A new phishing campaign codenamed MULTI#STORM has established its sights on India and the U.S. by leveraging JavaScript data files to produce distant accessibility trojans on compromised programs.
“The attack chain ends with the victim device contaminated with numerous special RAT (distant entry trojan) malware occasions, these types of as Warzone RAT and Quasar RAT,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov reported.
“Both equally are applied for command-and-control all through unique phases of the infection chain.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The multi-stage attack chain commences when an email receiver clicks the embedded link pointing to a password-safeguarded ZIP file (“Ask for.zip”) hosted on Microsoft OneDrive with the password “12345.”

Extracting the archive file reveals a closely obfuscated JavaScript file (“Request.js”) that, when double clicked, activates the an infection by executing two PowerShell instructions that are responsible for retrieving two individual payloads from OneDrive and executing them.
The very first of the two documents is a decoy PDF document that is shown to the sufferer when the 2nd file, a Python-dependent executable, is stealthily operate in the qualifications.
The binary functions as a dropper to extract and operate the principal payload packed inside it in the variety of Foundation64-encoded strings (“Storm.exe”), but not right before environment up persistence by means of Windows Registry modification.
Also decoded by the binary is a second ZIP file (“data files.zip”) that is made up of 4 unique documents, each of which is made to bypass User Account Handle (UAC) and escalate privileges by generating mock dependable directories.
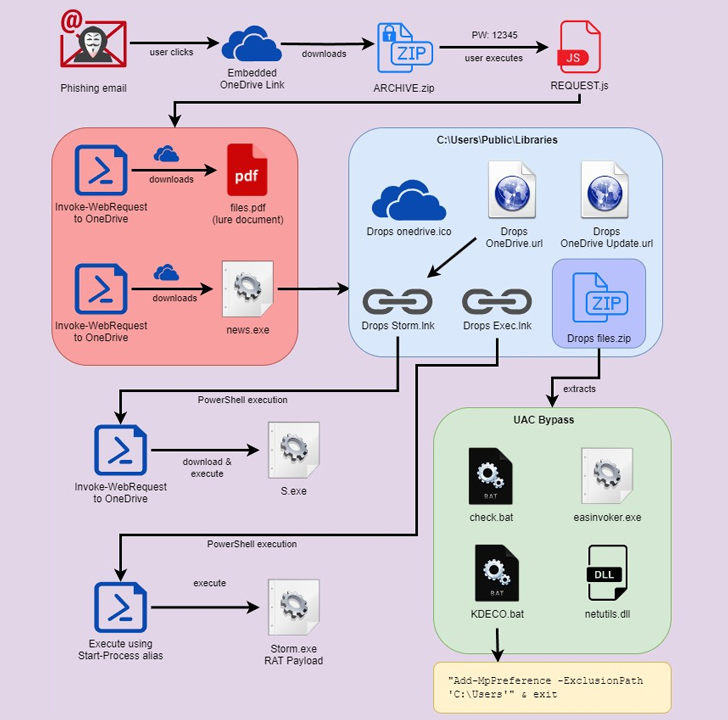
Amid the information is a batch file (“examine.bat”) that Securonix reported shares numerous commonalities with yet another loader identified as DBatLoader in spite of the difference in the programming language used.
A second file named “KDECO.bat” executes a PowerShell command to instruct Microsoft Defender to include an antivirus exclusion rule to skip the “C:Users” listing.
Upcoming WEBINAR🔐 Mastering API Security: Knowing Your Genuine Attack Surface area
Find the untapped vulnerabilities in your API ecosystem and just take proactive actions towards ironclad security. Be part of our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:immediately afterexhibit:inline-block.verify_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-correct-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-size:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.wn-label:immediately afterwidth:50pxheight:6pxcontent:”border-top rated:2px reliable #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-fat:900textual content-align:leftline-height:33px.wn-descriptiontext-align:leftfont-sizing:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
The attack culminates with the deployment of Warzone RAT (aka Ave Maria), an off-the-shelf malware that’s accessible for sale for $38 for every month and will come with an exhaustive record of functions to harvest delicate facts and obtain further malware these as Quasar RAT.
“It truly is essential to stay further vigilant when it comes to phishing emails, in particular when a perception of urgency is pressured,” the researchers claimed.
“This specific lure was usually unremarkable as it would call for the user to execute a JavaScript file directly. Shortcut data files, or data files working with double extensions would most likely have a bigger accomplishment rate.”
Identified this write-up fascinating? Follow us on Twitter and LinkedIn to examine far more special content we put up.
Some areas of this write-up are sourced from:
thehackernews.com

 Generative-AI apps & ChatGPT: Potential risks and mitigation strategies
Generative-AI apps & ChatGPT: Potential risks and mitigation strategies