German and South Korean govt agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users’ Gmail inboxes.
The joint advisory comes from Germany’s domestic intelligence equipment, the Federal Business office for the Safety of the Constitution (BfV), and South Korea’s National Intelligence Service of the Republic of Korea (NIS).
The intrusions are built to strike “gurus on the Korean Peninsula and North Korea issues” by spear-phishing strategies, the organizations noted.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Kimsuky, also recognised Black Banshee, Thallium, and Velvet Chollima, refers to a subordinate aspect within North Korea’s Reconnaissance Basic Bureau and is recognised to “obtain strategic intelligence on geopolitical events and negotiations influencing the DPRK’s interests.”
Principal targets of fascination incorporate entities in the U.S. and South Korea, notably singling out persons performing in just the government, army, manufacturing, academic, and assume tank organizations.
“This danger actor’s pursuits contain amassing financial, own, and customer info specifically from academic, manufacturing, and countrywide security industries in South Korea,” Google-owned menace intelligence organization Mandiant disclosed previous year.
The latest attacks orchestrated by the team suggest an growth of its cyber exercise to encompass Android malware strains this kind of as FastFire, FastSpy, FastViewer, and RambleOn.
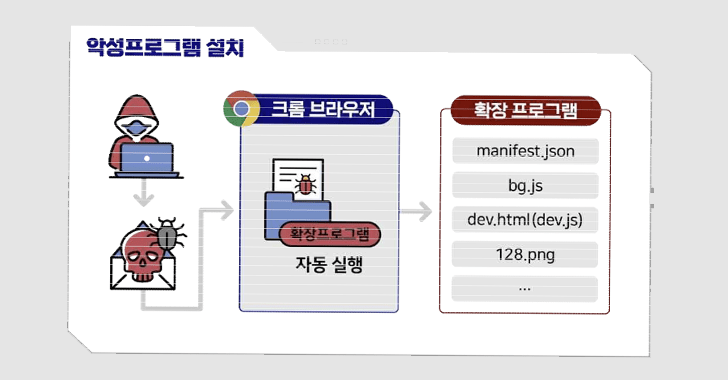
The use of Chromium-primarily based browser extensions for cyber espionage reasons is not new for Kimsuky, which has previously used related procedures as section of campaigns tracked as Stolen Pencil and SharpTongue.
The SharpTongue procedure also overlaps with the most current energy in that the latter is also able of thieving a victim’s email content applying the rogue add-on, which, in switch, leverages the browser’s DevTools API to execute the operate.
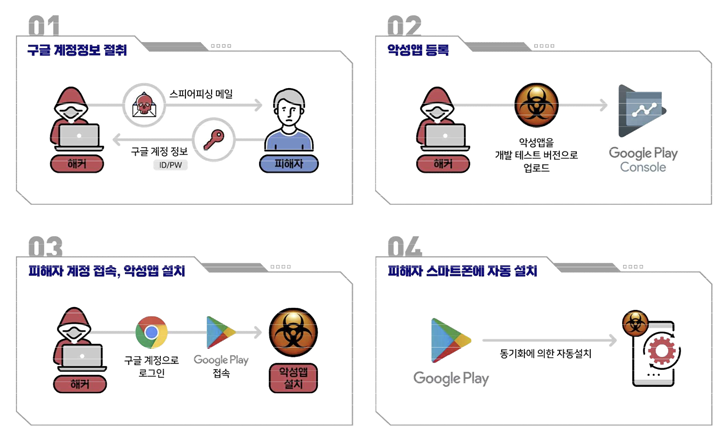
But in an escalation of Kimsuky’s cellular attacks, the menace actor has been noticed logging into victims’ Google accounts working with qualifications presently received in advance by way of phishing strategies and then putting in a destructive application on the products connected to the accounts.
“The attacker logs in with the victim’s Google account on the Computer system, accesses the Google Play Retail outlet, and requests the set up of a malicious application,” the organizations spelled out. “At this time, the target’s smartphone joined with the Google account is picked as the machine to set up the malicious app on.”
It is really suspected that the applications, which embed FastFire and FastViewer, are dispersed working with a Google Perform aspect recognized as “internal tests” that lets 3rd-party developers to distribute their applications to a “small set of reliable testers.”
WEBINARDiscover the Concealed Hazards of Third-Party SaaS Applications
Are you aware of the pitfalls associated with third-party application accessibility to your company’s SaaS apps? Be a part of our webinar to understand about the kinds of permissions becoming granted and how to reduce risk.
RESERVE YOUR SEAT
A issue truly worth mentioning right here is that these inner application checks, which are carried out prior to releasing the app to production, are not able to exceed 100 consumers for every application, indicating that the marketing campaign is really specific in mother nature.
Equally the malware-laced applications occur with abilities to harvest a extensive assortment of sensitive details by abusing Android’s accessibility products and services. The applications are shown under –
- com.viewer.fastsecure (FastFire)
- com.tf.thinkdroid.secviewer (FastViewer)
The disclosure will come as the North Korean advanced persistent danger (APT) actor dubbed ScarCruft has been joined to various attack vectors that are used to provide PowerShell-dependent backdoors on to compromised hosts.
Located this post attention-grabbing? Observe us on Twitter and LinkedIn to study more special written content we put up.
Some areas of this report are sourced from:
thehackernews.com

 BreachForums Shuts Down After Admin’s Arrest
BreachForums Shuts Down After Admin’s Arrest