Losing sleep more than Generative-AI apps? You might be not alone or erroneous. According to the Astrix Security Study Group, mid measurement corporations already have, on normal, 54 Generative-AI integrations to core programs like Slack, GitHub and Google Workspace and this number is only predicted to expand. Proceed looking through to fully grasp the prospective dangers and how to lower them.
E book a Generative-AI Discovery session with Astrix Security’s industry experts (totally free – no strings hooked up – agentless & zero friction)
“Hey ChatGPT, overview and enhance our resource code”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Hey Jasper.ai, create a summary email of all our net new clients from this quarter”
“Hey Otter.ai, summarize our Zoom board meeting”
In this era of money turmoil, firms and workers alike are consistently wanting for applications to automate operate processes and raise effectiveness and productiveness by connecting third party applications to core company devices these as Google workspace, Slack and GitHub through API keys, OAuth tokens, services accounts and extra. The rise of Generative-AI applications and GPT expert services exacerbates this issue, with workforce of all departments fast introducing the most current and biggest AI applications to their productivity arsenal, with out the security team’s know-how.
From engineering applications these as code evaluate and optimization to internet marketing, design and style and profits applications this kind of as information & video generation, impression generation and email automation applications. With ChatGPT becoming the speediest developing app in history, and AI-powered apps currently being downloaded 1506% extra than very last year, the security challenges of applying, and even worse, connecting these typically unvetted applications to business main devices is currently causing sleepless nights for security leaders.
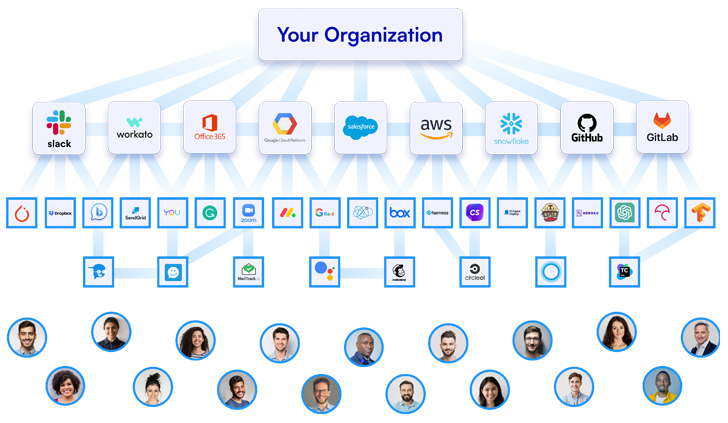 Your organization’s application-to-application connectivity
Your organization’s application-to-application connectivity
The dangers of Gen-AI apps
AI-centered applications current two principal considerations for security leaders:
1. Knowledge Sharing by using applications like ChatGPT: The electrical power of AI lies in knowledge, but this incredibly toughness can be a weak spot if mismanaged. Workforce might unintentionally share sensitive, organization-critical info such as prospects PII and mental residence like code. This sort of leaks can expose organizations to knowledge breaches, competitive cons and compliance violations. And this is not a fable – just inquire Samsung.
The Samsung and ChatGPT leaks – a scenario for caution
Samsung claimed a few distinctive leaks of hugely sensitive information by 3 workers that made use of ChatGPT for efficiency purposes. One of the employees shared a confidential resource code to check it for errors, a further shared code for code optimization, and the 3rd shared a recording of a meeting to change into meeting notes for a presentation. All this information is now made use of by ChatGPT to educate the AI styles and can be shared throughout the web.
2. Unverified Generative-AI apps: Not all generative AI applications arrive from verified resources. Astrix’s the latest analysis reveals that workers are significantly connecting these AI-dependent applications (that usually have high-privilege access) to main systems like GitHub, Salesforce and these – increasing significant security fears.
 The broad array of Generative AI applications
The broad array of Generative AI applications
Reserve a Generative-AI Discovery session with Astrix Security’s experts (free – no strings hooked up – agentless & zero friction)
True existence instance of a risky Gen-AI integration:
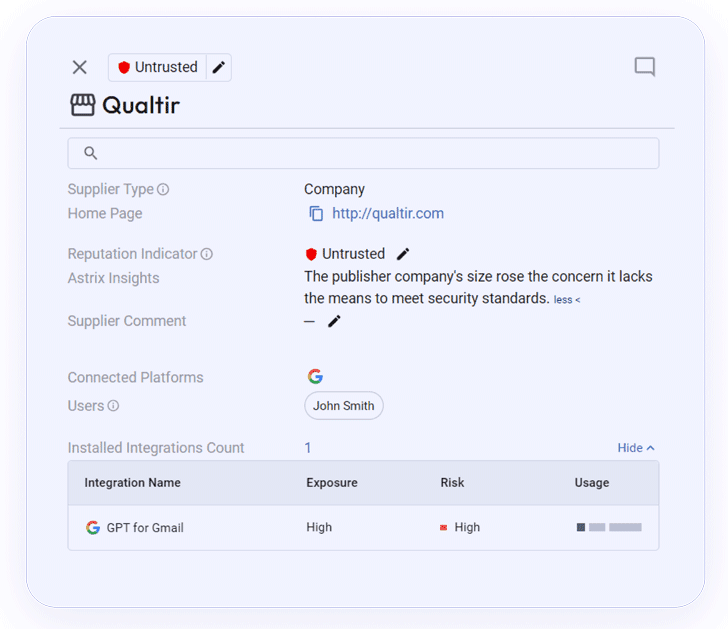
In the images down below you can see the particulars from the Astrix system about a dangerous Gen-AI integration that connects to the organization’s Google Workspace natural environment.
