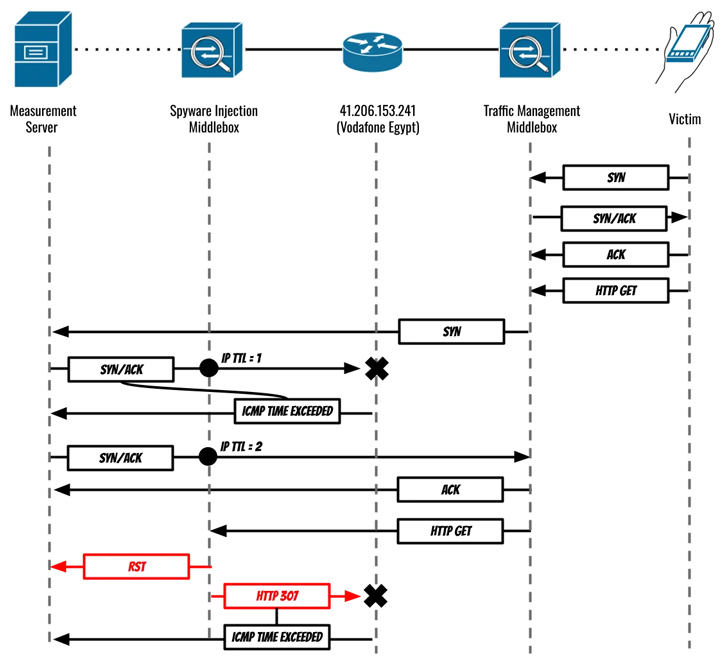
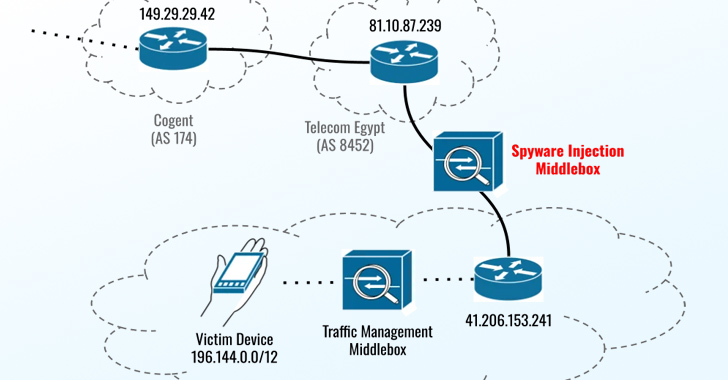
“In August and September 2023, Eltantawy’s Vodafone Egypt cell relationship was persistently picked for targeting by way of network injection when Eltantawy visited selected websites not applying HTTPS, a unit put in at the border of Vodafone Egypt’s network mechanically redirected him to a malicious site to infect his phone with Cytrox’s Predator spy ware,” the Citizen Lab researchers explained.

The exploit chain leveraged a set of three vulnerabilities – CVE-2023-41991, CVE-2023-41992, and CVE-2023-41993 – which could permit a destructive actor to bypass certificate validation, elevate privileges, and accomplish distant code execution on qualified units on processing a specially crafted web content.
Predator, designed by a business termed Cytrox, is analogous to NSO Group’s Pegasus, enabling its consumers to surveil targets of desire and harvest delicate knowledge from compromised devices. Element of a consortium of spy ware suppliers called the Intellexa Alliance, it was blocklisted by the U.S. govt in July 2023 for “enabling strategies of repression and other human legal rights abuses.”
