At the starting of January, Gcore confronted an incident involving several L3/L4 DDoS attacks with a peak quantity of 650 Gbps. Attackers exploited over 2000 servers belonging to one of the top rated 3 cloud vendors worldwide and targeted a customer who was applying a cost-free CDN plan. Even so, owing to Gcore’s distribution of infrastructure and a large number of peering associates, the attacks had been mitigated, and the client’s web application remained out there.
Why was mitigating these attacks so significant?
1. These attacks were major since they exceeded the ordinary bandwidth of equivalent attacks by 60×. The done attacks relate to volume-based attacks targeted to saturate the attacked application’s bandwidth in order to overflow it. Measuring full quantity (bps)—rather than the quantity of requests—is the way these attacks are ordinarily tabulated.
The regular bandwidth of this attack form is normally in the tens of Gbps (about 10 Gbps). Therefore, the specified attacks (at 650 Gbps) exceeded the common price by 60 times. Attacks of this quantity are rare and are of distinct curiosity to security professionals.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Additionally, this price (650 Gbps) is similar to the history DDoS attack on the most significant Minecraft server (2.4 Tbps), only one-fourth as substantial.
2. The consumer getting attacked was applying a CDN plan devoid of more DDoS security. When clientele use Gcore’s CDN (as portion of the Edge Network), the malicious visitors of the L3/L4 attacks right impacts only its infrastructure (it serves as a filter), not the qualified clients’ servers. The unfavorable impact falls on the capability and connectivity of the infrastructure When a CDN is impressive more than enough, it can guard shoppers against L3/L4 attacks—even when accessed applying a free plan.
What were the technical specifications of the attacks?
The length of the incident was 15 minutes, and at its peak, it achieved more than 650 Gbps. A doable explanation why the incident took so extended is that the attackers weighed the ineffectiveness of the attacks (the customer application retained operating) against their superior value.
The incident consisted of 3 attacks with unique vectors. They are marked with site visitors peaks on the diagram below:
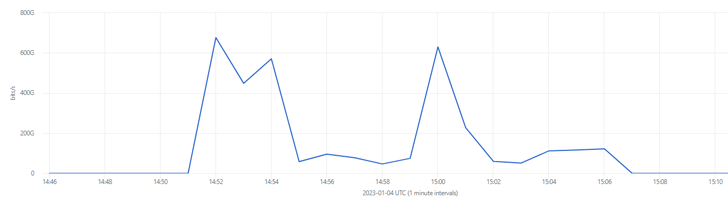
The distinctiveness of the incident was that the attacks have been performed from numerous non-spoofed IP addresses. This permitted professionals to discover that the attackers employed 2,143 servers in 44 various locations, and all of the servers belonged to a solitary community cloud provider. Employing Anycast authorized Gcore to absorb the attack 100% about peering connections with this provider.
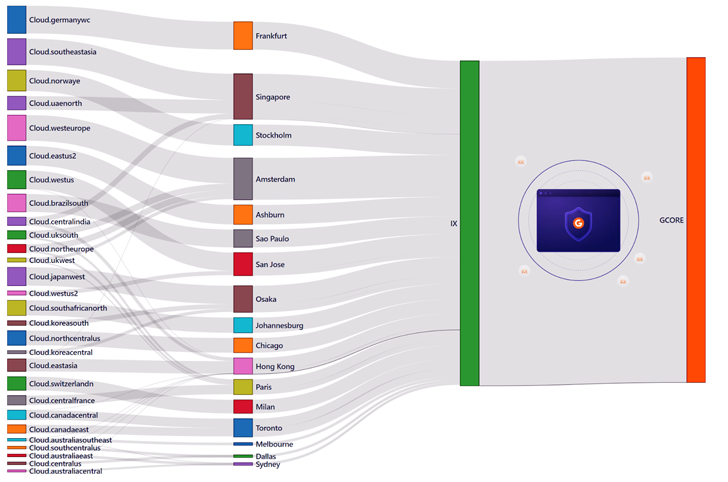
Sankey diagram displaying the resource and movement of the attack. Names of the destinations from the first column are linked with one particular of the best 3 cloud companies.
Why did the attacks not have an effect on the shopper?
1. Gcore’s connectivity by peering with a lot of areas performed a key purpose in mitigating the attacks. Gcore has over 11,000 peering companions (ISPs), and these associates link their networks working with cables and give every single other with accessibility to visitors originating from their networks. These connections make it possible for for bypassing the community internet and specifically absorbing targeted visitors from the peering companions. In addition, this website traffic is either no cost of cost or charges much significantly less than site visitors on the public internet. This low expense would make it probable to protect shopper site visitors on a free plan.
In the context of the DDoS attack that transpired, the level of connectivity considerably benefited the efficacy of mitigation. Gcore and the cloud provider made use of to launch the attack are peering associates, so when the attack was taking place, Gcore was able to ingest most of the targeted traffic above the cloud provider’s personal network. This enormously diminished the total of targeted visitors that essential to be dealt with by the general public internet.
Personal peering also permits extra precise filtering and greater attack visibility, which qualified prospects to extra productive attack mitigation.
2. Gcore’s substantial potential, thanks to the placement of servers in a lot of info centers, also played a function. Gcore’s edge servers are existing in more than 140 factors of presence and are primarily based on high-overall performance 3rd technology Intel® Xeon® Scalable processors.
The overall network ability is over 110 Tbps. With about 500 servers located in info centers worldwide, the organization is equipped to withstand substantial-scale DDoS attacks. So, the 650 Gbps of site visitors could be distributed across the network, and every single particular server would only obtain 1-2 Gbps, which is an insignificant load.
Security traits
According to Gcore’s working experience, DDoS attacks will continue to improve 12 months over 12 months. In 2021, the attacks achieved 300 Gbps, and by 2022, they had greater to 700 Gbps. Thus, even smaller and medium-sized organizations want to use distributed articles delivery networks these kinds of as the CDN and Cloud to guard from DDoS attacks.
Found this posting fascinating? Adhere to us on Twitter and LinkedIn to study additional exceptional content material we submit.
Some areas of this write-up are sourced from:
thehackernews.com


 U.S. Cybersecurity Agency CISA Adds Three New Vulnerabilities in KEV Catalog
U.S. Cybersecurity Agency CISA Adds Three New Vulnerabilities in KEV Catalog