GitHub has introduced the basic availability of a new security characteristic termed force protection, which aims to avert builders from inadvertently leaking keys and other strategies in their code.
The Microsoft-owned cloud-primarily based repository hosting platform, which commenced testing the element a calendar year back, stated it’s also extending push defense to all public repositories at no further price tag.
The operation is developed to operate hand-in-hand with the present mystery scanning attribute, which scans repositories for recognized key formats to avert their fraudulent use and avert most likely significant outcomes.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“Force security helps prevent secret leaks devoid of compromising the developer expertise by scanning for highly identifiable secrets and techniques right before they are dedicated,” GitHub mentioned earlier this week.
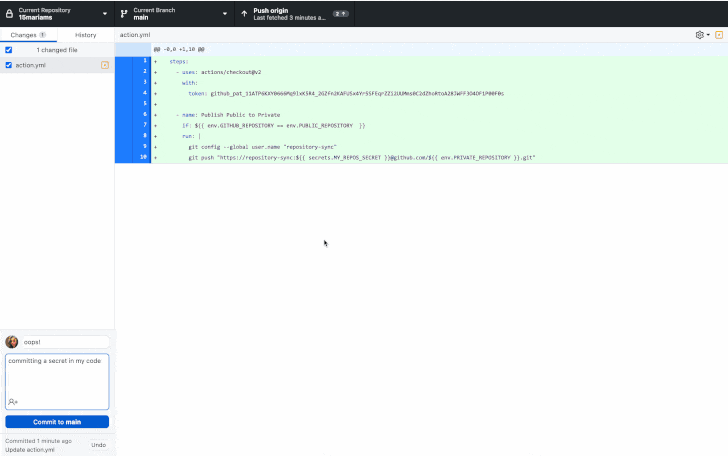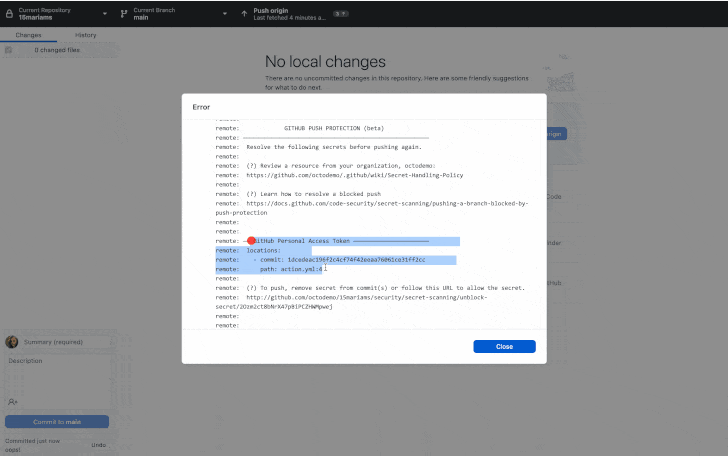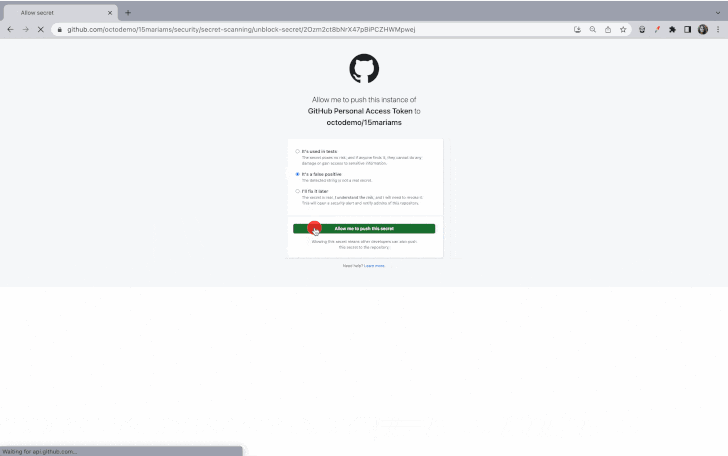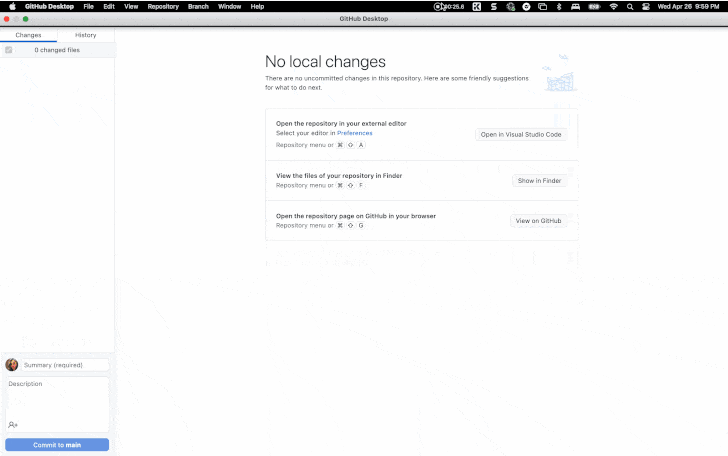
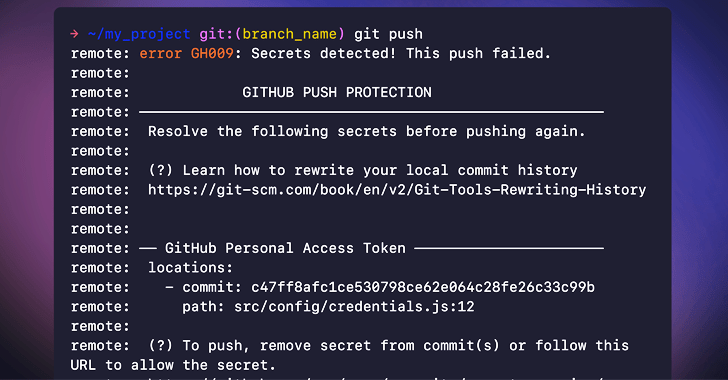
“When a solution is detected in code, builders are prompted specifically in their IDE or command line interface with remediation steerage to make certain that the solution is under no circumstances exposed.”
While push safety can be bypassed by delivering a purpose (e.g., screening, false optimistic, or acceptable risk), repository and organization directors and security professionals will be notified of this sort of gatherings by using email.
Upcoming WEBINARLearn to Quit Ransomware with True-Time Protection
Sign up for our webinar and understand how to stop ransomware attacks in their tracks with authentic-time MFA and company account protection.
Save My Seat!
To enable the selection, buyers can head to Configurations > Find “Code security and analysis” > Allow “Top secret scanning” and “Push security.”
Drive safety, due to the fact it went are living in April 2022 as a beta, is believed to have prevented 17,000 accidental top secret leaks, conserving additional than 95,000 several hours that would have otherwise been put in revoking, rotating, and remediating the compromised strategies, the corporation included.
The advancement arrives just about 5 months right after GitHub manufactured Magic formula scanning no cost for all community repositories, enabling users to be notified about leaked strategies in their repositories.
Observed this report interesting? Adhere to us on Twitter and LinkedIn to go through more exceptional material we post.
Some components of this write-up are sourced from:
thehackernews.com

 Google Announces New Privacy, Safety, and Security Features Across Its Services
Google Announces New Privacy, Safety, and Security Features Across Its Services