An open source command-and-regulate (C2) framework known as Havoc is becoming adopted by threat actors as an option to other properly-recognized reputable toolkits like Cobalt Strike, Sliver, and Brute Ratel.
Cybersecurity company Zscaler said it observed a new campaign in the starting of January 2023 concentrating on an unnamed government group that used Havoc.
“When C2 frameworks are prolific, the open up-supply Havoc framework is an sophisticated put up-exploitation command-and-manage framework capable of bypassing the most latest and up-to-date variation of Windows 11 defender owing to the implementation of superior evasion tactics these kinds of as oblique syscalls and snooze obfuscation,” scientists Niraj Shivtarkar and Niraj Shivtarkar explained.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
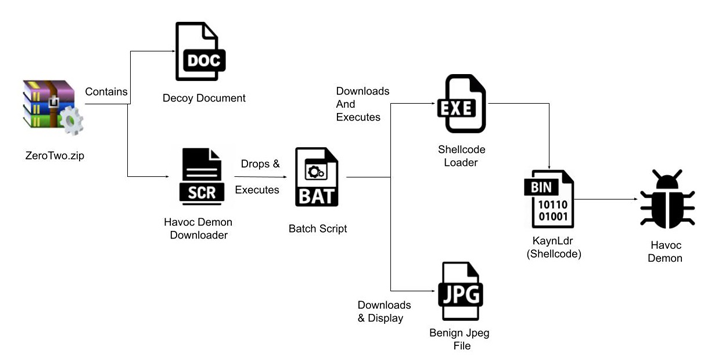
The attack sequence documented by Zscaler commences with a ZIP archive that embeds a decoy doc and a monitor-saver file which is developed to download and launch the Havoc Demon agent on the infected host.
Demon is the implant created through the Havoc Framework and is analogous to the Beacon sent by way of Cobalt Strike to achieve persistent entry and distribute destructive payloads.
It also will come with a vast range of characteristics that helps make it challenging to detect, turning it into a lucrative instrument in the fingers of menace actors even as cybersecurity suppliers are pushing again from the abuse of this sort of reputable crimson workforce computer software.
“Just after the demon is deployed correctly on the target’s device, the server is ready to execute several instructions on the goal procedure,” the researchers explained, stating that the server logs the command and its reaction on execution. The results are subsequently encrypted and transmitted back to the C2 server.
Havoc has also been employed in link with a fraudulent npm module dubbed aabquerys that, at the time put in, triggers a three-stage course of action to retrieve the Demon implant. The bundle has due to the fact been taken down.
Identified this article exciting? Abide by us on Twitter and LinkedIn to read a lot more distinctive written content we put up.
Some pieces of this report are sourced from:
thehackernews.com


 Gcore Thwarts Massive 650 Gbps DDoS Attack on Free Plan Client
Gcore Thwarts Massive 650 Gbps DDoS Attack on Free Plan Client