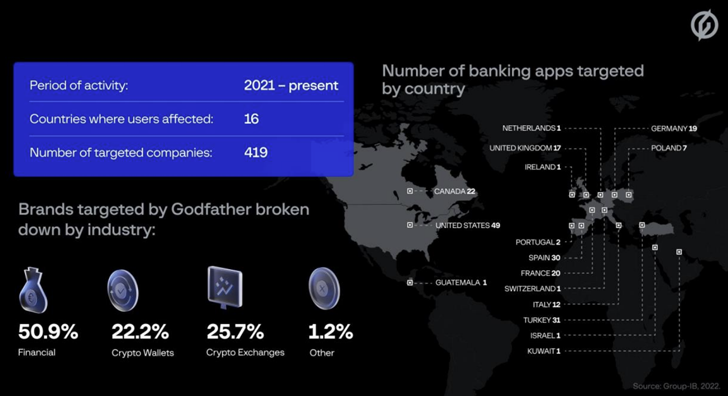
An Android banking trojan recognized as GodFather is getting utilised to target end users of extra than 400 banking and cryptocurrency applications spanning across 16 nations.
This contains 215 banking companies, 94 crypto wallet suppliers, and 110 crypto exchange platforms serving users in the U.S., Turkey, Spain, Italy, Canada, and Canada, among the other folks, Singapore-headquartered Group-IB stated in a report shared with The Hacker Information.
The malware, like a lot of financial trojans targeting the Android ecosystem, makes an attempt to steal user qualifications by making convincing overlay screens (aka web fakes) that are served atop goal purposes.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

First detected by Team-IB in June 2021 and publicly disclosed by ThreatFabric in March 2022, GodFather also packs in native backdoor attributes that permits it to abuse Android’s Accessibility APIs to document films, log keystrokes, capture screenshots, and harvest SMS and get in touch with logs.
Team-IB’s examination of the malware has exposed it to be a successor of Anubis, one more banking trojan that had its source code leaked in an underground forum in January 2019. It is also said to be distributed to other menace actors by way of the malware-as-a-company (MaaS) design.
The similarities between the two malware people extend to the system of obtaining the command-and-command (C2) tackle, implementation of C2 instructions, and the web pretend, proxy and screen seize modules. Nonetheless, audio recording and place tracking capabilities have been eradicated.
“Apparently, GodFather spares users in put up-Soviet nations around the world,” Team-IB claimed. “If the possible victim’s system choices involve a single of the languages in that location, the Trojan shuts down. This could advise that GodFather’s developers are Russian speakers.”
What helps make GodFather stand out is the actuality that it retrieves its command-and-regulate (C2) server handle by decrypting actor-controlled Telegram channel descriptions that are encoded employing the Blowfish cipher.
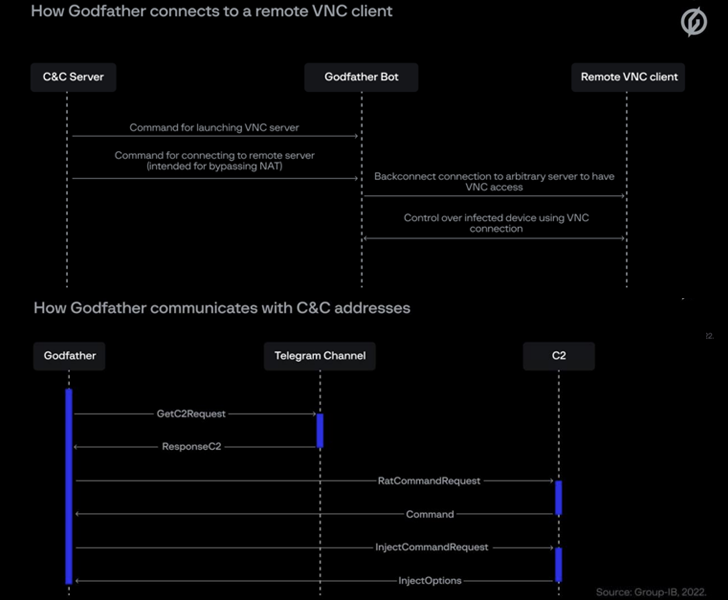
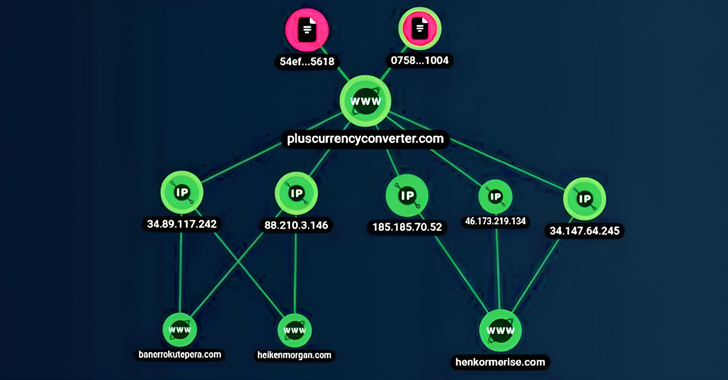
The exact modus operandi employed to infect user products is not regarded, though an evaluation of the risk actor’s command-and-control (C2) infrastructure reveals trojanized dropper applications as a person potential distribution vector.
This is dependent on a C2 address which is linked to an application named Forex Converter Additionally (com.furthermore.currencyconverter) that was hosted on the Google Participate in Retailer as of June 2022. The application in query is no lengthier obtainable for down load.
Yet another artifact examined by Group-IB impersonates the authentic Google Participate in Safeguard services that, upon currently being launched, results in an ongoing notification and hides its icon from the record of mounted purposes.
The conclusions occur as Cyble found out a variety of GodFather samples masquerading as the MYT Müzik application aimed at customers in Turkey.
GodFather is not the only Android malware centered on Anubis. Earlier this July, ThreatFabric disclosed that a modified edition of Anubis recognised as Falcon qualified Russian buyers by impersonating the condition-owned VTB Financial institution.
“The emergence of GodFather underscores the capability of risk actors to edit and update their instruments to maintain their performance in spite of endeavours by malware detection and prevention vendors to update their solutions,” Group-IB researcher Artem Grischenko explained.
“With a device like GodFather, risk actors are constrained only by their skill to create convincing web fakes for a certain software. Occasionally, the sequel actually can be much better than the unique.”
Located this write-up fascinating? Abide by us on Twitter and LinkedIn to examine far more unique content material we put up.
Some parts of this post are sourced from:
thehackernews.com

 Ransomware Hackers Using New Way to Bypass MS Exchange ProxyNotShell Mitigations
Ransomware Hackers Using New Way to Bypass MS Exchange ProxyNotShell Mitigations