This integration, Google Workspace Integration “GPT For Gmail”, was designed by an untrusted developer and granted with significant-permissions to the organization’s Gmail accounts:
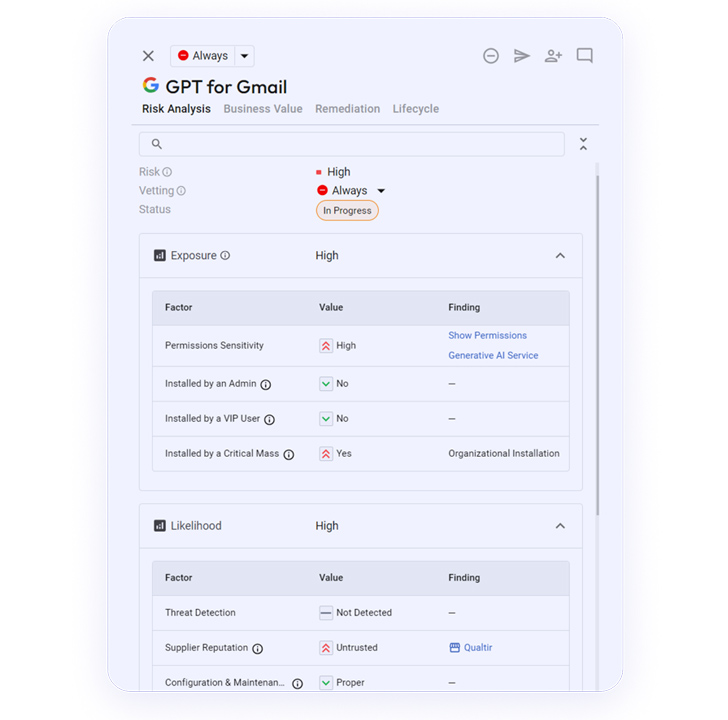
Amid the scopes of the permissions granted to the integration is “mail.all”, which makes it possible for the third party app to browse, compose, ship and delete emails – a incredibly sensitive privilege:
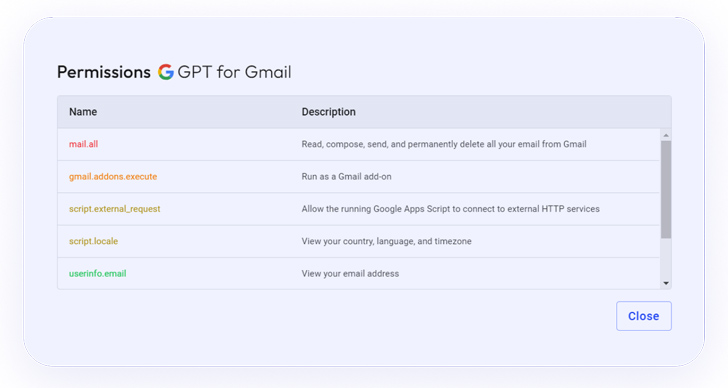
Information and facts about the integration’s provider, which is untrusted:
How Astrix allows minimizing your AI dangers
To safely and securely navigate the fascinating but complex landscape of AI, security teams need to have strong non-human id management in order to get visibility into the third-party products and services your workforce are connecting, as effectively as handle more than permissions and effectively consider likely security challenges. With Astrix you now can:
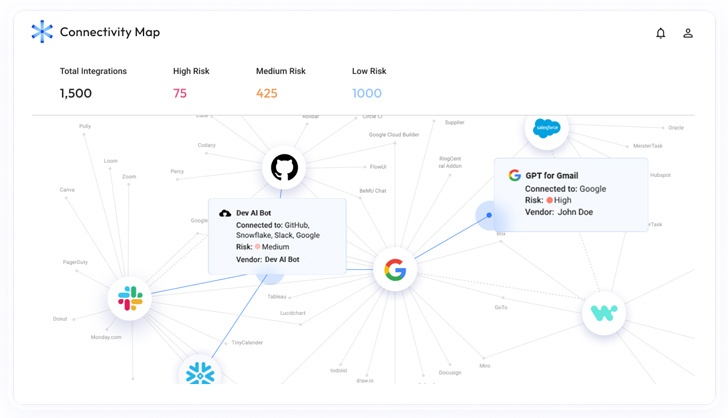 The Astrix Connectivity map
The Astrix Connectivity map
- Get a entire inventory of all AI-tools that your personnel use and access your core techniques, and understand the dangers associated with them.
- Clear away security bottlenecks with automatic security guardrails: fully grasp the organization benefit of each and every non-human link which includes the utilization level (frequency, very last routine maintenance, use quantity), the connection owner, who in the corporation takes advantage of the integration and the marketplace details.
- Lessen your attack area – Make certain all AI-based mostly non-human identities accessing your core units have minimum privileged access, clear away unused connections, and untrusted app sellers.
- Detect anomalous action and remediate risks: Astrix analyzes and detects destructive conduct this kind of as stolen tokens, interior application abuse and untrusted distributors in genuine time as a result of IP, person agent and entry data anomalies.
- Remediate faster: Astrix will take the load off your security group with automated remediation workflows as well as instructing conclude-end users on resolving their security issues independently.
E book a Generative-AI Discovery session with Astrix Security’s experts (no cost – no strings connected – agentless & zero friction)
Observed this post fascinating? Observe us on Twitter and LinkedIn to read through a lot more special written content we article.
Some elements of this report are sourced from:
thehackernews.com


 Alert: Million of GitHub Repositories Likely Vulnerable to RepoJacking Attack
Alert: Million of GitHub Repositories Likely Vulnerable to RepoJacking Attack