Telecommunication providers in the Center East are the matter of new cyber attacks that commenced in the initially quarter of 2023.
The intrusion set has been attributed to a Chinese cyber espionage actor related with a extended-jogging campaign dubbed Procedure Smooth Mobile based on tooling overlaps.
“The original attack section consists of infiltrating Internet-going through Microsoft Trade servers to deploy web shells made use of for command execution,” researchers from SentinelOne and QGroup mentioned in a new complex report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“After a foothold is founded, the attackers carry out a variety of reconnaissance, credential theft, lateral movement, and info exfiltration things to do.”
Procedure Gentle Mobile, according to Cybereason, refers to malicious things to do carried out by China-affiliated actors concentrating on telecommunications providers because at minimum 2012.
The Smooth Mobile danger actor, also tracked by Microsoft as Gallium, is known to goal unpatched internet-dealing with expert services and use instruments like Mimikatz to acquire qualifications that allows for lateral movement throughout the focused networks.
Also set to use by the adversarial collective is a “tough-to-detect” backdoor codenamed PingPull in its espionage attacks directed against organizations working in Southeast Asia, Europe, Africa, and the Middle East.
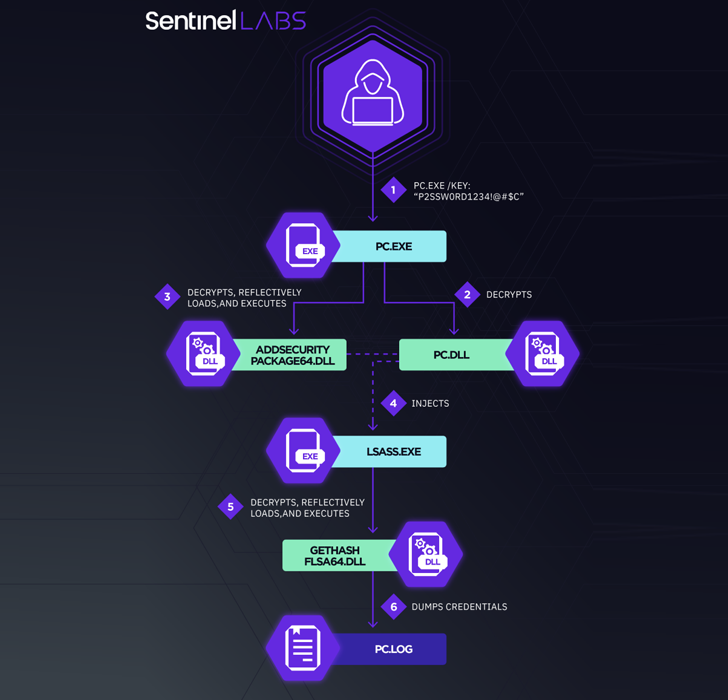
Central to the most up-to-date marketing campaign is the deployment of a customized variant of Mimikatz referred to as mim221, which packs in new anti-detection functions.
“The use of unique-goal modules that carry out a selection of sophisticated strategies demonstrates the threat actors’ devotion to advancing its toolset to maximum stealth,” the scientists reported, introducing it “highlights the constant servicing and even more improvement of the Chinese espionage malware arsenal.”
Prior exploration into Gallium suggests tactical similarities [PDF] with multiple Chinese country-state teams this sort of as APT10 (aka Bronze Riverside, Potassium, or Stone Panda), APT27 (aka Bronze Union, Emissary Panda, or Lucky Mouse), and APT41 (aka Barium, Bronze Atlas, or Wicked Panda).
WEBINARDiscover the Hidden Hazards of 3rd-Party SaaS Apps
Are you aware of the hazards linked with 3rd-party app access to your company’s SaaS apps? Sign up for our webinar to understand about the styles of permissions remaining granted and how to lessen risk.
RESERVE YOUR SEAT
This as soon as all over again points to signals of shut-supply resource-sharing involving Chinese condition-sponsored danger actors, not to mention the possibility of a “digital quartermaster” dependable for retaining and distributing the toolset.
The findings come amid revelations that several other hacking groups, like BackdoorDiplomacy and WIP26, have set their sights on telecom service companies in the Center East location.
“Chinese cyber espionage threat actors are recognised to have a strategic interest in the Middle East,” the scientists concluded.
“These menace actors will practically unquestionably keep on checking out and upgrading their equipment with new techniques for evading detection, which include integrating and modifying publicly available code.”
Observed this post exciting? Abide by us on Twitter and LinkedIn to read more distinctive content material we submit.
Some components of this report are sourced from:
thehackernews.com


 German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics