An lively malware marketing campaign concentrating on Latin The us is dispensing a new variant of a banking trojan called BBTok, particularly people in Brazil and Mexico.
“The BBTok banker has a dedicated features that replicates the interfaces of extra than 40 Mexican and Brazilian banks, and tips the victims into moving into its 2FA code to their lender accounts or into entering their payment card amount,” Examine Position claimed in study printed this week.
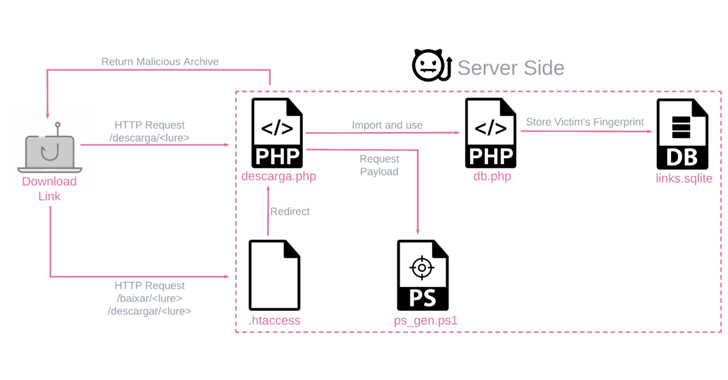
The payloads are produced by a customized server-facet PowerShell script and are exceptional for every single target primarily based on the running system and nation, though staying shipped by way of phishing e-mail that leverage a assortment of file varieties.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
BBTok is a Windows-dependent banking malware that to start with surfaced in 2020. It’s outfitted with options that operate the usual trojan gamut, making it possible for it to enumerate and kill procedures, issue remote commands, manipulate keyboard, and serve pretend login internet pages for banking companies functioning in the two international locations.
The attack chains on their own are quite uncomplicated, utilizing bogus backlinks or ZIP file attachments to stealthily deploy the banker retrieved from a remote server (216.250.251[.]196) when displaying a decoy document to the victim.

But they are also diversified for each Windows 7 and Windows 10 programs, largely taking steps to evade recently executed detection mechanisms these as Antimalware Scan Interface (AMSI) that will allow for scanning the equipment for any threats.
Two other key strategies to fly less than the radar are the use of dwelling-off-the-land binaries (LOLBins) and geofencing checks to guarantee that the targets are only from Brazil or Mexico just before serving the malware by way of the PowerShell script.
As soon as released, BBTok establishes connections with a distant server to acquire commands to simulate the security verification internet pages for various banking companies.
In impersonating the interfaces of Latin American banks, the goal is to harvest credential and authentication information entered by the end users to carry out account takeovers of the on the web financial institution accounts.
“What is notable is the operator’s careful tactic: all banking actions are only executed upon direct command from its C2 server, and are not instantly carried out on each individual contaminated technique,” the business explained.
Examine Point’s evaluation of the malware has disclosed a significant enhancement to its obfuscation and focusing on given that 2020, expanding over and above Mexican banking companies. The existence of Spanish and Portuguese language in the supply code as nicely as in phishing emails presents a hint as to the attackers’ origin.
Far more than 150 users are estimated to have been infected by BBTok, based mostly on an SQLite database discovered in the server hosting the payload era element that documents entry to the malicious software.
The focusing on and the language details to the danger actors probably working out of Brazil, which carries on to be the epicenter of potent fiscally-focused malware.
Impending WEBINARAI vs. AI: Harnessing AI Defenses From AI-Powered Risks
Completely ready to deal with new AI-driven cybersecurity troubles? Sign up for our insightful webinar with Zscaler to handle the increasing menace of generative AI in cybersecurity.
Supercharge Your Skills
“Even though BBTok has been able to stay less than the radar thanks to its elusive techniques and concentrating on victims only in Mexico and Brazil, it’s obvious that it is even now actively deployed,” Look at Place explained.
“Because of to its numerous abilities, and its exceptional and artistic supply system involving LNK documents, SMB and MSBuild, it still poses a threat to corporations and individuals in the region.”
The development arrives as the Israeli cybersecurity company comprehensive a new huge-scale phishing marketing campaign that a short while ago targeted above 40 popular firms across various industries in Colombia with an supreme aim to deploy the Remcos RAT through a multi-phase an infection sequence.
“Remcos, a refined ‘Swiss Army Knife’ RAT, grants attackers comprehensive regulate about the contaminated laptop or computer and can be utilized in a wide variety of attacks. Frequent implications of a Remcos an infection contain facts theft, stick to-up infections, and account takeover,” Verify Stage said.
Located this article fascinating? Abide by us on Twitter and LinkedIn to go through extra exclusive written content we publish.
Some elements of this write-up are sourced from:
thehackernews.com

 How to Interpret the 2023 MITRE ATT&CK Evaluation Results
How to Interpret the 2023 MITRE ATT&CK Evaluation Results