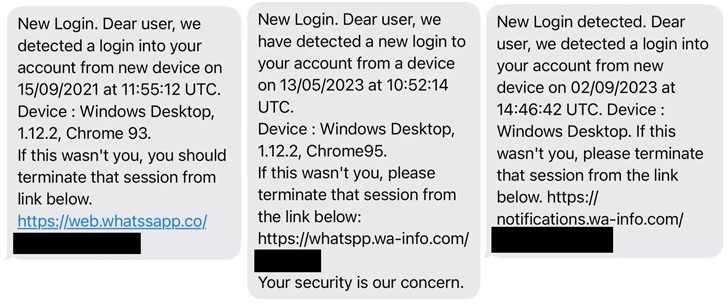
The exploit, hosted on a area named sec-flare[.]com, is explained to have been sent just after Eltantawy was redirected to a internet site named c.betly[.]me by suggests of a subtle network injection attack utilizing Sandvine’s PacketLogic middlebox located on a connection in between Telecom Egypt and Vodafone Egypt.
“The physique of the spot web page bundled two iframes, ID ‘if1’ which contained evidently benign bait written content (in this case a website link to an APK file not containing spyware) and ID ‘if2’ which was an invisible iframe made up of a Predator infection website link hosted on sec-flare[.]com,” the Citizen Lab stated.
Google TAG researcher Maddie Stone characterised it as a situation of an adversary-in-the-center (AitM) attack that usually takes advantage of a pay a visit to to a web page using HTTP (as opposed to HTTPS) to intercept and force the target to pay a visit to a different internet site operated by the menace actor.
“In the scenario of this campaign, if the target went to any ‘http’ web site, the attackers injected visitors to silently redirect them to an Intellexa site, c.betly[.]me,” Stone defined. “If the consumer was the predicted focused user, the web site would then redirect the goal to the exploit server, sec-flare[.]com.”
Eltantawy gained three SMS messages in September 2021, May 2023, and September 2023 that masqueraded as security alerts from WhatsApp urging Eltantawy to simply click on a website link to terminate a suspicious login session originating from a purported Windows system.
While these one-way links never match the fingerprint of the aforementioned area, the investigation exposed that the Predator spyware was set up on the unit close to 2 minutes and 30 seconds soon after Eltantawy browse the concept despatched in September 2021.
Impending WEBINARAI vs. AI: Harnessing AI Defenses In opposition to AI-Driven Dangers
Ready to tackle new AI-driven cybersecurity worries? Sign up for our insightful webinar with Zscaler to handle the expanding threat of generative AI in cybersecurity.
Supercharge Your Skills
He also obtained two WhatsApp messages on June 24, 2023, and July 12, 2023, in which an unique proclaiming to be performing for the Worldwide Federation for Human Legal rights (FIDH) solicited his viewpoint on an short article that pointed to the web page sec-flare[.]com. The messages ended up remaining unread.
Google TAG stated it also detected an exploit chain that weaponized a remote code execution flaw in the Chrome web browser (CVE-2023-4762) to supply Predator on Android devices employing two techniques: the AitM injection and through one-time inbound links sent right to the concentrate on.
CVE-2023-4762, a variety confusion vulnerability in the V8 engine, was anonymously reported on August 16, 2023, and patched by Google on September 5, 2023, despite the fact that the internet huge assesses that Cytrox/Intellexa may well have utilized this vulnerability as a zero-working day.
In accordance to a quick description on the Nationwide Vulnerability Database (NVD), CVE-2023-4762 considerations a “style confusion in V8 in Google Chrome prior to 116..5845.179 [that] permitted a remote attacker to execute arbitrary code by means of a crafted HTML web page.”
The hottest results, other than highlighting the abuse of surveillance equipment to target the civil society, underscores the blindspots in the telecom ecosystem that could be exploited to intercept network targeted traffic and inject malware into targets’ units.
“Though great strides have been designed in modern many years to ‘encrypt the web,’ buyers however once in a while check out sites with no HTTPS, and a solitary non-HTTPS internet site stop by can outcome in spyware infection,” the Citizen Lab mentioned.
People who are at risk of adware threats due to the fact of “who they are or what they do” are advisable to retain their gadgets up-to-day and permit Lockdown Mode on iPhones, iPads, and Macs to stave off this sort of pitfalls.
Discovered this write-up intriguing? Follow us on Twitter and LinkedIn to read extra exclusive material we publish.
Some elements of this article are sourced from:
thehackernews.com

 New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks
New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks